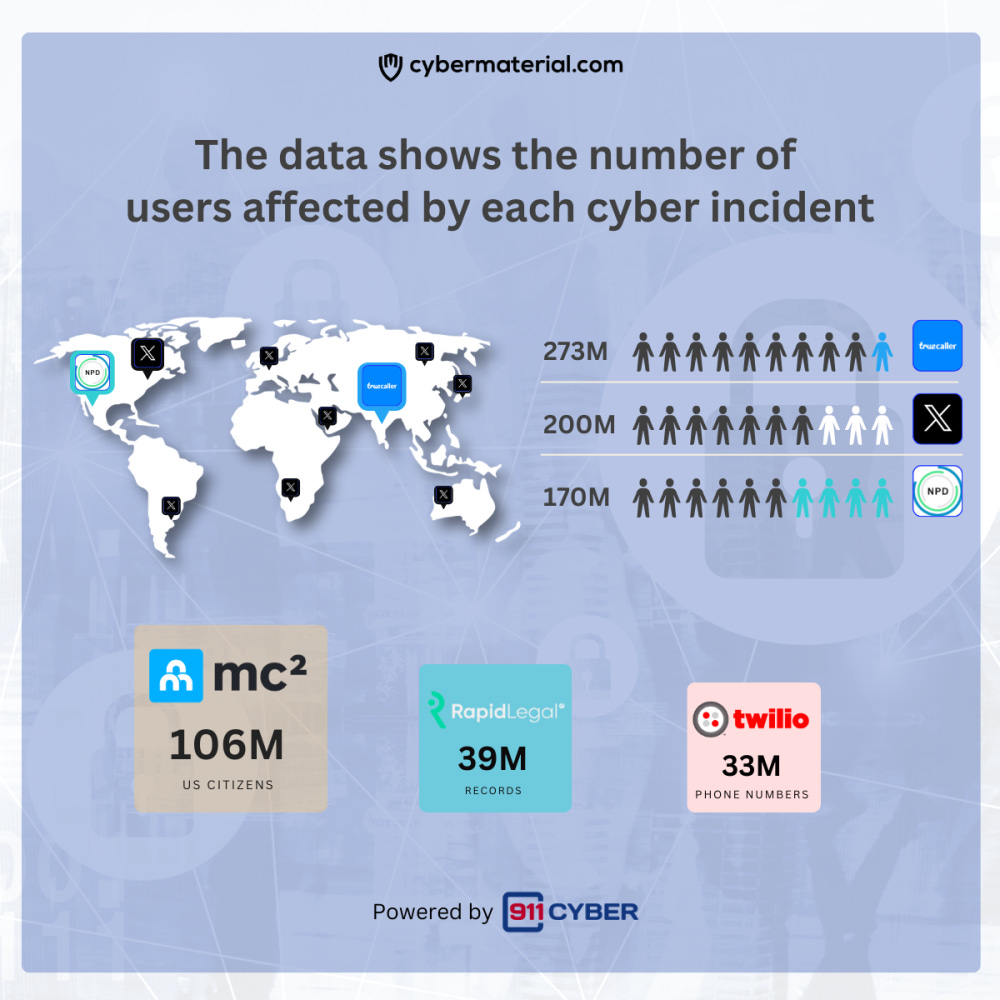
Top Victims Q3 2024
Q3 2024 saw major breaches at Truecaller, X, NPD, and Twilio, exposing billions of records and highlighting urgent gaps in data protection, third-party risk, and breach response strategies.
Welcome back to our latest edition of Hall of Hacks Weekly! In the third quarter of 2024, we saw some of the most significant data breaches and cybersecurity incidents, highlighting the broader implications for industries worldwide.
First time seeing this?
Key Data Breaches in Q3 2024
Q3 2024 has witnessed numerous high-profile cyber incidents, affecting millions of users globally. Here’s an overview of the top victims during this period:
Truecaller: A massive data breach compromised the personal information of approximately 273 million Indian users, making it one of the largest incidents for the quarter.
X (Twitter): 200 million users were affected by an extensive data breach that exposed sensitive data, highlighting ongoing security challenges in social media platforms.
National Public Data (NPD): A staggering breach resulted in the exposure of 2.9 billion records, affecting 170 million US users.
MC2: This breach compromised sensitive data from 100 million US citizens, highlighting major flaws in data security and handling practices.
Twilio’s Authy app: 33 million phone numbers were stolen by infiltrating the authentication services.
Rapid Legal Services Company: Approximately 39 million legal records were leaked online, reflecting the critical nature of securing private legal documents.
Incident Aftermath
Each of these breaches has its own complex aftermath involving legal actions, mitigation efforts, and the broader impact on stakeholders:
Truecaller:
Legal and Regulatory Actions: Truecaller has not faced fines or penalties as they maintained that no new breach occurred. The company is under regulatory scrutiny, particularly with international data protection authorities.
Mitigation and Response: Truecaller conducted an internal investigation which they claim found no evidence of a breach. Their response has focused on reassuring users and monitoring for potential misuse of data.
Data Misuse and Impact: There is no specific evidence of misuse of the exposed data from this alleged breach. The potential risk includes identity theft and spam, which remains a concern for the affected users.
X (formerly Twitter)
Legal and Regulatory Actions: Ongoing investigations by European and U.S. regulators are examining the breach, though no new fines have been imposed specifically for this incident.
Mitigation and Response: X claims the exposed data was due to a previously addressed vulnerability and not a new breach. The company has not issued widespread new notifications to users, focusing instead on general security advisories.
Data Misuse and Impact: The exposed data primarily includes email addresses, increasing risks of phishing and spam. The full impact on user privacy and trust is still being assessed.
National Public Data (NPD)
Legal and Regulatory Actions: NPD faced severe legal consequences, including multiple class-action lawsuits and significant regulatory scrutiny, leading to its closure.
Mitigation and Response: The company acknowledged the breach late and was eventually forced to shut down due to financial insolvency, influenced by legal pressures.
Data Misuse and Impact: The exposure of 2.9 billion records poses extensive risks of identity theft and fraud, significantly impacting personal data security.
MC2
Legal and Regulatory Actions: Legal scrutiny from consumer rights attorneys and possible class-action lawsuits are focusing on potential violations of data protection laws.
Mitigation and Response: MC2 secured the exposed database but has been criticized for its slow initial response and lack of transparency with affected individuals.
Data Misuse and Impact: The leaked data includes comprehensive personal profiles, posing high risks of identity theft and financial fraud, highlighting the need for enhanced security practices in data handling.
Twilio’s Authy App
Legal and Regulatory Actions: At least one legal investigation has been launched, examining potential failures in securing sensitive user data.
Mitigation and Response: Twilio secured the affected API immediately upon discovery of the breach and has been proactive in advising users on security enhancements.
Data Misuse and Impact: The stolen phone numbers could be used for phishing attacks, impacting user security. Ongoing risks include SIM swapping and targeted social engineering attacks.
Rapid Legal Services Company
Legal and Regulatory Actions: No specific fines have been reported, but the company faces potential legal challenges due to the sensitive nature of the exposed data.
Mitigation and Response: The company responded quickly by securing the exposed database and is likely reviewing its security protocols to prevent future incidents.
Data Misuse and Impact: Although there is no confirmed misuse of the data, the exposure of legal records poses risks of privacy violations and could undermine client confidentiality.
Emerging Threats and Vulnerability Points
As we analyze the breaches of Q3 2024, it's clear that cybercriminals are exploiting new vulnerability points, particularly in cloud storage and third-party service integrations. For example, the breach involving Twilio's Authy app was primarily due to compromised third-party services. These incidents highlight the need for enhanced security measures such as end-to-end encryption and more robust identity and access management systems.
Organizations should also focus on educating their employees about phishing and other common tactics used by attackers, as human error continues to be a major factor in many breaches.
Cybersecurity Best Practices for Users
To counter the growing cyber threats, here are some actionable steps users can take to protect their personal information:
Password Management: Use complex passwords and consider a reputable password manager to keep track of different accounts securely.
Multi-factor Authentication (MFA): Always enable MFA where available to add an extra layer of security beyond just a password.
Software Updates: Keep all devices and applications up-to-date to protect against vulnerabilities that could be exploited by hackers.
Phishing Awareness: Be vigilant about emails and messages from unknown sources and avoid clicking on suspicious links or downloading attachments from untrusted sources.
Regular Backups: Ensure that data is backed up regularly, so in the event of a data breach or ransomware attack, you can restore your information from a secure backup.
6. Keep track of your digital footprint: Regularly monitor your digital footprint and update security settings to minimize risks from data breaches.
As we’ve seen in Q3 2024, cybersecurity is a shared challenge that requires a unified approach. No sector is immune from cyber threats, hence by adopting these best practices, users can significantly reduce their vulnerability to cyberattacks and safeguard their personal and sensitive data. Stay vigilant, stay informed, and as always, stay secure.
Need help safeguarding your business? Click here
Coming Next Week
Next week, we’ll delve into the Top Regulations of Q3 2024. Stay informed and protect your organization by subscribing to our weekly newsletter, providing you with the latest updates and expert analyses in cybersecurity.
📥 Want to read the full document now? Download here
Subscribe and Comment
Copyright © 2025 CyberMaterial. All Rights Reserved.
Follow CyberMaterial on:
Substack, LinkedIn, Twitter, Reddit, Instagram, Facebook, YouTube, and Medium.