Cyber Briefing: 2025.11.18
Recent cyber incidents highlight a surge in targeted attacks and data breaches worldwide. Threats range from Iranian hackers launching spy operations and U.S. account takeovers, to massive DDoS attack
👉 What’s the latest in the cyber world today?
Welcome to Cyber Briefing, the newsletter that informs you about the latest cybersecurity advisories, alerts, incidents and news every weekday.
First time seeing this? Please Subscribe
🚨 Cyber Alerts
1. Fortinet Flaw Used To Create Admins
Cybersecurity researchers are urgently warning about an authentication bypass flaw in the Fortinet FortiWeb Web Application Firewall (WAF) (patched in version 8.0.2) that is being actively exploited in the wild to allow attackers to compromise devices, typically by adding new administrator accounts for persistence. The vulnerability is a combination of a path traversal bug and an authentication bypass that permits an attacker to impersonate an admin user by supplying specific values via the CGIINFO HTTP header.
2. Iran Hackers Launch SpearSpecter Spying
An Iranian state-sponsored group, APT42, is running a new espionage campaign, codenamed SpearSpecter, that targets high-ranking government and defense officials—and notably their family members—using personalized social engineering to gain access or deploy malware. This ongoing effort, detected in September 2025, leverages sophisticated tactics like impersonating trusted contacts or creating convincing conference invitations to build trust before delivering malicious payloads or harvesting credentials.
3. Interview Campaign Exploits JSON Storage
North Korean hackers are using LinkedIn and JSON storage services to spread malware in the “Contagious Interview” campaign, active since 2023. The attacks involve impersonating recruiters to trick targets into running a malicious “demo project” that ultimately deploys the BeaverTail info-stealer and the InvisibleFerret Remote Access Trojan (RAT).
For more alerts, click here!
💥 Cyber Incidents
4. Kenyan Gov Sites Back Online After Hack
A cyberattack targeting the government of Kenya resulted in the defacement of multiple ministry websites with explicit white supremacist and racist messages on Monday morning, temporarily taking platforms for key ministries like Interior, Health, and Education offline. The Kenyan Interior Ministry confirmed the incident, suspected to be the work of a group calling itself ‘PCP@Kenya,’ adding that systems were quickly contained and are now being monitored.
5. Massive Cloud DDoS Hits Microsoft Azure
Microsoft’s Azure platform successfully defended against the largest-ever cloud-based distributed denial of service (DDoS) attack, which peaked at 15.72 terabits per second (Tbps) and was launched by the Aisuru botnet. The attack, which flooded a single endpoint with nearly 3.64 billion packets per second, was automatically detected and mitigated by Azure’s protection service on October 24, resulting in no service interruptions for customers.
6. Princeton Reports Donor Data Breach
A database belonging to Princeton University, containing personal information for its community members including donors, alumni, students, faculty, and parents, was compromised in a hack discovered on November 10. The university publicly acknowledged the data breach on November 15, noting that the hacker had access for less than 24 hours and that while the full extent of the view is unclear, the database stores names, contact information, addresses, and donation history.
For more incidents click here!
📢 Cyber News
7. UK Hacker Ordered To Repay Bitcoin
A man convicted for the 2020 Twitter hack that compromised high-profile accounts, including former U.S. President Barack Obama, has been ordered to repay $5.40 million (4.1 million pounds) worth of Bitcoin, according to British prosecutors. Joseph James O’Connor, 26, who pleaded guilty in the U.S. to charges including wire fraud and computer intrusion, was sentenced to five years in prison in 2023.
8. NetApp Accuses Exec Of Stealing Secrets
NetApp has filed a dramatic lawsuit against former Senior VP and CTO, Jón Stefánsson, alleging he secretly developed a competing business, referencing the film “Office Space,” while still employed, and then immediately sold it to direct rival VAST Data after his departure. This case, which involves allegations of intellectual property theft and corporate deception, has resulted in a temporary restraining order against Stefánsson, highlighting the immense power a top executive can wield in the hypercompetitive cloud AI and data infrastructure market.
9. Rogue Hosting Company Shut Down
Dutch authorities seized thousands of servers from a self-proclaimed “bulletproof” hosting provider that was actively enabling large-scale global cybercrime, including ransomware and financial fraud. The operation, which involved confiscating approximately 250 physical servers, aims to disrupt active criminal networks that relied on the service’s promise of anonymity and non-cooperation with law enforcement.
For more news click here
📈Cyber Stocks
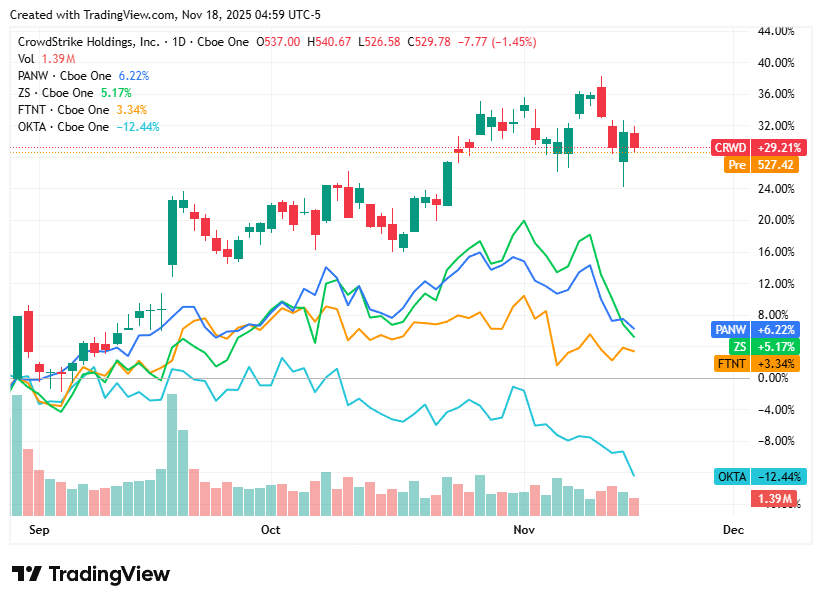
On Tuesday, 18th November, cybersecurity stocks trended lower across the board as investors remained cautious amid ongoing macro uncertainty and softness in the broader technology sector. Despite steady global demand for endpoint, identity, and cloud-security solutions, sentiment was weighed down by valuation concerns and profit-taking following recent sector gains. Geopolitical cyber risks continued to underpin long-term spending, but near-term market conditions pulled most cybersecurity names into negative territory.
CrowdStrike closed at 529.78 dollars and moved lower as investors took profit after recent strength, while broader weakness in growth-oriented tech added pressure.
Palo Alto Networks closed at 202.90 dollars and edged down, reflecting cautious sentiment around enterprise security spending cycles despite stable platform demand.
Zscaler closed at 294.92 dollars and declined more sharply, driven by sensitivity to high-valuation cloud names and concerns around short-term IT budget moderation.
Fortinet closed at 81.94 dollars and slipped slightly, as persistent worries over slowing firewall refresh activity overshadowed its solid fundamentals.
Okta closed at 81.07 dollars and recorded the largest drop among the group, reflecting investor hesitation in the identity-security segment and uncertainty around pacing of new contract expansions.
💡 Cyber Tip
Beware of “Demo Projects” in Unsolicited Job Interviews
Be extremely cautious of unsolicited job offers on professional networking sites that require you to download and execute code as a mandatory part of the interview process.
What to do:
Verify Identity: Thoroughly verify the authenticity of all unexpected recruitment offers, especially those from individuals or companies you have not previously engaged with.
Refuse Execution: Never download or execute unverified “demo projects,” coding tasks, or any executable files from external sources on your local or work system.
Monitor Traffic: Implement increased monitoring for suspicious or unexpected API requests directed towards common JSON storage or cloud services, as these are often used to host malicious payloads.
Why it matters: This type of sophisticated attack exploits the trust inherent in professional networking to deploy persistent and potent malware like the InvisibleFerret Remote Access Trojan. By being vigilant about code execution and monitoring API traffic, you can prevent info-stealing and long-term compromise of critical systems.
📚 Cyber Book
Identity Theft Privacy by Robert Siciliano
That concludes today’s briefing . You can check the top headlines here!
Copyright © 2025 CyberMaterial. All Rights Reserved.
Follow CyberMaterial on:
Substack, LinkedIn, Twitter, Reddit, Instagram, Facebook, YouTube, and Medium.