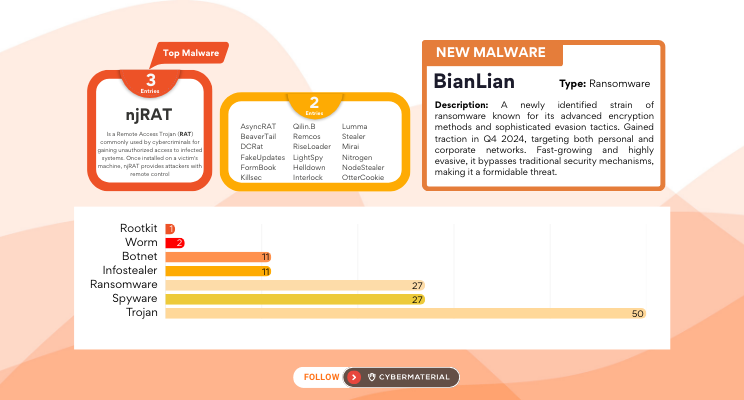
Top Threats - Q4 2024
Q4 2024 saw a surge in RaaS, MaaS, mobile malware, and social engineering campaigns. Major disruptions like Operation Magnus marked a turning point in the fight against advanced cyber threats.
Welcome back to Hall of Hacks Weekly
In this issue, we uncover the most significant threats that shaped the global cyber landscape in Q4 2024. From ransomware evolutions to mobile surveillance malware and nation-state espionage, these threats reveal the evolving tactics and global scope of cybercriminal operations.
First time seeing this?
Overview: A Season of Sophisticated Threats
Q4 2024 brought a surge of sophisticated cyber threats spanning ransomware, trojans, spyware, and botnets. Cybercriminals ramped up operations with highly evasive malware, widespread phishing campaigns, and exploitation of both mobile and IoT platforms. Coordinated law enforcement actions like Operation Magnus marked progress, but new variants and campaigns continued to escalate the stakes.
Dominant Malware Families and Campaigns
Ransomware Still Reigns
Ransomware remained the most pervasive threat in the last quarter of 2024, with over 20 active groups using encryption, extortion, and stealth to disrupt systems across industries and platforms.
Qilin.B, PlayCrypt, RansomHub, Interlock, Sarcoma, Helldown, and Beast delivered attacks targeting Windows, Linux, and ESXi systems.
Emerging variants like Qilin.B and BianLian introduced stronger encryption and stealth mechanisms.
Prince Ransomware and others exploited niche systems like FreeBSD and used phishing baits like Royal Mail delivery scams to spread.
Spyware and Infostealers Surge
RedLine and MetaStealer were central to the Operation Magnus takedown, which dismantled over 1,200 servers used for credential theft.
North Korean-linked BeaverTail, SpyMax, and OtterCookie deployed targeted surveillance against organizations and developers.
Malware like CloudScout Toolset, NodeStealer, and CoinLurker expanded campaigns to steal session cookies, browser credentials, and cryptocurrency wallet data.
Mobile Threats Escalate
FakeCall malware for Android evolved to hijack outgoing calls to banks, mimicking call UIs and enabling voice phishing (vishing) attacks.
LightSpy, DroidBot, and NoviSpy targeted iOS and Android users with advanced features like real-time mic and camera surveillance.
Over 200 malicious apps were flagged across third-party and official app stores.
Botnets and IoT Exploits
Mirai, Prometei, Quad7, Ngioweb, and Matrix botnets were used for global DDoS attacks, credential theft, and IoT proxy network exploitation.
These botnets took advantage of default credentials and unpatched routers.
Social Engineering and Supply Chain Attacks
FakeUpdate campaigns tricked users into downloading malware disguised as browser or app updates from compromised websites.
The Contagious Interview campaign lured victims via fake job interviews and dropped malware like OtterCookie and BeaverTail through npm packages and video apps.
GodLoader abused the Godot gaming engine to stealthily distribute malware through developer ecosystems.
Evasion and Obfuscation Tactics
Threat actors significantly advanced their stealth techniques to bypass detection mechanisms. Tools like HeartCrypt, a Packer-as-a-Service, allowed cybercriminals to obfuscate malware and evade analysis. Meanwhile, AsyncRAT was deployed alongside ScreenConnect to establish persistent and covert remote access to victim systems. Additionally, the emergence of PUMAKIT, a sophisticated Linux rootkit, demonstrated how attackers are now leveraging low-level stealth tactics to avoid endpoint detection and maintain long-term access.
State-Sponsored Activity: North Korea and China
Q4 of 2024 saw major activity from nation-state APT groups:
North Korean threat actors deployed OtterCookie, VeilShell, FASTCash, and RustDoor in campaigns to steal crypto, impersonate recruiters, and exfiltrate sensitive data.
China-linked GHOSTSPIDER targeted telecoms with espionage malware.
South Korea and the U.S. issued sanctions and indictments against key individuals tied to these campaigns.
Why These Threats Matter
The threats in the fourth quarter demonstrated a clear evolution in the cybercrime landscape, marked by the rapid expansion of malware-as-a-service ecosystems and the increasing convergence of mobile, IoT, and cloud-based attack vectors. Social engineering became more deeply integrated into malware delivery, with campaigns leveraging fake job offers, phishing, and deceptive apps to infiltrate systems. At the same time, a growing wave of cross-platform malware emerged, capable of targeting both consumer and enterprise environments, further blurring the lines between personal and organizational cybersecurity risks.
Security teams are urged to:
Monitor and block info-stealer infrastructure
Educate users against phishing and fake job lures
Update protections across IoT, mobile, and VPN endpoints
Track the rise of nation-state APTs and ransomware-as-a-service operations
Emerging Threats to Watch
Emerging threats in Q4 2024 showcased increasingly deceptive and versatile attack methods. Exploits targeting Session Smart Routers delivered new variants of the Mirai botnet, while FakeCaptcha attacks used spoofed security prompts to inject infostealers. Meanwhile, updated versions of njRAT, Remcos, and DarkGate were spread through Microsoft Teams chats and malicious Excel macros, blurring the lines between business tools and malware delivery. Additionally, smishing campaigns and WhatsApp-based threats like PixPirate targeted users’ financial data through social messaging platforms, marking a significant rise in mobile-focused cybercrime.
Coming Next Week
Next week, we’ll release the full Q4 2024 Cybersecurity Threat Report, packed with detailed insights into the good, the bad, and the ugly of the quarter. From major takedowns to emerging threats, this comprehensive document will give you a clear picture of what shaped the global cybersecurity landscape and what to prepare for next.
Copyright © 2025 CyberMaterial. All Rights Reserved.
Follow CyberMaterial on:
Substack, LinkedIn, Twitter, Reddit, Instagram, Facebook, YouTube, and Medium.