Cyber Briefing: 2025.11.28
Botnet tests, crypto library flaw, Central Asia RAT attacks, Korean MSP ransomware surge, Asahi data theft, Mazda spared, arrests over cybercrime, UK privacy concerns, and Polish espionage case.
👉 What’s going on in the cyber world today?
Welcome to Cyber Briefing, the newsletter that informs you about the latest cybersecurity advisories, alerts, incidents and news every weekday.
First time seeing this? Please Subscribe
🚨 Cyber Alerts
1. ShadowV2 Botnet Tests During AWS Outage
A new Mirai-based botnet malware dubbed ‘ShadowV2’ was recently observed using exploits for known vulnerabilities to target various IoT devices, including those from D-Link and TP-Link. The activity was noted during a major AWS outage, suggesting the brief deployment may have been a test run for the malware.
2. Forge Library Patch Stops Signature Bypass
A significant vulnerability, CVE-2025-12816, was found in the popular node-forge JavaScript cryptography library, allowing attackers to bypass signature verifications by creating data that appears valid but is cryptographically malformed. This high-severity flaw stems from an interpretation conflict in the library’s ASN.1 validation mechanism, which can trick applications into accepting invalid data.
3. Bloody Wolf Widens Java RAT Campaign
The threat actor Bloody Wolf has been executing a cyber campaign targeting Kyrgyzstan since June 2025, and later expanded to include Uzbekistan, primarily aimed at deploying the NetSupport RAT by impersonating government ministries. This low-profile group uses social engineering and simple malicious Java Archive (JAR) files delivered via spear-phishing to compromise finance, government, and IT sectors.
For more alerts, click here!
💥 Cyber Incidents
4. Qilin Ransomware Hits Korean MSP
A sophisticated supply chain attack, potentially involving the Qilin Ransomware-as-a-Service (RaaS) group and North Korean actors, has compromised South Korea’s financial sector by exploiting a Managed Service Provider (MSP) to deploy the ransomware. This campaign, dubbed “Korean Leaks” by the attackers, caused an unprecedented surge in South Korean ransomware victims, with 24 out of 25 cases in September 2025 targeting the financial industry.
5. Asahi Breach Hits Two Million Users
Japanese brewing company Asahi announced that a September ransomware attack, later claimed by the Qilin group, resulted in the theft of personal information belonging to approximately 2 million individuals. The incident, which caused partial disruption to operations, compromised sensitive data for customers, employees, and their family members, though the company confirmed no credit card information was stolen.
6. Mazda Reports No Impact From Oracle Hack
Mazda has confirmed it was targeted in the recent Cl0p-attributed hacking campaign exploiting Oracle E-Business Suite (EBS) vulnerabilities, though the carmaker stated that its systems and production were not impacted, and no data leakage has been confirmed. Despite Mazda being named on the Cl0p ransomware group’s leak site, the company’s swift action in applying EBS patches and its assessment of the attack’s ineffectiveness suggest it is unlikely to pay a ransom.
For more incidents click here!
📢 Cyber News
7. Russia Arrests Young Cybersecurity Leader
A 21-year-old Russian cybersecurity entrepreneur, Timur Kilin, has been arrested in Moscow on treason charges, becoming the latest target in the government’s crackdown on the nation’s tech community. Kilin had publicly criticized the state-backed Max messaging app and opposed a proposed anti-cybercrime bill that would criminalize the disclosure of security flaws.
8. UK Privacy Enforcement Activity Drops
A coalition of over 70 civil liberties groups and experts is calling for a parliamentary investigation into the UK’s principal data protection regulator, the Information Commissioner’s Office (ICO), alleging a profound “collapse in enforcement activity” stemming from deep structural failures. This lack of action, particularly against government bodies like the Ministry of Defence following a serious data leak that reportedly resulted in deaths in Afghanistan, has allegedly led to an increase in reported data breaches and complaints in the UK.
9. Poland Detains Russian Hacking Suspect
A Russian national was detained in Poland on suspicion of hacking local companies’ IT systems, in a case authorities link to a broader pattern of Russian espionage and sabotage efforts. The interior minister stated the man was arrested for breaching security to access company databases, with prosecutors adding he allegedly manipulated an online retailer’s systems, potentially disrupting operations and endangering customers.
For more news click here
📈Cyber Stocks
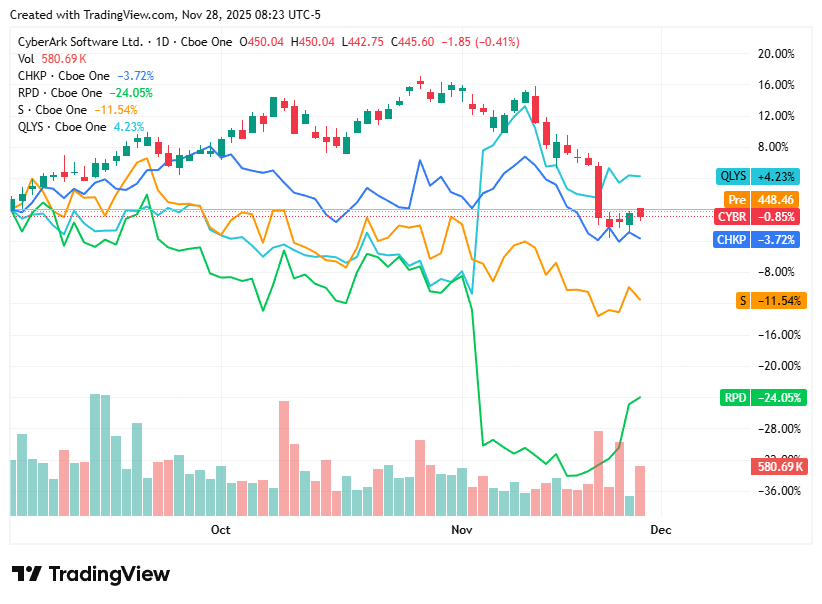
On Friday, 28th November, the broader cybersecurity segment showed modest divergence among names: some equities edged up, while others saw mild pressure, as investors balanced long-term demand for cyber-security infrastructure with continued caution around valuations and macroeconomic headwinds. Overall, the sector remained under the influence of mixed sentiment — steady demand but selective buying.
CyberArk Software Ltd. closed at 445.60 dollars and was marginally lower, reflecting a broadly cautious tone toward identity/privileged-access security names despite stable long-term demand fundamentals.
Check Point Software Technologies Ltd. closed at 184.34 dollars and showed a slight dip, as investor focus lingered on potential near-term softening in enterprise spending and the impact on traditional firewall and perimeter-security vendors.
Rapid7, Inc. closed at 15.51 dollars and edged up, buoyed by continued interest in vulnerability management and detection & response platforms — sectors benefiting from ongoing cyber-threat awareness.
SentinelOne, Inc.closed at 15.94 dollars and dipped modestly, as broader volatility in high-growth tech weighed on sentiment despite the company’s growing appeal in AI-driven endpoint security.
Qualys, Inc. closed at 141.63 dollars and was nearly unchanged, indicating stable sentiment toward its cloud-based vulnerability scanning and compliance services, though lack of near-term catalysts kept movement muted.
💡 Cyber Tip
🔐 Forge Library Patch Fixes Critical Signature Verification Bypass
A high-severity flaw in the popular node-forge cryptography library allowed attackers to bypass signature verification by crafting malformed ASN.1 data that appeared valid to the library. The issue, tracked as CVE-2025-12816, affected versions up to 1.3.1 and could lead to authentication bypass, tampered signed data, or misuse of certificate operations in applications relying on node-forge for security.
What You Should Do
Update node-forge immediately to version 1.3.2 or later.
Review applications that depend on node-forge and confirm they are not using outdated versions.
Conduct security testing for components that rely on cryptographic validation, especially where ASN.1 parsing is involved.
Monitor CERT-CC and vendor advisories for related guidance or downstream impacts.
Why This Matters
Node-forge is downloaded nearly 26 million times per week, meaning many applications may be exposed to this verification bypass. Because malformed ASN.1 data could pass as valid, critical trust decisions within your application could be compromised. Prompt updates are essential to ensure cryptographic safety.
📚 Cyber Book
100 Facts About Black Friday & Cyber Monday with Tips on How to Avoid Scams by Robert Gres
That concludes today’s briefing . You can check the top headlines here!
Copyright © 2025 CyberMaterial. All Rights Reserved.
Follow CyberMaterial on:
Substack, LinkedIn, Twitter, Reddit, Instagram, Facebook, YouTube, and Medium.