Cyber Briefing: 2025.11.19
AI-agent exploits found, China hijacks DNS for malware, old Finger protocol abused, major breaches hit Under Armour, France, Denmark, plus arrests and new RCMP reporting system.
👉 What’s the latest in the cyber world today?
Welcome to Cyber Briefing, the newsletter that informs you about the latest cybersecurity advisories, alerts, incidents and news every weekday.
First time seeing this? Please Subscribe
🚨 Cyber Alerts
1. AI Agents Turned Against Each Other
Security researchers have found that malicious actors can exploit default settings in ServiceNow’s Now Assist AI platform to execute sophisticated “second-order prompt injection” attacks. This method leverages the platform’s agent-to-agent collaboration to allow attackers to unauthorizedly exfiltrate corporate data, modify records, and escalate privileges within internal systems.
2. Malware Spread Through DNS Rerouting
The China-aligned threat actor PlushDaemon is leveraging a newly discovered, custom Go-based network backdoor called EdgeStepper to perform sophisticated Adversary-in-the-Middle (AitM) attacks. EdgeStepper primarily works by hijacking a target’s DNS queries, redirecting them from legitimate software update servers to malicious infrastructure controlled by the attacker, facilitating supply chain compromises.
3. Old Finger Protocol Used In Malware
Threat actors are resurrecting the decades-old ‘finger’ command—once used for looking up user information—to retrieve and execute remote malicious commands on Windows devices. The simple protocol is being leveraged as a remote script delivery method, primarily in ClickFix attacks, bypassing detection and downloading malware like infostealers.
For more alerts, click here!
💥 Cyber Incidents
4. Under Armour Hit By Data Breach
The Everest ransomware group claims to have breached sportswear company Under Armour, posting a sample of what they allege is over 343GB of internal and customer data on the dark web. The hackers have given the retailer seven days to respond, raising concerns about potential identity theft, fraud, and social engineering risks for thousands of customers.
5. Danish Parties Targeted By Cyberattack
Pro-Russian hackers claimed responsibility for a cyberattack targeting the websites of several Danish political parties and a news outlet on the eve of local and regional elections, with the attack briefly causing the sites of the Conservatives and the Red-Green Alliance to be inaccessible. Danish intelligence had previously warned of a high likelihood of such Distributed Denial of Service (DDoS) attacks against election-linked websites by pro-Russian groups.
6. France Hit By Major Cyberattack
The French social charges body Urssaf has suffered a significant cyberattack on its Pajemploi service, potentially compromising the personal data, including names, addresses, and social security numbers, of up to 1.2 million private employers. Urssaf has reported the breach, which did not affect bank account numbers or service functionality, and is urging all users to be highly vigilant against expected phishing scams.
For more incidents click here!
📢 Cyber News
7. California Man Admits Crypto Laundering.
A 45-year-old California man, Kunal Mehta, has pleaded guilty to laundering at least $25 million stolen in a massive $230 million cryptocurrency heist. This plea makes him the eighth defendant to admit guilt in the scheme following charges brought by the Department of Justice in May 2025.
8. Russian Suspect Detained In Thailand
A Russian individual was detained in Thailand and is reportedly connected to the Void Blizzard hacking group, a relatively new threat actor aligned with the Kremlin that has attacked critical infrastructure and government networks throughout Europe and North America.
9. RCMP Launches Cybercrime Reporting System
The Royal Canadian Mounted Police (RCMP) has launched the new Report Cybercrime and Fraud website, a national, centralized system for individuals and organizations to report incidents of fraud and cybercrime to the National Cybercrime Coordination Centre (NC3) and the Canadian Anti-Fraud Centre (CAFC). This crucial tool aims to overcome severe underreporting by providing a user-friendly repository of information that will help law enforcement solve cases, disrupt cybercriminal activity, and ultimately prevent future victimization across Canada.
For more news click here
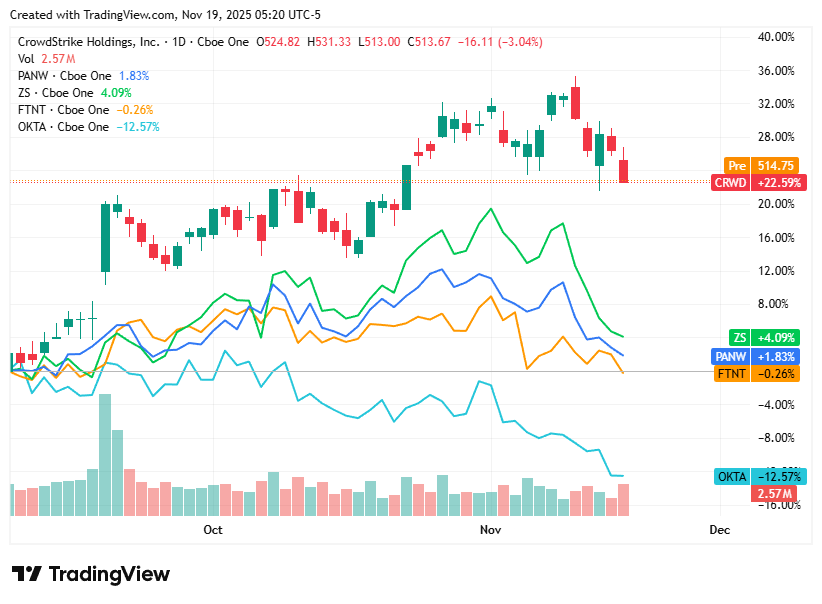
📈Cyber Stocks
On Wednesday, 19th November, cybersecurity stocks continued to trend lower as investors remained defensive across the broader technology sector. Persistent macro concerns, softer risk appetite, and renewed pressure on high-growth valuations weighed on the group, even as long-term demand for cloud, identity, and endpoint security stayed strong. Geopolitical cyber risks and regulatory scrutiny continued to underpin sector resilience, but markets favored caution over momentum ahead of key year-end signals.
CrowdStrike closed at 513.67 dollars and moved sharply lower, reflecting sustained profit-taking and heightened sensitivity to broader tech-market weakness.
Palo Alto Networks closed at 201.00 dollars and edged down as mixed enterprise-spending signals kept investors cautious despite ongoing platform demand.
Zscaler closed at 293.11 dollars and slipped modestly, weighed by concerns around high-growth valuations even as zero-trust adoption and cloud-security demand remained solid.
Fortinet closed at 80.15 dollars and fell further, with investor focus still centered on slowing firewall refresh cycles and uncertainty around hardware-driven revenue.
Okta closed at 81.03 dollars and finished nearly flat, indicating stable sentiment toward identity security but limited immediate catalysts to drive upside.
💡 Cyber Tip
🛑 Old Finger Protocol Used to Launch Malware Attacks
Threat actors are bringing back the decades-old Finger protocol to deliver remote commands onto Windows systems. Campaigns linked to ClickFix attacks trick users into running a harmless-looking command that secretly uses the finger utility to pull and execute malicious instructions from an attacker-controlled server. This technique is being used to download infostealer malware and other payloads while avoiding detection.
What You Should Do
Never run commands sent to you through email, chat, or pop-up prompts, even if they look simple or harmless.
Block the Finger protocol in your environment if it is not required.
Monitor for unexpected use of cmd.exe, batch files, or commands involving the finger utility.
Educate users about ClickFix-style scams that imitate Captcha checks or verification prompts.
Why This Matters
The Finger protocol is still supported on Windows, which gives attackers a built-in tool that can fetch and run remote commands without using typical malware delivery channels. Because the attack hides inside a legitimate system utility, it can bypass many security filters and quickly lead to malware installation or credential theft.
📚 Cyber Book
Wearable Medical Technologies by Kevin Chen
That concludes today’s briefing . You can check the top headlines here!
Copyright © 2025 CyberMaterial. All Rights Reserved.
Follow CyberMaterial on:
Substack, LinkedIn, Twitter, Reddit, Instagram, Facebook, YouTube, and Medium.