Cyber Briefing: 2025.12.10
Multiple attacks and breaches hit global organizations as critical flaws in WinRAR and major vendor products drive exploits, outages and law-enforcement action.
👉 What’s trending in cybersecurity today?
Welcome to Cyber Briefing, the newsletter that informs you about the latest cybersecurity advisories, alerts, incidents and news every weekday.
First time seeing this? Please Subscribe
🚨 Cyber Alerts
1. WinRAR Flaw Under Active Attack Now
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added a critical path traversal vulnerability in WinRAR, CVE-2025-6218, to its Known Exploited Vulnerabilities catalog due to active attacks by multiple threat actors. The flaw, which affects Windows-based versions and was patched in WinRAR 7.12, could allow an attacker to execute code by tricking a user into opening a malicious file.
2. Microsoft Fixes Dozens Of Security Flaws
Microsoft concluded 2025 with patches for 56 security flaws, including one that has been actively exploited, across its Windows platform. Of these, three are rated Critical, and 53 are rated Important in severity, with two defects publicly known at the time of release.
3. Urgent Patches Issued For Major Flaws
Fortinet, Ivanti, and SAP have released patches for critical security vulnerabilities in their products that could be exploited for authentication bypass and code execution. Organizations should promptly apply these updates to mitigate significant risks posed by these flaws, which include improper cryptographic signature verification and cross-site scripting issues.
For more alerts, click here!
💥 Cyber Incidents
4. Cyber Outage Hits PES Energize Phones
The Pulaski municipal utility, PES Energize, has closed its customer lobby and shifted outage reporting to backup channels following a cybersecurity incident that disabled its phones and computer systems. The utility is working with federal agencies and cybersecurity partners to resolve the issue, taking some systems offline as a precaution.
5. Cyberattack Hits Leavenworth Services
A November 19 cyberattack on the city government of Leavenworth, Kansas, caused a network outage that continues to disrupt internal systems. City officials are currently relying on manual workarounds for processes like invoice payments, permitting, and handling employment applications, though emergency services were not affected.
6. Inotiv Reports Ransomware Data Breach
Pharmaceutical research company Inotiv, based in West Lafayette, Indiana, disclosed a ransomware attack and data breach that resulted in the exfiltration of sensitive data from its network. The company, which specializes in drug discovery and development, confirmed the incident affected the information of 9,542 individuals, including current and former employees.
For more incidents click here!
📢 Cyber News
7. Justice Dept Targets Russian Hackers
A Ukrainian national has been federally indicted in Los Angeles for participating in dozens of destructive cyberattacks globally, supporting Russia’s geopolitical interests through her involvement with state-sponsored groups CyberArmyofRussia_Reborn and NoName057(16).
8. Spain Arrests Teen Over Data Theft
A 19-year-old hacker was arrested in Barcelona by the Spanish National Police for allegedly stealing and attempting to sell 64 million private records from nine companies. The suspect faces charges including cybercrime and unauthorized data disclosure after being found with the massive collection of personal information.
9. Polish Police Arrest Hackers With Tools
Three Ukrainian nationals were arrested in Poland for allegedly attempting to disrupt IT systems and acquire sensitive defense information using specialized hacking devices. The suspects face charges including fraud and possessing tools intended to compromise IT systems of national defense significance.
For more news click here
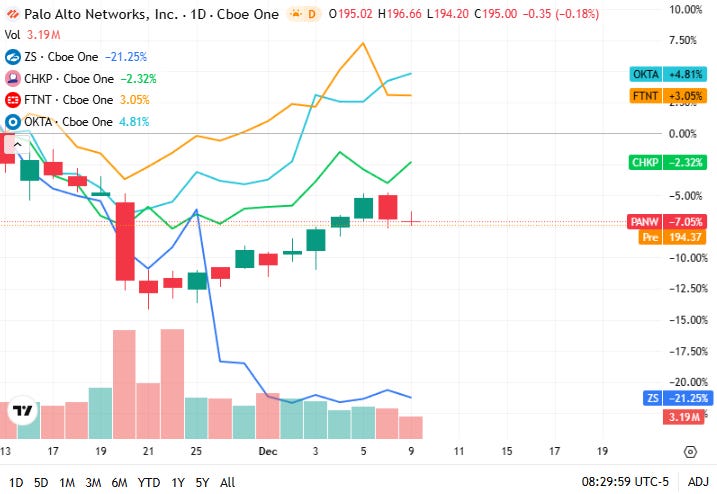
📈Cyber Stocks
On Wednesday, 10th December, cybersecurity stocks showed restrained movement as the sector continued to navigate a cautious broader market. Steady enterprise investment in cloud, identity and perimeter security helped offset macro uncertainty, while investor sentiment remained anchored by rising threat activity and regulatory pressures.
Palo Alto Networks closed at 195.00 dollars and held nearly flat, reflecting stable demand for its unified AI-driven security platform despite broader market hesitation.
Fortinet closed at 83.50 dollars and was mostly unchanged, supported by consistent interest in zero-trust and network-security offerings even as concerns around firewall product cycles persisted.
Zscaler closed at 243.01 dollars and slipped slightly, with light profit-taking tempering prior gains though adoption of cloud-delivered security continued to underpin long-term confidence.
Check Point Software Technologies closed at 194.19 dollars and posted a notable uptick, driven by renewed interest in perimeter and firewall technologies amid elevated global threat conditions.
Okta closed at 87.79 dollars and edged higher, supported by ongoing enterprise focus on identity protection and access control as identity-centric attacks continue to rise.
💡 Cyber Tip
📌 Microsoft Fixes Dozens of Security Flaws
Microsoft released patches for 56 Windows vulnerabilities, including one actively exploited flaw and two zero day command injection issues. The most urgent is CVE-2025-62221, a privilege escalation bug in the Cloud Files Mini Filter Driver that attackers are already using to gain SYSTEM access. Updates also covered PowerShell, Copilot for JetBrains, and Chromium-based Edge.
🔐 What You Should Do
• Install the latest Windows updates immediately
• Prioritize patching CVE-2025-62221 on all systems
• Limit PowerShell execution and monitor script activity
• Update vulnerable IDE plugins, especially Copilot for JetBrains
• Review systems for unusual privilege escalation attempts
⚠️ Why This Matters
Actively exploited flaws give attackers a direct path to full system takeover. Fast patching is the most effective defense.
📚 Cyber Book
Cybersecurity Bible by Alex Intrigue
That concludes today’s briefing . You can check the top headlines here!
Copyright © 2025 CyberMaterial. All Rights Reserved.
Follow CyberMaterial on:
Substack, LinkedIn, Twitter, Reddit, Instagram, Facebook, YouTube, and Medium.