Cyber Briefing: 2025.12.08
Android malware surges, WordPress RCE exploited, MuddyWater deploys new backdoor, major hacks hit Russia, Petco and Honduras, plus new laws and scams emerge.
👉 What’s going on in the cyber world today?
Welcome to Cyber Briefing, the newsletter that informs you about the latest cybersecurity advisories, alerts, incidents and news every weekday.
First time seeing this? Please Subscribe
🚨 Cyber Alerts
1. Android Malware Adds Stronger Data Theft
Two new Android malware families, FvncBot and SeedSnatcher, have been publicly detailed by cybersecurity researchers, alongside the discovery of an enhanced version of the existing ClayRat malware. The findings come from Intel 471, CYFIRMA, and Zimperium, who are tracking these threats that target mobile users for financial fraud and data theft.
2. Sneeit RCE And ICTBroadcast Bug Power Attacks
A critical remote code execution vulnerability, CVE-2025-6389 (CVSS score: 9.8), in the Sneeit Framework WordPress plugin is being actively exploited in the wild, allowing unauthenticated attackers to seize control of vulnerable sites. Security firm Wordfence reported over 131,000 exploitation attempts since the flaw was publicly disclosed and exploitation began on November 24, 2025.
3. MuddyWater Uses UDPGangster In Campaign
The Iranian hacking group MuddyWater is using a new backdoor called UDPGangster that employs the User Datagram Protocol (UDP) for its command-and-control (C2) communications, primarily targeting entities in Turkey, Israel, and Azerbaijan.
For more alerts, click here!
💥 Cyber Incidents
4. Hackers Hit Major Russian Logistics Firm
Ukrainian hackers disabled a major Russian logistics company, Eltrans+, that transports sanctioned goods and military components, successfully wiping out approximately 165 terabytes of crucial data in an operation timed to coincide with Ukraine’s Armed Forces Day. The coordinated cyberattack, executed by Ukraine’s Military Intelligence cyber unit and the hacker group BO Team, crippled the firm’s digital infrastructure, servers, and vital backups.
5. Petco Confirms Data Exposure Incident
Petco, a major pet products and services retailer, recently reported a data breach to California’s attorney general, which compromised the personal information of some customers. The company identified a software application misconfiguration that exposed certain files online and is now offering free credit and identity theft monitoring services to those affected.
6. Honduran Vote System Faces Security Breach
Honduras’s National Electoral Council (CNE) confirmed a cybersecurity breach in the system for reporting last month’s general election results, which an official stated compromises the validity of the vote counts. The controversy arises as the conservative National Party candidate, Nasry Asfura, maintains a narrow lead over Liberal Party candidate Salvador Nasralla, with only 88% of ballots counted.
For more incidents click here!
📢 Cyber News
7. FBI Warns Of Virtual Kidnapping Scams
The FBI has issued a warning regarding a rise in virtual kidnapping ransom scams where criminals use manipulated social media images as fake proof of life photos. These scams, which involve no actual abduction, are carried out by contacting victims via text message to demand ransom payments.
8. Portugal Revises Cybercrime Law For Researchers
Portugal’s cybercrime law now includes a legal safe harbor for security researchers, making hacking non-punishable under strict, good-faith conditions. This new provision protects actions aimed at identifying and responsibly disclosing vulnerabilities to enhance cybersecurity, as long as specific limits are observed.
9. EU Fines X 140 Million Over Blue Check
The European Commission has fined X €120 million for violating transparency obligations under the Digital Services Act (DSA), marking the first non-compliance ruling under these rules. The platform was found to have breached requirements through its misleading ‘blue checkmark’ system, opaque advertising database, and by blocking researchers’ access to public data.
For more news click here
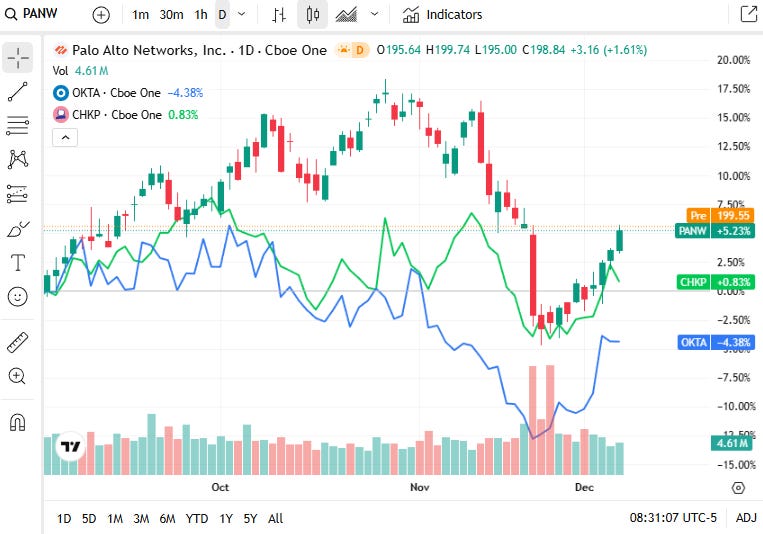
📈Cyber Stocks
On Monday, 8th December, cybersecurity stocks showed mixed but generally resilient performance as the sector continued to benefit from heightened enterprise security spending, stronger cloud-security demand, and renewed interest in AI-driven defensive technologies. While broader macro conditions remained cautious, ongoing geopolitical tensions, rising regulatory scrutiny, and increased cyber incidents helped sustain investor appetite for high-quality pure-play cybersecurity names.
Palo Alto Networks closed at 198.84 dollars and moved slightly higher, supported by stronger long-term demand for unified AI-driven security platforms. The recent Chronosphere acquisition created some valuation concerns, but improved fiscal 2026 guidance kept sentiment firm.
Fortinet closed at 86.92 dollars and recovered modestly, as long-term demand for zero-trust, cloud and network-security solutions outweighed near-term worries about a slowing firewall refresh cycle.
Zscaler closed at 242.68 dollars and posted a mild gain, driven by consistent enterprise adoption of cloud-delivered security and stronger spending on zero-trust and remote-work protections.
Check Point Software Technologies closed at 193.06 dollars and eased slightly, reflecting investor caution following its convertible-note announcement, though demand for perimeter, firewall and AI-focused protections remained supportive.
Okta closed at 85.89 dollars and was largely flat, with steady identity-security demand balancing broader enterprise budget caution and macro-driven spending sensitivities.
💡 Cyber Tip
📱 Android Malware Targets Banking and Crypto Users
New research highlights three dangerous Android threats: FvncBot, a fresh banking trojan built from scratch; SeedSnatcher, a crypto-focused stealer spreading through Telegram; and an upgraded ClayRat, now capable of screen recording, keystroke logging, and stealthy overlays. All three abuse Android accessibility services, fake app prompts, and malicious overlays to steal credentials, SMS 2FA codes, and even take remote control of the device.
🔐 What You Should Do
• Never install apps from links, Telegram channels, or unofficial APKs, especially those claiming to be banking, wallet, or system updates.
• Review app permissions carefully, especially accessibility, SMS, screen capture, and file access. Deny anything that seems unnecessary.
• Enable Google Play Protect and keep your device updated to block newer malware loaders.
• Use official banking and crypto apps only from the Play Store, and verify the developer name before installing.
• Do not enter seed phrases into any app or screen that appears unexpectedly, even if it looks legitimate. Malware like SeedSnatcher uses near-perfect phishing overlays.
• Turn on multi-factor authentication using an authenticator app, not SMS, whenever possible.
• If your device suddenly asks for accessibility permissions, treat it as a red flag and uninstall the app immediately.
⚠️ Why This Matters
Modern Android malware is no longer simple spyware. Threat actors now combine keylogging, remote control, screen streaming, overlay phishing, and 2FA interception to execute full account takeovers and financial theft. A single tap on a fake app or permissions prompt can hand over banking access, wallet keys, and sensitive data. Vigilance during app installation and permission requests is your strongest defense.
📚 Cyber Book
A Comprehensive Look at Fraud Identification and Prevention by James R. Youngblood
That concludes today’s briefing . You can check the top headlines here!
Copyright © 2025 CyberMaterial. All Rights Reserved.
Follow CyberMaterial on:
Substack, LinkedIn, Twitter, Reddit, Instagram, Facebook, YouTube, and Medium.