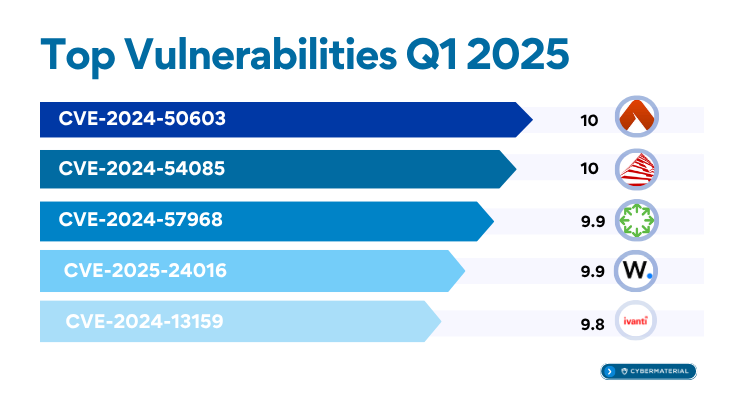
Top Vulnerabilities - Q1 2025
Q1 2025 saw major flaws in cloud and endpoint systems, with remote exploits requiring little to no authentication, letting attackers breach networks without crossing the perimeter.
Welcome back to Hall of Hacks Weekly!
The first quarter of 2025 brought a wave of critical security flaws affecting everything from cloud controllers to endpoint management systems. This quarter’s most dangerous vulnerabilities share the common theme of remote exploitation with minimal or no authentication required. Attackers are increasingly able to breach enterprise networks without needing to be inside the perimeter.
First time seeing this?
🚨 Critical Vulnerabilities Overview
During Q1 2025, the top vulnerabilities fell into several key categories. These included two remote OS command injection flaws, both rated at CVSS 10.0, which allow unauthenticated attackers to execute arbitrary system commands. Three authentication bypass vulnerabilities were discovered, enabling unauthorized access by exploiting weaknesses in login or access controls. Two unsafe deserialization bugs posed serious remote code execution risks through manipulated data objects. Lastly, four file upload and path traversal flaws increased the chances of sensitive data exposure or malicious code execution, highlighting the urgent need for improved input validation and access controls across enterprise systems.
⚡ The Highest-Rated Threats (CVSS 10.0)
CVE-2024-50603 – Aviatrix Controller
Unauthenticated attackers can inject shell metacharacters into API parameters, allowing arbitrary OS command execution on cloud infrastructure. With a 94.35% EPSS score, exploitation is likely imminent.
CVE-2024-54085 – AMI SPx BMC Firmware
A Redfish Host Interface flaw allows remote authentication bypass, providing attackers with full system access and control over device firmware. This directly threatens confidentiality, integrity, and availability at the hardware level.
🧩 Unsafe Deserialization Risks
CVE-2025-24016 – Wazuh Distributed Architecture
A flaw in JSON deserialization enables remote code execution through crafted objects. This vulnerability (CVSS 9.9, EPSS 91.65%) affects Wazuh's centralized logging and threat detection systems, posing risks of widespread compromise in SOC environments.
📁 File Upload & Path Traversal
CVE-2024-57968 – Advantive VeraCore
An authenticated user can upload files to unintended directories. If chained with other flaws, this can result in arbitrary code execution or data leakage.
CVE-2024-13159 – Ivanti Endpoint Manager (EPM)
This absolute path traversal bug allows unauthenticated access to sensitive files. Multiple related CVEs (13159–13161) all carry CVSS 9.8+ and EPSS scores over 90%, underscoring their danger.
CVE-2025-24813 – Apache Tomcat
A path equivalence flaw allows attackers to bypass normal protections. Public exploits already exist, increasing the urgency for patching.
🔓 Authentication Bypasses Surge
Fortinet FortiOS & FortiProxy
Multiple CVEs (e.g., CVE-2025-55591, CVE-2025-24472) allow attackers to escalate privileges to super-admin through alternate paths, including websocket modules and specially crafted proxy requests.
📊 Threat Intelligence Snapshot
2 CVEs scored 10.0 CVSS and >90% EPSS, marking them as urgent, high-likelihood threats.
5 vulnerabilities had public exploits available within days of disclosure.
ICS/OT systems are increasingly affected, exposing critical infrastructure to remote compromise.
Input sanitization, authentication logic, and access control weaknesses were recurring causes.
🔐 Key Takeaways for Defenders
This quarter's top vulnerabilities reveal clear priorities for defenders. CVEs with high CVSS and EPSS scores, especially those with public exploits or EPSS above 90 percent, should be patched immediately.
Many attacks exploited weak authentication paths, so enforcing MFA and disabling unused modules is critical. Deserialization flaws like Wazuh’s highlight the need for strict JSON and XML validation.
With file upload risks on the rise, teams must validate file types and isolate upload directories. Monitoring EPSS trends can help prioritize threats that attackers are actively targeting.
📌 Coming Next Week
Hall of Hacks will release the Most Vulnerable Vendors of Q1 2025.
We’ll break down which vendors were hit hardest in the first quarter, what made them vulnerable, and what it means for enterprise risk and supply chain security.
Subscribe and Comment.
Copyright © 2025 CyberMaterial. All Rights Reserved.
Follow CyberMaterial on:
Substack, LinkedIn, Twitter, Reddit, Instagram, Facebook, YouTube, and Medium.