Cyber Briefing: 2025.11.17
RoninLoader spreads, XWiki exploited, Windows update bug hits, Logitech breached, Checkout rejects ransom, CCTV leak in India, record ransomware, NK scheme, US targets China scams.
👉 What’s trending in cybersecurity today?
Welcome to Cyber Briefing, the newsletter that informs you about the latest cybersecurity advisories, alerts, incidents and news every weekday.
First time seeing this? Please Subscribe
🚨 Cyber Alerts
1. Dragon Breath Deploys Roninloader Ghosts
The threat group Dragon Breath is deploying a sophisticated multi-stage loader, RONINGLOADER, primarily targeting Chinese-speaking users by disguising malicious Gh0st RAT-carrying installers as popular apps like Google Chrome and Microsoft Teams. This campaign employs numerous advanced evasion techniques, including abusing signed drivers, custom WDAC policies, and tampering with Microsoft Defender binaries via PPL abuse, all aimed at neutralizing endpoint security products popular in the Chinese market.
2. Rondodox Targets XWiki To Grow Botnet
The RondoDox botnet is actively exploiting a critical and recently patched arbitrary code execution vulnerability, CVE-2025-24893 (CVSS 9.8), in XWiki instances. This vulnerability, which allows any guest user to execute remote code, is seeing a significant spike in exploitation attempts by RondoDox and other threat actors for purposes including launching DDoS attacks and deploying cryptocurrency miners.
3. Windows 10 Update Error 800f0922
Microsoft is currently investigating a confirmed bug where the first Windows 10 Extended Security Update (KB5068781) is failing to install on some corporately licensed devices, reporting the error 0x800f0922. The company notes this installation failure, which causes the update to roll back, appears to specifically affect devices using Windows subscription activation via the Microsoft 365 Admin Center.
For more alerts, click here!
💥 Cyber Incidents
4. Logitech Confirms Major Data Breach
Logitech confirmed a data breach involving the exfiltration of certain internal data shortly after it was publicly named as a victim in the recent Cl0p hacking and extortion campaign targeting users of Oracle’s E-Business Suite (EBS). The company believes the incident stemmed from an unauthorized third party exploiting a zero-day vulnerability in a third-party software platform, though it does not anticipate a material financial impact.
5. Checkoutcom Rejects Hackers After Breach
Fintech company Checkout was breached by the ShinyHunters threat group, which stole merchant data from a legacy cloud system and is now demanding a ransom. Checkout has publicly refused to pay the ransom, choosing instead to strengthen its security and donate the intended funds to cybersecurity research.
6. Hackers Steal Maternity Ward Videos
Hacked sensitive video footage from a maternity hospital in India, depicting pregnant women during medical procedures, was discovered being sold on Telegram, prompting a police investigation. This incident revealed a much larger cybercrime operation where hackers stole and sold footage from at least 50,000 poorly secured CCTV cameras across the country, highlighting significant national privacy and security risks.
For more incidents click here!
📢 Cyber News
7. Ransomware Fragmentation Hits Breaking Point
The third quarter of 2025 saw a record 85 active ransomware and extortion groups, indicating the most decentralized ecosystem to date, with 1,590 victims disclosed across 85 leak sites, demonstrating high, sustained activity despite ongoing law-enforcement efforts.
8. Five Help North Korea Evade Sanctions
Five individuals have pleaded guilty to orchestrating illegal IT worker schemes that funneled illicit revenue to North Korea, thereby violating international sanctions. The U.S. Department of Justice announced the pleas, noting the schemes defrauded 136 U.S. companies of $2.2 million and compromised over 18 identities, while concurrent actions seized $15 million in virtual currency tied to North Korean hacking group APT38.
9. US Targets Chinese Crypto Scammers
U.S. federal authorities have launched the Scam Center Strike Force, a new multi-agency task force dedicated to dismantling transnational Chinese cryptocurrency scam networks that annually defraud Americans of an estimated $10 billion. This team, comprising agents from the Department of Justice, FBI, and Secret Service, specializes in investigating and prosecuting large-scale “pig butchering” investment scams, seizing illicit funds, and coordinating with international partners to disrupt the criminal infrastructure across Southeast Asia.
For more news click here
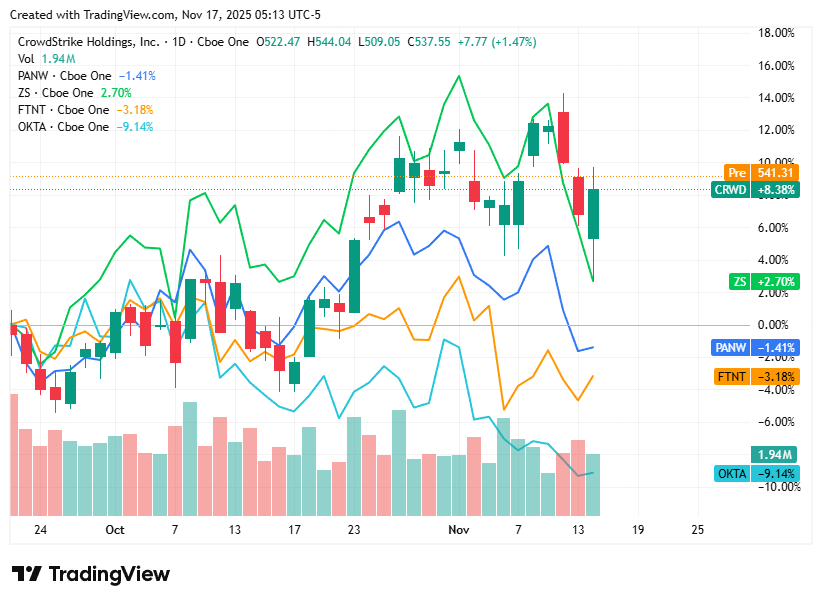
📈Cyber Stocks
On Monday, 17th November, cybersecurity stocks posted a mixed performance as investors weighed strong global demand for cloud, identity, and endpoint security against macroeconomic uncertainty and sector-wide valuation pressure. Geopolitical tensions continued to elevate cyber-risk awareness, supporting spending across federal and enterprise customers, while cautious sentiment toward high-growth tech and hardware refresh concerns created pockets of weakness. Overall, the sector reflected resilience, selective momentum, and measured consolidation as markets assessed year-end security budgets.
CrowdStrike closed at 537.55 dollars and moved higher as strong expectations of an earnings beat and continued demand for AI-driven endpoint protection lifted investor confidence.
Palo Alto Networks closed at 205.25 dollars and finished slightly up, supported by analyst optimism about its long-term platform strategy despite broader caution across network security.
Zscaler closed at 299.45 dollars and traded lower as weakness across high-growth technology stocks outweighed continued momentum in zero-trust adoption and recent analyst upgrades.
Fortinet closed at 82.31 dollars and posted modest gains, helped by solid third-quarter results, although concerns about a slowing firewall refresh cycle and an ongoing legal overhang restricted further upside.
Okta closed at 83.94 dollars and ended marginally positive, driven by strengthening demand for identity security and improving sentiment around upcoming AI-based monetization opportunities.
💡 Cyber Tip
🔥 Firefox 145 and Chrome 142 Fix High Severity Security Flaws
Google and Mozilla have released urgent security updates for Chrome 142 and Firefox 145 to fix multiple high severity vulnerabilities. There is currently no evidence of active exploitation, but experts warn that these flaws could allow remote attacks if left unpatched.
What You Should Do
Update Google Chrome to version 142.0.7444.162 (Linux and macOS) or 142.0.7444.162 or .163 (Windows).
Update Mozilla Firefox to version 145 and apply updates for Firefox ESR 140.5 or ESR 115.30 if you use extended support versions.
Enable automatic browser updates to receive future patches promptly.
Restart your browser after updating to ensure patches are active.
Why This Matters
Chrome 142 fixes a high severity flaw in the V8 JavaScript engine (CVE-2025-13042) which could lead to denial of service or code execution. Firefox 145 fixes 16 vulnerabilities, including nine rated high severity, such as WebGPU boundary issues, a WebAssembly flaw, and a JavaScript Engine miscompilation bug. Prompt patching reduces the risk of remote attacks and strengthens your browser security.
📚 Cyber Book
Cybersecurity 101 by Milo Codde Milligan
That concludes today’s briefing . You can check the top headlines here!
Copyright © 2025 CyberMaterial. All Rights Reserved.
Follow CyberMaterial on:
Substack, LinkedIn, Twitter, Reddit, Instagram, Facebook, YouTube, and Medium.