Cyber Briefing: 2025.12.11
Teams vishing, Gogs zero day exploits, ransomware obfuscation, major data leaks, healthcare breaches, and global legal actions marked today’s cyber landscape.
👉 What’s trending in cybersecurity today?
Welcome to Cyber Briefing, the newsletter that informs you about the latest cybersecurity advisories, alerts, incidents and news every weekday.
First time seeing this? Please Subscribe
🚨 Cyber Alerts
1. Vishing Scam Via Teams Spreads Malware
A sophisticated vishing campaign uses Microsoft Teams and Quick Assist to socially engineer victims, leading to fileless deployment of multi-stage .NET malware through memory-based reflection.
2. Gogs Zero Day Hits Hundreds Of Servers
A high-severity unpatched security flaw in the Gogs Git service is currently being exploited, leading to the compromise of over 700 online instances. The vulnerability, tracked as CVE-2025-8110, is a file overwrite issue in the Gogs API that allows an attacker to gain SSH access and execute arbitrary code on the server, leveraging improper handling of symbolic links.
3. Ransom Gangs Use Shanya Packer To Hide
Multiple ransomware gangs are utilizing Shanya, a packer-as-a-service platform, to deploy payloads that disable endpoint detection and response solutions on victim systems by obfuscating their malicious code. Shanya emerged in late 2024 and has been observed in various countries, with ransomware groups like Akira, Medusa, Qilin, and Crytox confirmed to be using it.
For more alerts, click here!
💥 Cyber Incidents
4. Morton Drug Company Reports Data Breach
Morton Drug Company, a Wisconsin-based pharmacy serving long-term care facilities, recently suffered a security incident impacting its IT systems and the data of 40,051 individuals. The breach, detected around August 20, 2025, involved unauthorized network access and potential theft of patient information, including names, addresses, prescription details, and, for some, Social Security numbers.
5. Over 10,000 Docker Images Leak Keys
Over ten thousand Docker Hub container images were found to expose sensitive data, including live production credentials and LLM keys, affecting approximately one hundred organizations. These compromised secrets present critical risks for the impacted entities, which range from small businesses to a Fortune 500 company and a major national bank.
6. Cl0p Ransomware Hits Barts Health Data
The Cl0p ransomware group stole invoice data from a Barts Health NHS Trust database, affecting patients, staff, and suppliers. The trust is taking legal action to prevent further publication of the stolen information, which appeared on the dark web after an attack exploiting a vulnerability in Oracle E-business Suite.
For more incidents click here!
📢 Cyber News
7. Teams Will Warn Of Suspicious Traffic
Microsoft is developing a new security feature for Teams that will analyze traffic with external domains to assist IT administrators in addressing security threats. The “External Domains Anomalies Report,” as detailed in a Microsoft 365 roadmap update, is designed to help administrators protect their organizations without impeding legitimate communications.
8. Australia Enforces Teen Social Media Ban
Australia has enacted a landmark law, making it the first country to ban social media access for children under the age of sixteen, a move widely supported by parents and child advocates but opposed by major tech companies and free-speech groups. Starting at midnight, ten major platforms, including TikTok, YouTube, Instagram, and Facebook, must block minors or face significant fines of up to A$49.5 million under the new legislation, which is drawing international attention from regulators.
9. Ukrainian Hacker Aids Russian Groups
A Ukrainian national was charged by U.S. prosecutors for her alleged role in cyberattacks against global critical infrastructure, including U.S. water, election, and nuclear systems, carried out on behalf of Russian state-backed hacktivist groups. The individual, Victoria Eduardovna Dubranova, has been arraigned on charges related to two separate groups, to which she pleaded not guilty, with trials set for February and April 2026.
For more news click here
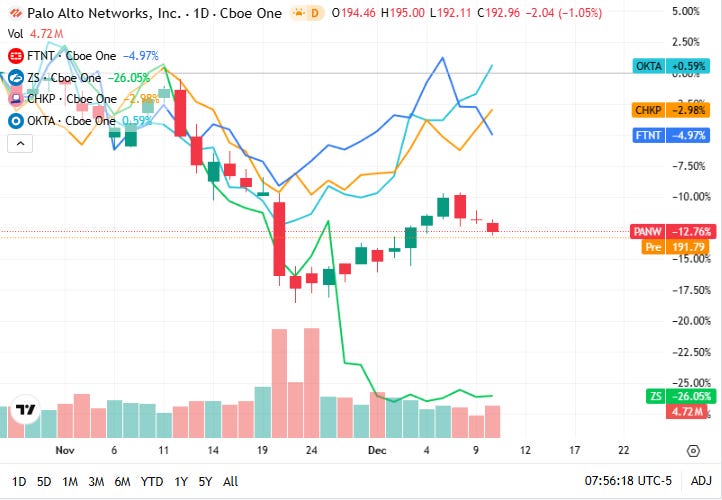
📈Cyber Stocks
On Thursday, 11th December, cybersecurity stocks showed mixed movement as investors balanced ongoing strength in sector demand against broader market volatility. Continued focus on cloud security, identity management and perimeter defense supported select names, while profit-taking and rotation into value sectors tempered gains elsewhere.
Palo Alto Networks closed at 192.96 dollars and eased modestly, reflecting cautious trading as investors weighed long-term confidence in platform-based AI security against near-term market headwinds.
Fortinet closed at 81.60 dollars and declined, with profit-taking and rotation pressure outweighing steady enterprise demand for zero-trust and network-security solutions.
Zscaler closed at 243.29 dollars and inched higher, supported by ongoing enterprise adoption of cloud-delivered security and zero-trust architectures despite broader market caution.
Check Point Software Technologies closed at 197.50 dollars and posted a solid uptick, driven by renewed interest in perimeter and firewall defenses amid rising global cyber threats.
Okta closed at 89.84 dollars and moved higher, buoyed by steady enterprise investment in identity and access management as organisations prioritise protection against identity-centric attacks.
💡 Cyber Tip
📞 Vishing Scam Via Teams Deploys Fileless Malware
Threat actors are impersonating IT staff on Microsoft Teams and convincing victims to launch Windows Quick Assist. Once remote access is granted, victims are redirected to a malicious site that delivers a trojanized updater program. The malware then decrypts and loads its payload directly into memory using .NET reflection, bypassing traditional file based detection.
🔐 What You Should Do
Never accept unsolicited Teams calls claiming to be from IT
Verify identity through official internal channels before granting remote access
Disable or restrict Quick Assist if not needed in your environment
Block unknown domains and monitor for unusual redirections
Deploy EDR that can detect memory injection and .NET runtime anomalies
Train staff to treat any surprise support request as a red flag
⚠️ Why This Matters
This attack blends social engineering, legitimate Windows tools, and fileless malware. Once memory based execution begins, most traditional defenses miss the intrusion entirely. Proactive verification and strong endpoint monitoring are critical defenses.
📚 Cyber Book
What To Do When You Get Hacked by Shimon Brathwaite
That concludes today’s briefing . You can check the top headlines here!
Copyright © 2025 CyberMaterial. All Rights Reserved.
Follow CyberMaterial on:
Substack, LinkedIn, Twitter, Reddit, Instagram, Facebook, YouTube, and Medium.