Top Threat Actors - Q1 2025
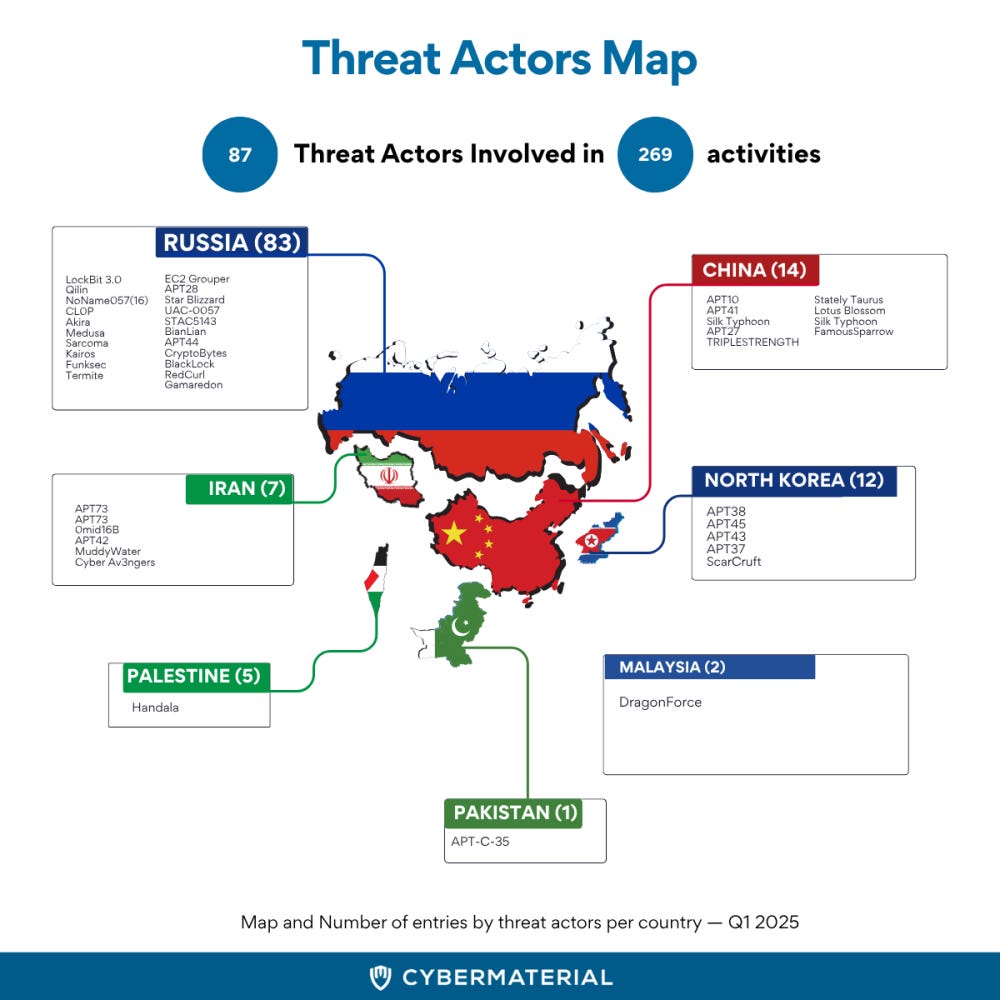
Q1 2025 saw 269 cyber incidents linked to 87 threat actors, from espionage units to ransomware crews. The threat landscape intensified as new and persistent adversaries clashed in a global cyber arena
Welcome back to Hall of Hacks Weekly
The first quarter of 2025 was packed with familiar names, fresh adversaries, and a relentless pace of global cyber activity. We tracked 269 incidents tied to 87 unique threat actors, ranging from sophisticated espionage groups to ransomware gangs and hacktivists. The cyber battlefield grew more complex, with new players jumping in and old ones refusing to go away.
First time seeing this?
🌍 A Look at the Global Threat Landscape
From coordinated ransomware attacks to targeted state-backed campaigns, Q1 2025 confirmed one thing: threat actors are multiplying, and they’re getting smarter. The quarter's activity involved:
41 ransomware groups
13 advanced persistent threat (APT) actors
4 hacktivist collectives
30 cybercrime organizations
These actors originated from over a dozen countries, though a large portion of activity couldn’t be clearly attributed to a nation-state. Russia, China, North Korea, and Iran led the pack in state-aligned operations, while most ransomware and cybercriminal activity came from uncertain or deliberately masked origins.
🇷🇺 Russia Still Dominates the Scene
Russia was behind at least 83 of the 269 recorded cyber activities this quarter. Its arsenal included powerful ransomware groups like LockBit 3.0, Akira, and Medusa, along with APTs like APT28 and Star Blizzard. These groups hit targets across Europe, Asia, and North America, focusing on finance, healthcare, and government systems.
Key Russian-affiliated actors this quarter included: LockBit 3.0, Sarcoma, Funksec, STAC5143, CryptoBytes, APT44, Kairos
🇨🇳 China Maintains Focus on Espionage
Chinese APTs launched 14 recorded campaigns, mostly aimed at intelligence collection and long-term network access. Groups like APT41, APT10, and Silk Typhoon continued targeting sectors like telecom, defense, and biotech.
Notable Chinese groups active this quarter: APT41, Silk Typhoon, Lotus Blossom, Stately Taurus, TRIPLESTRENGTH
🇮🇷 Iran’s Cyber Arm Keeps Pushing
Iranian actors remained active and aggressive, with 7 operations attributed to government-linked APTs. These campaigns leaned heavily into infrastructure disruption and data theft, with energy and public sector targets in Europe and the Middle East. Iran-Linked Hackers Target UAE Organizations with New Sosano Malware Campaign
Key Iranian threat actors this quarter:APT42, MuddyWater, Cyber Av3ngers, 0mid16B
🇰🇵 North Korea’s Financial Focus
North Korean cyber units focused largely on financially motivated attacks, including cryptocurrency thefts, banking intrusions, and targeting Web3 developers with fake job opportunities. Groups like APT38, APT43, and ScarCruft were all active, executing stealthy campaigns designed to quietly extract value while maintaining plausible deniability.
Ransomware: The Most Crowded Field
Ransomware groups led in volume and visibility. FOG was the most active threat actor this quarter, with 44 recorded operations across multiple regions. Other prolific players included RansomHub, 8Base, Everest, and Akira. The ransomware landscape grew more fragmented, with dozens of newer groups using repurposed malware from LockBit and others.
Top ransomware groups of Q1 2025: FOG, RansomHub, Qilin, CL0P, Hellcat, Termite, Medusa, Funksec, Everest
APTs Keep Steady Pressure
Advanced persistent threat groups remained a serious concern, especially those from Russia, China, and North Korea. These actors focused on long-term access, surveillance, and the exfiltration of sensitive data.
Key APTs this quarter: APT10, APT28, APT42, APT-C-35, Stately Taurus
Hacktivist Activity on the Rise
Cyber activism surged in early 2025, often tied to geopolitical conflicts. Pro-Russian group NoName057(16) led a wave of politically motivated DDoS attacks in Europe. Others like Nam3L3ss, XakNet, and DXPLOIT targeted news outlets, government portals, and financial institutions.
Attribution Gets Murkier
Of the 269 recorded events, 139 were linked to actors with unknown or unclear affiliations. These groups operate in the shadows, often mimicking others or using tools from multiple ecosystems to avoid detection.
Notable unclassified groups: 8Base, Everest, InterLock, Safepay, Abyss, CoreInjection, EncryptHub, Dark Storm Team, Stargazer Goblin
🚨 Spotlight on: FOG
FOG was the most active threat actor of the quarter.
Type: Ransomware
Activity Count: 44 incidents
Notable Targets: Manufacturing, energy, and healthcare across North America and Europe
Origin: Unknown
Despite being relatively new, FOG has quickly adopted a high-impact, high-volume strategy and is believed to be operating with advanced tooling and dark web alliances.
🔍 Key Trends to Watch
More Hybrid Threats: Groups are blending espionage, data theft, and ransomware in single campaigns.
Tool Sharing & Malware Recycling: The LockBit 3.0 leak has seeded dozens of offshoots and lookalike strains.
Attribution Challenges: Threat actors are getting better at hiding their origins using mixed infrastructure and global proxy networks.
Healthcare & Defense Targeting: There was a clear uptick in campaigns against hospitals, biotech firms, and defense contractors.
Geopolitical Spillovers: Offline wars are being mirrored online, especially in Eastern Europe and the Middle East.
📌 Coming Next Week
Hall of Hacks – Top Cyber Threats of Q1 2025
From the most exploited vulnerabilities to the most targeted sectors, we’ll break down the biggest digital dangers organizations faced in early 2025, and what defenders need to prepare for next.
Subscribe and Comment.
Copyright © 2025 CyberMaterial. All Rights Reserved.
Follow CyberMaterial on:
Substack, LinkedIn, Twitter, Reddit, Instagram, Facebook, YouTube, and Medium.