Top Incident Impact - Q1 2025
Over 3.6B records were breached in Q1 2025. Ransomware, supply chain attacks, and crypto theft surged, hitting sectors from healthcare to defense.
Welcome back to Hall of Hacks Weekly!
This quarter, data breaches surged to catastrophic levels, with billions of records leaked and sensitive systems compromised across the globe. From mega-platforms like Twitter/X to blood banks and national defense institutions, the first quarter of 2025 has spared no one.
First time seeing this?
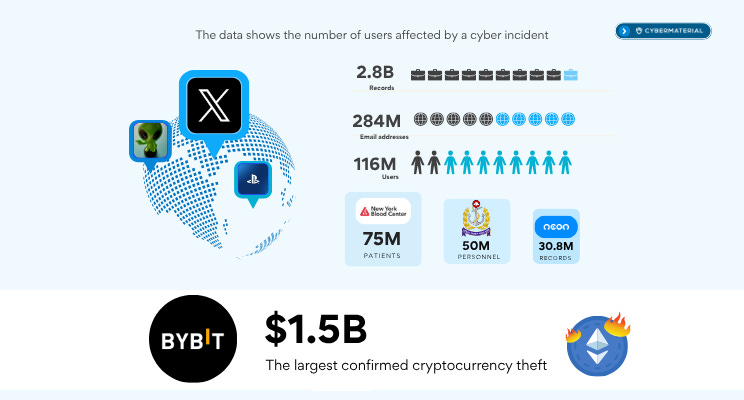
🧵 Top Data Breaches of Q1 2025
📌 Twitter/X – Nearly 2.87 billion records were exposed in one of the largest single-platform leaks to date. This includes full names, email addresses, usernames, and follower counts.
📌 ALIEN TXTBASE Stealer Logs – Leaked 287 million unique email entries harvested via infostealers, showcasing the industrial scale of credential theft.
📌 PlayStation – A breach affecting 116 million global accounts included login credentials and user behavior data, signaling a major threat to the gaming sector.
📌 New York Blood Center – Over 75 million records, including health, donation, and PII data, were compromised.
📌 Bangladesh Navy – Sensitive defense systems were reportedly infiltrated in a sophisticated cyberattack that compromised national security infrastructure and affected 50 million service members.
📌 Neon (Banco Neon) – A breach at the Brazilian digital bank exposed 30.8 million records, underscoring the growing risk to fintech platforms and financial services across Latin America.
Record-Breaking Cryptocurrency Theft
💸Bybit Crypto Exchange reported a staggering $1.5 billion loss in Ethereum due to wallet compromises and token transfer manipulation, making it one of the largest digital heists in recent memory.
🎯 Key Insights & Trends
Ransomware Rules the Quarter
Ransomware was at the heart of most critical breaches. Attackers used dual extortion, first encrypting, then leaking data to maximize leverage. Groups like Qilin, ALPHV/BlackCat, and Medusa featured prominently in reported intrusions.
Supply Chain: The Soft Belly of Cybersecurity
Vulnerabilities in third-party services (like billing, IT, and hosting providers) were a key intrusion vector. Many high-profile breaches began with lateral movement from smaller vendors into larger ecosystems.
Weak Credentials & Cloud Misconfigurations
Most successful intrusions stemmed from unauthorized access and system intrusion. Often due to unpatched software, weak passwords, or misconfigured public cloud buckets.
🧠 What This Means for Defenders
Defensive Depth is Critical – Organizations must layer endpoint, email, and network defenses to prevent initial access and limit lateral movement.
Third-Party Due Diligence is Non-Negotiable – Vetting and monitoring vendor access is now essential to digital trust.
Healthcare Needs a Cyber Lifeline – Breaches in hospitals and medical networks occurred weekly, highlighting underinvestment and overexposure.
🔍 What to Watch Next
Threat actors continue to adapt with evolving tactics despite law enforcement pressure. Stealer logs remain a hot commodity on dark web marketplaces like Genesis Market, which persist even after major takedowns. Meanwhile, “quishing,” the use of malicious QR codes, is rising rapidly, now appearing in emails, printed flyers, and fake surveys to trick users into divulging credentials. In the healthcare sector, attackers are leveraging AI-generated voice deepfakes to impersonate staff and manipulate targets, highlighting the growing intersection of artificial intelligence and social engineering.
📌 Coming Next Week
Hall of Hacks Top Vulnerabilities of Q1 2025, where we’ll dive into the most exploited CVEs, zero-day exposures, and patching gaps that attackers loved in early 2025.
Subscribe and Comment.
Copyright © 2025 CyberMaterial. All Rights Reserved.
Follow CyberMaterial on:
Substack, LinkedIn, Twitter, Reddit, Instagram, Facebook, YouTube, and Medium.