Cyber Briefing: 2025.12.05
VPN flaw exploited, Predator targeting revealed, China RAT campaign, major breaches at Leroy Merlin & Marquis, ASUS vendor hack, arrests, PRC backdoor, NCSC warns.
👉 What’s going on in the cyber world today?
Welcome to Cyber Briefing, the newsletter that informs you about the latest cybersecurity advisories, alerts, incidents and news every weekday.
First time seeing this? Please Subscribe
🚨 Cyber Alerts
1. Hackers Exploit ArrayOS AG VPN Flaw
Threat actors are actively exploiting a command injection vulnerability in Array AG Series VPN devices to install webshells and create unauthorized user accounts. This flaw, which Array Networks patched in May without assigning a formal identifier, is being used in attacks reported by JPCERT/CC, primarily targeting Japanese organizations since at least August.
2. Intellexa Leak Exposes Predator Zero Days
A Pakistani human rights lawyer from Balochistan was the target of an attempted digital attack using Intellexa’s Predator spyware, according to an Amnesty International report. The attack involved a suspicious WhatsApp link, making the lawyer the first known civil society member in Pakistan targeted by this mercenary surveillance tool.
3. Silver Fox Spreads ValleyRAT In China
The threat actor known as Silver Fox is using a false flag operation to impersonate a Russian threat group while targeting organizations in China. This SEO poisoning campaign employs Microsoft Teams lures to trick victims into downloading a malicious file that ultimately deploys ValleyRAT (Winos 4.0), a remote access trojan linked to Chinese cybercrime.advised, as the flaw requires no special setup and is being actively exploited.
For more alerts, click here!
💥 Cyber Incidents
4. Leroy Merlin Reports Data Breach
French home improvement and gardening retailer Leroy Merlin has alerted its customers in France about a recent data breach that compromised their personal information, though no banking data or online passwords were exposed. The company has contained the incident and is advising affected customers to be vigilant against phishing attempts.
5. Marquis Breach Hits Over 780,000 People
Hackers breached the fintech firm Marquis, resulting in the theft of personal and financial data belonging to over 780,000 individuals. The security breach at the fintech firm Marquis involved hackers stealing personal and financial data, specifically including names, addresses, Social Security numbers (SSNs), and card numbers, ultimately impacting more than 780,000 people.
6. ASUS Confirms Vendor Breach By Everest
ASUS confirmed a breach at a third-party supplier led to the exposure of some phone camera source code, after the Everest ransomware group claimed responsibility and leaked sample data. The company stated that no user data, products, or internal systems were impacted and is now focusing on strengthening its supply chain security.
For more incidents click here!
📢 Cyber News
7. Hackers Accused Of Wiping 96 Databases
Two Virginia brothers were arrested and charged with allegedly conspiring to steal sensitive government information and destroy databases after being fired from their jobs as federal contractors. This new indictment follows a previous prison sentence the twins served after pleading guilty in 2015 to unauthorized access and theft of personal information while working for the U.S. State Department.
8. PRC Hackers Use BrickStorm In US
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has detailed BRICKSTORM, a sophisticated backdoor written in Golang and used by state-sponsored Chinese threat actors to achieve long-term persistence in VMware vSphere and Windows environments. This malware grants attackers interactive shell access, supports multiple protocols for stealthy command-and-control, and is notable for its self-monitoring feature that ensures its automatic reinstallation and continued operation.
9. NCSC Warns Orgs Of Exposed Device Flaws
The UK’s National Cyber Security Center (NCSC) is currently testing a new service called Proactive Notifications, which uses internet scanning and public data, delivered via Netcraft, to identify unpatched vulnerabilities and lacking security services in organizations’ environments, prompting specific software update recommendations. This service is intended to help harden systems and reduce risks, complementing the more established ‘Early Warning’ service, which provides timely alerts on potential cyberattacks and compromises once they are detected.
For more news click here
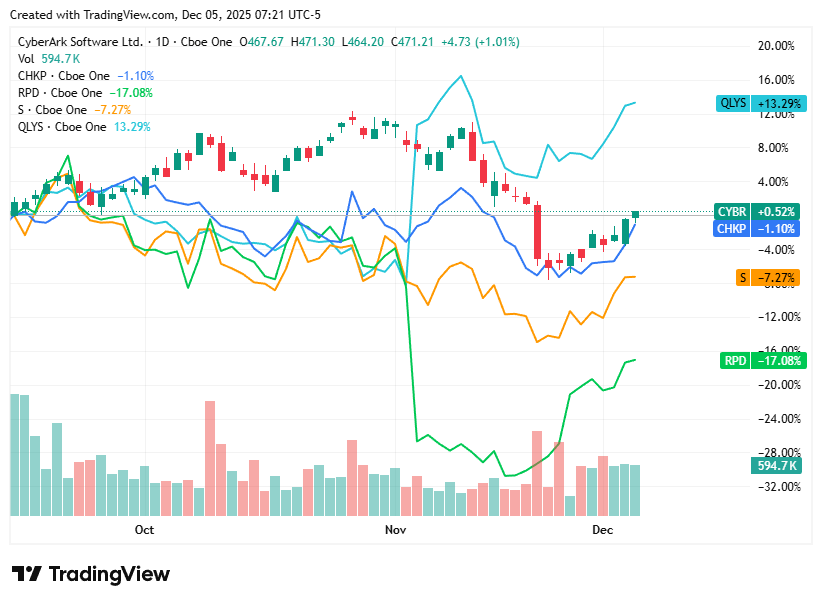
📈Cyber Stocks
On Friday, 5th December, cybersecurity stocks generally saw gains as investor sentiment regained some footing after a choppy week. A combination of renewed interest in identity, perimeter and compliance-driven security tools, plus a modest shift toward defensive technology names, supported the sector. The broader macro environment remained cautious, but security demand trends and valuation resets appeared to encourage selective buying.
CyberArk Software closed at 471.21 dollars and moved higher, reflecting investor confidence in identity-security and privileged-access management as corporates continue prioritising cyber-resilience.
Check Point Software Technologies closed at 195.83 dollars and posted a strong uptick, driven by renewed demand for firewalls, perimeter and network-security solutions as organisations reinforce perimeter and cloud defenses.
Rapid7, closed at 16.12 dollars and nudged up, supported by ongoing demand for vulnerability-management, detection & response services amid rising compliance and audit pressures.
SentinelOne, closed at 16.97 dollars and was nearly flat, indicating steady investor interest in AI-driven endpoint detection and response (EDR), albeit tempered by still-cautious sentiment in high-growth security names.
Qualys, closed at 149.63 dollars and gained modestly, buoyed by robust demand for cloud-based vulnerability scanning, compliance, and continuous-monitoring tools as hybrid-cloud deployments and regulatory requirements increase.
💡 Cyber Tip
📡 Intellexa Leak Exposes Predator Zero Days
A Pakistani human rights lawyer was recently targeted with a WhatsApp link tied to Predator spyware. This marks the first known civil society target in Pakistan, according to Amnesty International. Leaked Intellexa documents shed new light on how Predator is marketed and deployed, revealing its use of stealthy one-click and zero-click exploits on both Android and iOS.
🔐 What You Should Do
Avoid clicking links sent from unknown or unexpected numbers on WhatsApp, Signal, SMS, or email.
Keep both your device OS and browser fully updated to reduce exposure to zero day exploits.
Disable link previews in messaging apps when possible since some spyware uses preview triggers.
Use Lockdown Mode on iOS or Advanced Protection features on Android if you are at higher risk.
Report suspicious messages to the platform and delete them immediately.
⚠️ Why This Matters
Spyware like Predator targets journalists, activists, lawyers, and political figures using highly advanced exploits. A single tap on a malicious link can compromise an entire device. Vigilance with unexpected messages is one of the strongest defenses against targeted surveillance.
📚 Cyber Book
The Truth About Avoiding Scams by Steve Weisman
That concludes today’s briefing . You can check the top headlines here!
Copyright © 2025 CyberMaterial. All Rights Reserved.
Follow CyberMaterial on:
Substack, LinkedIn, Twitter, Reddit, Instagram, Facebook, YouTube, and Medium.