Cyber Briefing: 2025.12.12
Active exploits hit Chrome and Gladinet as espionage groups expand, healthcare and legal breaches grow, MITRE flags top flaws, and the US targets Iranian hackers.
👉 What are the latest cybersecurity alerts, incidents, and news?
Welcome to Cyber Briefing, the newsletter that informs you about the latest cybersecurity advisories, alerts, incidents and news every weekday.
First time seeing this? Please Subscribe
🚨 Cyber Alerts
1. Attacks Exploit Gladinet Hard Coded Keys
Huntress has issued a warning regarding an actively exploited vulnerability in Gladinet’s CentreStack
2. Chrome Hit By Active Wild Exploit
Google has released a security update for its Chrome browser to fix three vulnerabilities, including a zero-day flaw that is currently being exploited in active attacks. The high-severity issue, tracked by the ID 466192044, involves a likely buffer overflow in the ANGLE graphics layer, and users are urged to update their browsers immediately.
3. WIRTE Uses Ashenloader To Install Ashtag
An advanced persistent threat, WIRTE, also known as Ashen Lepus, has been targeting government and diplomatic organizations across the Middle East since 2020 using new malware called AshTag, with a suspected operational expansion into Oman and Morocco from initial targets including the Palestinian Authority, Jordan, Iraq, Saudi Arabia, and Egypt. The actor, assessed to be active since at least 2018, is linked to the Gaza Cyber Gang and focuses on espionage, persistently continuing its campaign even through recent regional conflicts to deploy new malware variants and engage in hands-on activity.
For more alerts click here!
💥 Cyber Incidents
4. Law Firm Faces Major Data Breach
A Pittsburgh law firm, Davies, McFarland & Carroll, specializing in medical malpractice, suffered a data breach impacting the sensitive information of 54,712 individuals after an unauthorized network intrusion. The firm, a business associate of HIPAA-covered entities, had its network accessed by an unauthorized third party between May 19 and May 22, 2025, resulting in the viewing or acquisition of files containing protected health information.
5. Trizetto Warns Clients Of Data Breach
TriZetto Provider Solutions, a Cognizant company providing revenue management services, recently detected a cybersecurity incident involving unauthorized access to a web portal used by some of its healthcare clients. The access, which was first detected on October 2, 2025, but began in November 2024, compromised patient protected health information contained in historical eligibility transaction reports.
6. Awakenings Center Reports Data Breach
Loving and Living Center (Awakenings Center), a North Carolina-based counseling provider, discovered unauthorized access to its electronic medical records system around September 10, 2025, potentially affecting up to 17,800 patients. The exposed data included demographic information such as name, age, date of birth, gender, relationship status, employment status, city, and zip code, but no financial details were compromised.
For more incidents click here!
📢 Cyber News
7. MITRE Lists Top 25 Software Vulnerabilities
The MITRE Corporation released an updated Common Weakness Enumeration (CWE) Top 25 Most Dangerous Software Weaknesses list reflecting the latest changes in the threat landscape. Cross-site scripting (XSS) remained at the top of the list, followed by SQL injection and cross-site request forgery (CSRF).
8. Ex Accenture Employee Faces Cyber Fraud
A former government contractor manager has been charged by the Justice Department for lying about a cloud platform’s compliance with Department of Defense security requirements. Danielle Hillmer allegedly concealed the fact that the product did not implement necessary security controls, including those mandated by FedRAMP and the DoD Risk Management Framework, to obtain and maintain government contracts.
9. US Offers 10 Million Bounty For Hackers
The US government is offering a reward of up to $10 million for information on the Iranian hacking group now called Shahid Shushtari, an organization operating under the Islamic Revolutionary Guard Corps Cyber-Electronic Command (IRGC-CEC). The group has been linked to attacks on critical infrastructure sectors and influence operations, and the US has named Mohammad Bagher Shirinkar as its leader and Fatemeh Sedighian Kashi as a key employee.
For more news click here
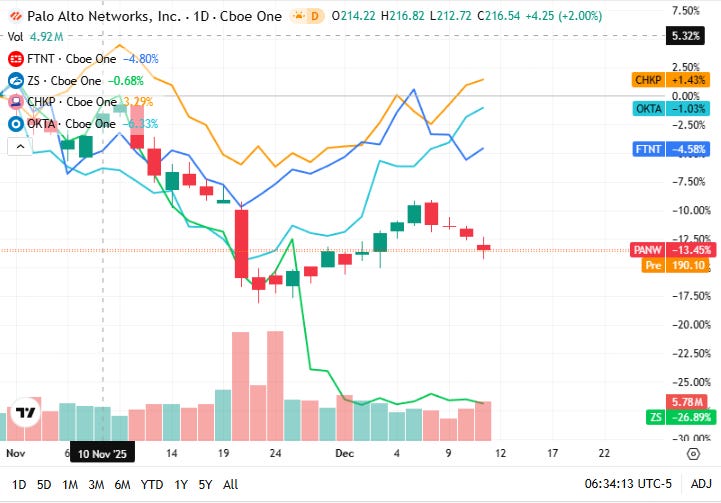
📈Cyber Stocks
On Friday, 12th December, cybersecurity stocks traded with mixed performance as defensive demand for cloud, identity and perimeter security remained steady amid broader market volatility. Ongoing focus on threat detection, compliance and zero-trust architectures supported select names, while profit-taking in parts of the tech sector kept gains measured.
Palo Alto Networks closed at 190.36 dollars and eased modestly, as investor caution around valuation and broader market softness outweighed ongoing confidence in its unified AI-driven security platform.
Fortinet closed at 82.47 dollars and edged higher, supported by sustained enterprise interest in zero-trust and network-security solutions even as macro headwinds kept broader sector performance in check.
Zscaler closed at 242.08 dollars and dipped slightly, reflecting light profit-taking after recent moves, though strong adoption of cloud-delivered security and zero-trust architectures continued to underpin long-term demand.
Check Point Software Technologies closed at 198.48 dollars and gained, driven by renewed investor interest in firewall and perimeter defenses amid elevated global cyber-threat activity.
Okta closed at 90.59 dollars and moved higher, buoyed by ongoing enterprise investment in identity and access management as organizations prioritise protection against identity-centric attacks.
💡 Cyber Tip
🌐 Chrome Hit by Active Exploit
Google has released urgent Chrome updates to fix three security flaws, including a high severity zero day that is being actively exploited. The issue appears to stem from a memory handling bug in Chrome’s graphics layer, which could allow attackers to crash the browser or potentially execute malicious code. Details are limited while users rush to patch.
🔐 What You Should Do
• Update Google Chrome immediately to the latest version
• Restart the browser after updating to apply fixes
• Keep automatic updates enabled on all browsers
• Update other Chromium based browsers like Edge, Brave, and Opera
• Avoid clicking unknown links until updates are applied
⚠️ Why This Matters
Browser zero days are a favorite entry point for attackers. Delaying updates leaves systems exposed to real world exploitation that can lead to malware infections or data theft. Fast patching is critical.
📚 Cyber Book
Hacked: The Secrets Behind Cyber Attacks by Dr Jessica Barker
Get book: https://amzn.to/450OhbE
💼 Cyber Jobs
Today’s 10 curated cybersecurity job openings:
🇺🇸 Datadog – Security Engineering Intern, New York, New York, United States – Apply
🇺🇸 Guidepost Solutions – Digital Investigator, New York, New York, United States – Apply
🇺🇸 AMC Networks – Security Ops Analyst I, Bethpage, New York, United States – Apply
🇺🇸 State Street – Cyber Security Operations Center (SOC) Analyst, Quincy, Massachusetts, United States – Apply
🇺🇸 Canus Tech – Security Analyst, Parsippany, New Jersey, United States – Apply
🇬🇧 La Fosse – Cyber Security Analyst, Birmingham, England, United Kingdom – Apply
🇬🇧 Experian – Cyber Defence Analyst, Nottingham, England, United Kingdom – Apply
🇬🇧 Best Job Tool – Cyber Security Analyst, United Kingdom – Apply
🇬🇧 Hack The Box – Join Hack The Box (Global), London, England, United Kingdom – Apply
🇬🇧 Network IT Recruitment Limited – Cyber Security Analyst, Birmingham, England, United Kingdom – Apply
If you know someone on the job hunt, share this with them!
📅 Cyber Events
Find global upcoming cybersecurity events here.
🇬🇧 TechEx Global 2026 – London, United Kingdom – February 4–5 – RSVP
🇺🇸 Aiken AI & Cyber Innovation Week 2026 – Aiken, South Carolina, United States – February 2–7 – RSVP
🇺🇸 SANS Rockville 2026 – Rockville, Maryland, United States – February 2–7 – RSVP
🇺🇸 Foundational Application of Social Engineering – United States – February 9–12 – RSVP
🇺🇸 Wild West Hackin’ Fest @ Mile High 2026 – Denver, Colorado, United States – February 10–12 – RSVP
🇬🇧 Fintech Week Dubai 2026 – Dubai, United Arab Emirates – February 17 – RSVP
🇺🇸 SANS Surge 2026 – United States – February 23–28 – RSVP
🇺🇸 GenAI Gala Dinner Convention 2026 – United States – February 24 – RSVP
🇺🇸 Cloud USA 2026 – United States – February 24 – RSVP
🇬🇧 RegTech Live 2026 – London, United Kingdom – February 26 – RSVP
That concludes today’s briefing. You can check the top headlines here!
Copyright © 2025CyberMaterial. All Rights Reserved.
Follow CyberMaterial on:
Substack, LinkedIn, Twitter, Reddit, Instagram, Facebook, YouTube, and Medium












Excellent roundup of today's threat landscape. The Chrome zeroday getting dropped so fast after discovery shows how quickly attackers are weaponizing vulns now. I've been tracking WIRTE's activity since early this year and their pivot into Oman/Morocco feels like a natural exansion given regional tensions. Interested to see if the 10M bounty on Iranian operators actually yields actionable intel or just symbolic.