Top Threat Actors - Q2 2025
Global law enforcement cracked down hard in Q2 2025, arresting ransomware actors, fraud rings, and dark web criminals worldwide.
Welcome back to Hall of Hacks Weekly
The second quarter of 2025 brought a shifting threat landscape with familiar ransomware names reasserting dominance, state-linked APTs surfacing in new regions, and hacktivists keeping pressure tied to geopolitical conflicts. We tracked hundreds of incidents tied to dozens of unique actors, underscoring the fractured but relentless cyber battlefield.
First time seeing this?
🌍 A Look at the Global Threat Landscape
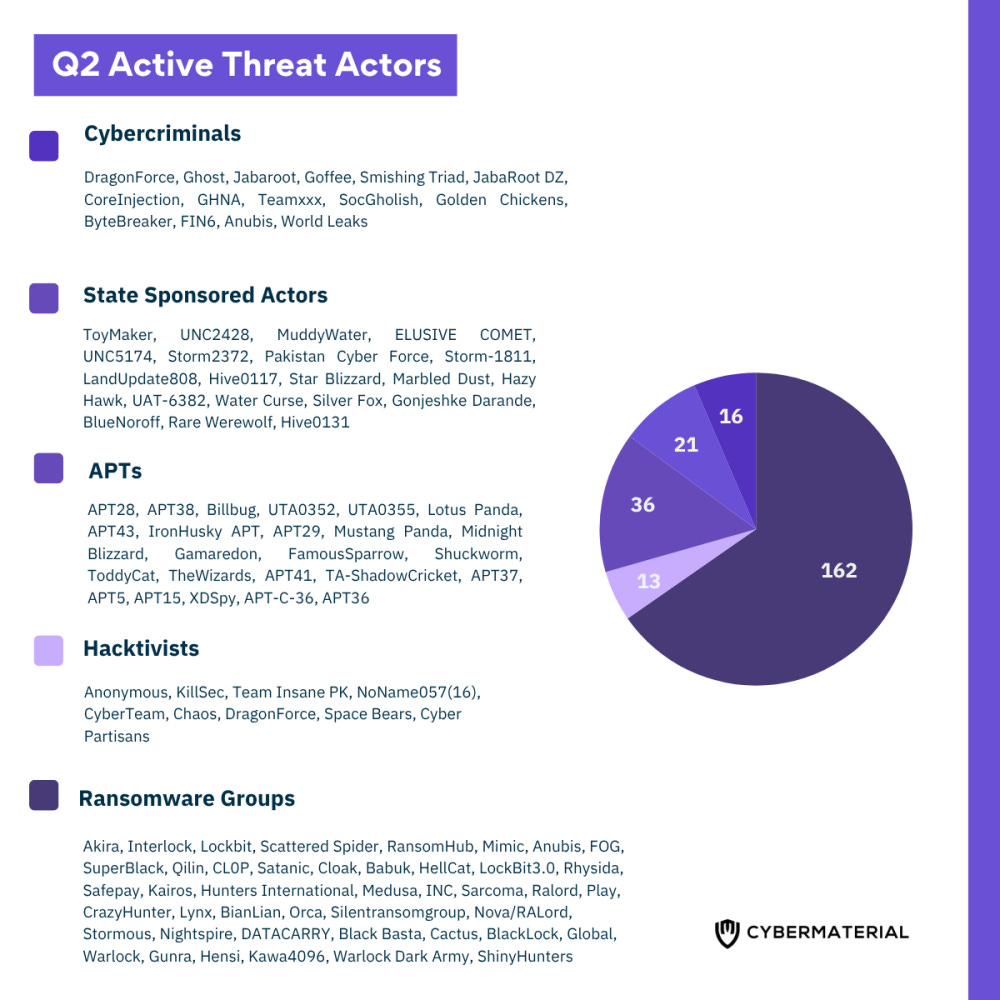
From ransomware extortion to espionage and political hacktivism, Q2 2025 revealed a fractured but relentless threat ecosystem. The quarter’s activity involved:
160+ ransomware groups
36 advanced persistent threat (APT) actors
21 state-sponsored operations
16 cybercriminal organizations
13 hacktivist collectives
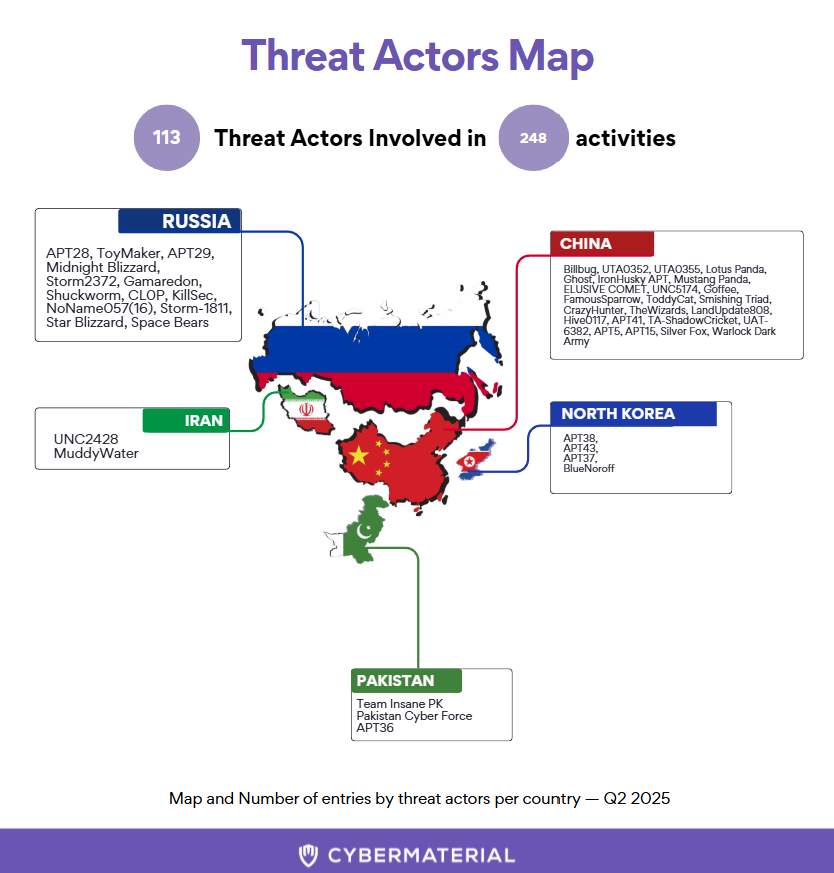
Activity stretched across multiple regions, including Russia, China, North Korea, Malaysia, Algeria, Pakistan, and Israel, alongside unattributed campaigns.
🇷🇺 Russia’s Cyber Front
Russia remained highly active in Q2, with multiple ransomware, hacktivist, and cybercriminal groups driving operations across sectors. Key Russian-affiliated actors this quarter included NoName057(16), KillSec, and Space Bears, all of which continued to launch politically motivated or financially driven campaigns targeting Europe and beyond.
🇨🇳 China Expands Cyber Attacks Operations
Chinese-origin groups weren’t just espionage-focused this quarter. In addition to APT41 and APT5, the data also lists the cybercriminal group Ghost, highlighting China’s presence beyond traditional APTs. Their activity spanned telecoms, defense, and government portals, often disguised as political protest.
Notable Chinese actors active this quarter: APT41, APT5, Silver Fox, TA-ShadowCricket, and the new threat actor Warlock Dark Army
🇮🇷 Iran Keeps Its Presence
Iranian-linked groups maintained a lower but steady tempo in Q2, with ransomware-adjacent efforts surfacing in data theft and influence campaigns. UNC2428 and MuddyWater were the key espionage-focused actors observed during the quarter.
🇰🇵 North Korea’s Cyber Campaigns
North Korean activity stood out with 11 Entries. Key ones included APT38, APT43, and APT37, as well as BlueNoroff. Their campaigns focused heavily on cryptocurrency theft, banking intrusions, and financially motivated espionage, underscoring North Korea’s continued reliance on cyber operations as a revenue source.
🧱 Ransomware: Akira Rules, Safepay Rises
Ransomware once again led the quarter by volume. Akira was the single most active group, responsible for 49 incidents, far ahead of any competitor. The group also spawned a wide array of smaller affiliates and splinters such as ByteBreaker, Nightspire, Nova/RALord, Silentransomgroup, DATACARRY, and more.
Other notable ransomware groups included:
Safepay – 20 incidents
Qilin – 14 incidents
Interlock – 7 incidents
INC – 7 incidents
Additional recurring but smaller actors included Rhysida, Hunters International, Medusa, HellCat, Sarcoma, Cloak, and Play, each maintaining activity across diverse sectors.
🕶️ APTs Keep Pressure On
APT groups remained steady with 36 entries, continuing to focus on espionage and infiltration. Notable examples this quarter included:
APT36
APT37
APT41
APT15
APT-C-36
TA-ShadowCricket
These actors targeted governments, telecoms, and sensitive industries, often blending espionage with financially motivated operations.
⚔️ Hacktivist Fronts Stay Loud
Hacktivist groups remained a visible presence in Q2, with 13 collectives identified. While many of their campaigns were symbolic or disruptive rather than destructive, they still drew significant attention. Active groups included NoName057(16), DragonForce, Team Insane PK, Anonymous, Chaos, KillSec, and Cyber Partisans, each contributing to the ongoing wave of politically and ideologically motivated cyber activity.
💻 Cybercriminal Syndicates
Beyond ransomware, 16 cybercrime organizations were tracked. Groups such as Golden Chickens, Smishing Triad, and SocGholish pushed phishing, malware, and fraud operations. Their work often overlapped with ransomware affiliates, blurring lines between categories.
🚨 Spotlight on: Akira
The most active actor of Q2.
Type: Ransomware-as-a-Service (RaaS)
Activity Count: 49 incidents
Notable Targets: Government, healthcare, and financial sectors across Europe and North America
Akira’s model has clearly overtaken LockBit, cementing its role as the top ransomware operator in 2025.
🔍 Key Trends to Watch
Affiliate Splintering: Akira-linked offshoots (ByteBreaker, Nova/RALord, etc.) highlight how easily affiliates rebrand to evade detection.
Safepay & Qilin Growth: These groups are filling some of the vacuum left by LockBit’s decline.
APT–Ransomware Blending: Several APTs appeared in ransomware-linked activity, complicating attribution.
Regional Expansion: Increased entries tied to North Africa, South Asia, and Southeast Asia.
Persistent Hacktivism: Groups like NoName057(16) and DragonForce keep politically motivated disruption in the mix.
🧩 Why This Matters
Ransomware remains the most dominant threat even after repeated takedowns, with Akira showing how affiliates quickly adapt and persist. Defense is further complicated by attribution gaps, as many groups rebrand or use mixed infrastructure to obscure their identities. At the same time, geopolitical tensions are directly shaping cyber operations, from Russia’s campaigns to China’s hacktivist activity.
📌 Coming Next Week
Hall of Hacks – Top Cyber Threats of Q2 2025
We’ll break down the vulnerabilities, exploits, and most targeted industries of this quarter, helping defenders prepare for what’s next
Subscribe and Comment.
Copyright © 2025 CyberMaterial. All Rights Reserved.
Follow CyberMaterial on:
Substack, LinkedIn, Twitter, Reddit, Instagram, Facebook, YouTube, and Medium.