Cyber Briefing: 2025.12.02
Malicious VS Code packages, SmartTube breach, ShadyPanda spyware, major data leaks, mass camera hacks, sports federation breach, mixer takedown, Lazarus crypto heist, and India’s new phone app rule.
👉 What’s going on in the cyber world today?
Welcome to Cyber Briefing, the newsletter that informs you about the latest cybersecurity advisories, alerts, incidents and news every weekday.
First time seeing this? Please Subscribe
🚨 Cyber Alerts
1. Glassworm Malware Strikes Again In VS Code
The Glassworm campaign, a malware attack targeting developers via Visual Studio Code (VS Code) extension marketplaces (OpenVSX and Microsoft Visual Studio Marketplace), has entered its third wave, adding 24 new malicious packages. This malware uses invisible Unicode characters to hide its code and, once installed, steals account credentials and cryptocurrency data while setting up a SOCKS proxy and HVNC client for remote access.
2. Smarttube Breach Pushes Malicious Update
The popular open-source Android TV app, SmartTube, was compromised after an attacker accessed the developer’s signing keys and pushed a malicious update, which was subsequently flagged by Android’s Play Protect. The developer has confirmed the compromise, urged users to switch to a new app ID, and is working to address community trust issues following the insertion of a suspicious, hidden library that communicates with a remote server.
3. Shadypanda Extensions Hit Millions Users
A persistent malware operation dubbed “ShadyPanda” has accumulated over 4.3 million installations across 145 seemingly harmless Chrome and Edge browser extensions, gradually evolving them into sophisticated spyware capable of remote code execution. While Google has removed its Chrome versions, the campaign remains active on the Microsoft Edge platform, utilizing an update mechanism to transform the tools into backdoors that exfiltrate user data and perform search hijacking.
For more alerts, click here!
💥 Cyber Incidents
4. Hackers Claim Mercedes Benz USA Breach
A threat actor named “zestix” claims to have breached Mercedes-Benz USA’s legal infrastructure, exfiltrating $18.3 \text{ GB}$ of sensitive data, which is now being sold on a dark web forum for $\$5,000$. This alleged leak, which targets documentation related to consumer warranty defense, reportedly includes confidential legal strategies, vendor banking details, and customer Personally Identifiable Information (PII).
5. 120000 Cameras Hacked In South Korea Now
Four individuals in South Korea have been arrested for allegedly hacking over 120,000 video cameras in homes and businesses to create sexually exploitative content for sale on an overseas website. Police stated the accused exploited vulnerabilities in the Internet Protocol (IP) cameras, primarily simple passwords, to obtain the unauthorized footage.
6. French Soccer Federation Suffers Cyberattack
The French soccer federation (FFF) announced that it was subjected to a cyber-attack that led to the theft of data concerning its members via the administrative software used by local clubs. The federation confirmed that the breach, which exposed basic personal information such as names and addresses, has since been contained, and it has filed a formal complaint.
For more incidents click here!
📢 Cyber News
7. Police Shut Down Cryptomixer Service
Swiss and German law enforcement, supported by Europol and Eurojust, successfully dismantled the Cryptomixer cryptocurrency-mixing service, which is estimated to have helped cybercriminals launder over €1.3 billion in Bitcoin since 2016. In the joint operation, authorities seized servers, data, domains, and €24 million in Bitcoin, targeting a service that was popular with ransomware groups and dark web markets for obscuring the traceability of illegal funds.
8. North Korea Lazarus Group Hits Crypto
A recent cyberattack on South Korea’s largest cryptocurrency exchange, Upbit, resulted in the theft of $30 million, with South Korean officials alleging that North Korea’s government-backed Lazarus hacking group is responsible based on the specific tactics used for the breach and subsequent money laundering. The platform has suspended all deposits and withdrawals, transferred assets to a secure cold wallet, and guaranteed that it will cover all financial losses incurred by the theft.
9. India Orders Phones To Preinstall App
The Indian government’s telecommunications ministry has mandated that major mobile device manufacturers must preload the non-removable cybersecurity application Sanchar Saathi on all new phones within 90 days. This app is designed to help users report fraud, block stolen devices, and check mobile connections under their name, and the government justifies the directive as necessary for enhancing telecom cybersecurity and national security.
For more news click here
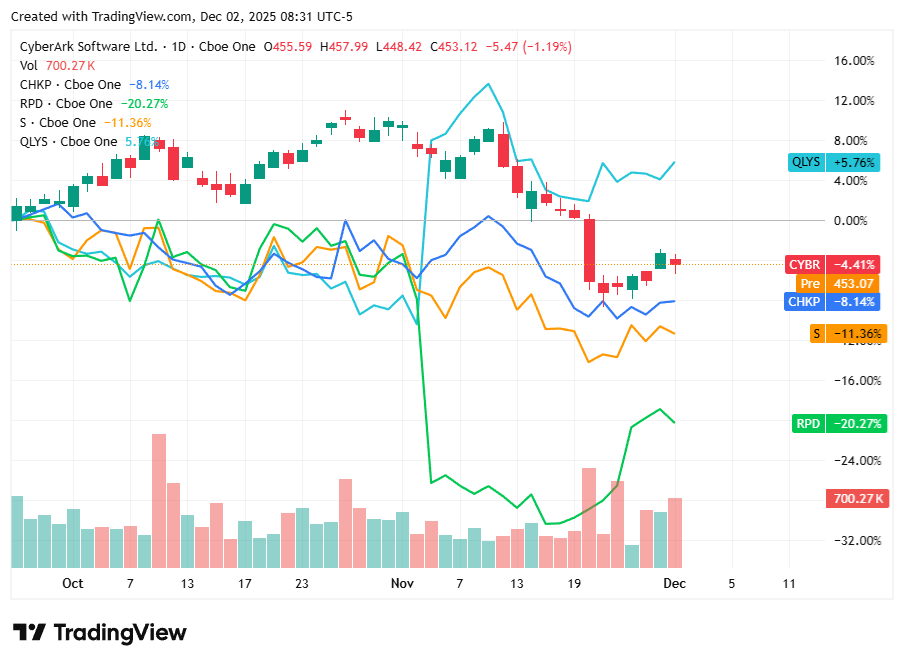
📈Cyber Stocks
On Tuesday, 2nd December, cybersecurity stocks delivered a mixed performance as investors balanced steady enterprise demand with ongoing caution across the broader technology sector. While long-term fundamentals in identity, vulnerability management, and endpoint security remained strong, selective profit-taking and valuation sensitivity shaped market movements. Overall, the sector reflected a blend of resilience and hesitation as markets awaited clearer signals on year-end spending priorities.
CyberArk Software Ltd. closed at 453.12 dollars and dipped slightly, reflecting mild profit-taking despite continued strength in privileged-access and identity-security demand.
Check Point Software Technologies Ltd. closed at 187.05 dollars and edged higher, supported by consistent enterprise interest in network and perimeter-security solutions.
Rapid7, Inc. closed at 15.42 dollars and moved lower, indicating cautious investor sentiment around vulnerability-management and detection-response spending cycles.
SentinelOne, Inc. closed at 16.08 dollars and slipped modestly, as appetite for high-growth endpoint-security names remained restrained amid macro uncertainty.
Qualys, Inc. closed at 143.16 dollars and posted gains, benefiting from steady demand for cloud-based vulnerability scanning and compliance services.
💡 Cyber Tip
🕶️ ShadyPanda Browser Extensions Hit Millions of Users
A massive and long-running malware campaign called ShadyPanda has infected more than 4.3 million Chrome and Edge users through 145 browser extensions that appeared harmless. These extensions, some dating back to 2018, evolved over time from affiliate fraud tools to full spyware with remote code execution capabilities. While Google has removed them from the Chrome Web Store, many remain active on the Microsoft Edge Add-ons platform.
What You Should Do
Review all installed Chrome and Edge extensions and remove any you do not fully recognize or trust.
Avoid installing extensions with very low reviews, unknown publishers, or suspicious permissions.
Monitor your browser for unexpected search redirects or pop-ups.
Clear cookies and reset browser settings if you suspect compromise.
Use trusted security tools that detect extension-based threats and malicious updates.
Why This Matters
ShadyPanda extensions can hijack searches, steal cookies, track browsing, and even execute remote code through a built-in backdoor that downloads commands every hour. The campaign remains active on Edge, putting millions of users at risk of ongoing data theft and full browser compromise. Regular extension audits are essential for protection.
📚 Cyber Book
How to Beat Scammers by Nick Stapleton
That concludes today’s briefing . You can check the top headlines here!
Copyright © 2025 CyberMaterial. All Rights Reserved.
Follow CyberMaterial on:
Substack, LinkedIn, Twitter, Reddit, Instagram, Facebook, YouTube, and Medium.