Cyber Briefing: 2025.12.09
Cyber threats surged this week with Ivanti exploits, dev-tool malware, major healthcare breaches, Chrome AI security upgrades, and ransomware costs soaring.
👉 What’s going on in the cyber world today?
Welcome to Cyber Briefing, the newsletter that informs you about the latest cybersecurity advisories, alerts, incidents and news every weekday.
First time seeing this? Please Subscribe
🚨 Cyber Alerts
1. Hackers Target Ivanti To Spread Metarat
A China-based attack group is actively targeting Japanese shipping and transportation organizations by exploiting known vulnerabilities in Ivanti Connect Secure (ICS). The campaign, first observed in April 2025, utilizes two critical vulnerabilities to gain initial access and deploy several PlugX malware variants, including the previously unnamed MetaRAT and Talisman PlugX.
2. Malicious Dev Packages Steal Data
Cybersecurity researchers found two malicious extensions on the Microsoft VS Code Marketplace that infected developer machines with stealer malware. These extensions, which posed as a premium dark theme and an AI coding assistant, stole sensitive data like code, emails, passwords, and browser sessions and sent the information to an attacker-controlled server.
3. Ransomware Gangs Use Shanya Packer
Multiple ransomware groups are utilizing the Shanya packer-as-a-service to deploy payloads designed to disable endpoint detection and response (EDR) solutions on victim systems. This service helps cybercriminals obfuscate their malicious code, making it difficult for standard security tools to detect and analyze.
For more alerts, click here!
💥 Cyber Incidents
4. Vitas Hospice Breach Hits Thousands
More than 300,000 individuals were affected by a recent cybersecurity incident at Vitas Healthcare, the largest for-profit hospice chain in the United States, according to the US Department of Health and Human Services (HHS). The organization discovered an intrusion on October 24, which allowed an attacker to access and download personal information belonging to current and former patients.
5. Microsoft Probes Copilot Outage Europe
Microsoft is currently addressing a service issue that is preventing some users in Europe from accessing its AI-powered Copilot digital assistant, with others who can connect possibly experiencing reduced functionality. The company is actively investigating and working to resolve the capacity scaling problem that caused the disruption.
6. Tri Century Eye Care Breach Hits Many
A data breach at Tri-Century Eye Care, which provides comprehensive eye care services in Bucks County, Pennsylvania, has potentially affected about 200,000 individuals, according to the US Department of Health and Human Services data breach tracker. The incident, attributed to the Pear ransomware group, may have compromised patients’ and employees’ personal and protected health information after the group gained access to certain files.
For more incidents click here!
📢 Cyber News
7. Google Strengthens Chrome Against Attacks
Google added new security features to Chrome following the integration of agentic AI capabilities, implementing layered defenses against indirect prompt injections from untrusted web content. These new protections include the User Alignment Critic, which independently evaluates the AI agent’s actions to ensure they align with the user’s stated goal and vetoes misaligned actions, and Agent Origin Sets, which limit the agent’s access to only relevant data sources to prevent cross-origin data leaks and site isolation bypasses.
8. Ransomware Payments Top 4.5 Billion
Ransomware payments reported to FinCEN exceeded $4.5 billion through 2024, peaking in 2023. A new FinCEN report revealed that over $2.1 billion was paid to ransomware groups between 2022 and 2024, with $1.1 billion paid just in 2023.
9. Cloudflare Outage Linked To React2Shell
Cloudflare’s recent outage on a Friday was attributed to the implementation of mitigations designed to address the critical, newly disclosed React2Shell remote code execution vulnerability, officially known as CVE-2025-55182. The security measure, intended to protect against widespread exploitation by threat actors targeting the popular React framework, unexpectedly caused Cloudflare’s network to become unavailable for several minutes, impacting major internet services like Zoom and LinkedIn.
For more news click here
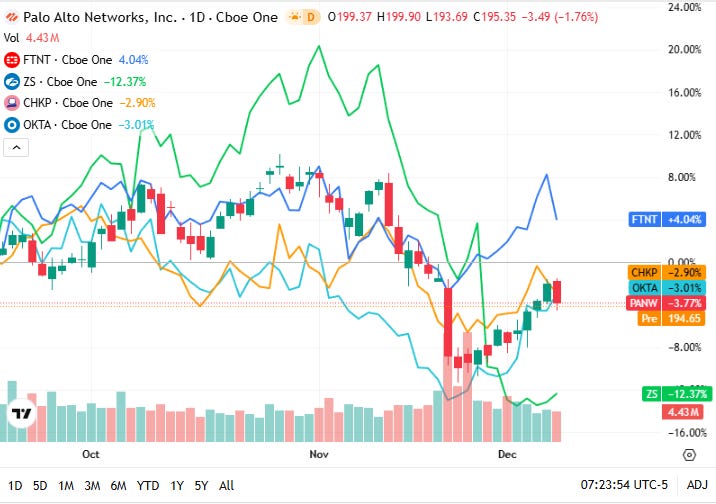
📈Cyber Stocks
On Tuesday, 9th December, cybersecurity stocks traded mixed as investors continued to balance sector stability against broader market caution. Demand drivers such as identity protection, cloud-security adoption, and AI-driven threat detection supported sentiment, even as selective profit-taking and macro uncertainty shaped intraday movements.
Palo Alto Networks closed at 195.35 dollars and dipped slightly, reflecting a soft start to the session, though interest in platform-based AI security tools kept long-term momentum intact.
Fortinet closed at 83.53 dollars and moved lower, as lingering concerns around firewall refresh cycles overshadowed steady enterprise spending on zero-trust and network-security solutions.
Zscaler closed at 244.88 dollars and posted a small gain, supported by ongoing customer adoption of cloud-delivered security and increased investment in zero-trust architectures.
Check Point Software Technologies closed at 190.85 dollars and eased modestly, with muted sentiment surrounding its convertible-note offering balanced by stable global demand for perimeter and AI-enhanced firewall technologies.
Okta closed at 87.29 dollars and inched higher, driven by renewed interest in identity-security and access-control solutions as organisations respond to escalating identity-based attacks.
💡 Cyber Tip
📦 Malicious VS Code Extensions Steal Developer Data
Two fake VS Code extensions posing as a dark theme and an AI coding assistant were caught stealing code, passwords, cookies, Wi-Fi credentials, and browser sessions. The malware used stealthy scripts and DLL hijacking via Lightshot to quietly exfiltrate data. Similar threats are appearing across Go, npm, and Rust ecosystems.
🔐 What You Should Do
Install extensions only from trusted and verified publishers
Review and remove unused or suspicious extensions regularly
Use security tools that monitor PowerShell, curl, and DLL sideloading
Never store API keys or secrets in browsers or project folders
Use dependency security scanners to detect malicious packages
⚠️ Why This Matters
A single compromised extension can leak source code, credentials, and internal sessions, exposing your development environment and software supply chain to attackers.
📚 Cyber Book
The Ethics of Cybersecurity by Markus Christen , Bert Gordijn, Michele Loi
That concludes today’s briefing . You can check the top headlines here!
Copyright © 2025 CyberMaterial. All Rights Reserved.
Follow CyberMaterial on:
Substack, LinkedIn, Twitter, Reddit, Instagram, Facebook, YouTube, and Medium.