Cyber Briefing: 2025.11.10
Fake iPhone scam, ClickFix hotel hack, Samsung spyware, SonicWall theft, China US hack, Oracle EBS breach, Maps extortion tool, FBI Tucows case, India cyber gap.
👉 What’s trending in cybersecurity today?
Welcome to Cyber Briefing, the newsletter that informs you about the latest cybersecurity advisories, alerts, incidents and news every weekday.
First time seeing this? Please Subscribe
🚨 Cyber Alerts
1. Lost iPhone Beware Fake Text Claims
The Swiss National Cyber Security Centre (NCSC) is alerting iPhone users to a sophisticated phishing scam that exploits the custom messages set on lost or stolen devices to steal Apple ID credentials. Scammers contact the owner claiming their phone was found, then direct them to a fake Find My website to trick them into entering their login details.
2. ClickFix Phishing Targets Hotel Systems
A widespread phishing campaign is actively targeting the hospitality industry, luring hotel staff with fake ClickFix pages to harvest credentials and deploy the PureRAT malware. Threat actors use compromised email accounts to impersonate platforms like Booking.com, ultimately stealing access to booking systems for either sale on cybercrime forums or to conduct fraud against hotel guests.
3. Samsung Flaw Used To Install Landfall
A zero-day security flaw in Samsung Galaxy Android devices was recently exploited to deploy LANDFALL, a commercial-grade Android spyware, in targeted attacks across the Middle East. This campaign leveraged CVE-2025-21042, an out-of-bounds write vulnerability in a core image component, allowing attackers to execute arbitrary code before Samsung issued a patch in April 2025.
For more alerts, click here!
💥 Cyber Incidents
4. Hackers Steal Sonicwall Cloud Backups
SonicWall confirmed a state-sponsored threat actor stole firewall configuration files from its cloud backup service, impacting all customers using that service. The stolen files contain encrypted credentials and configuration data, prompting the company to urge all affected customers to reset passwords and take immediate action to secure their devices against potential targeted attacks.
5. China Hackers Target US Nonprofit
A China-linked hacking group successfully breached a U.S. policy-focused nonprofit organization in April 2025, demonstrating a persistent interest in entities that influence U.S. government policy on international issues. The attackers aimed to establish long-term, stealthy access to the network, employing sophisticated tactics like DLL sideloading via a legitimate anti-virus component and targeting domain controllers to ensure broad network control.
6. Oracle EBS Hack Hits Nearly 30 Victims
A cluster of the FIN11 profit-driven threat actor, operating publicly as the Cl0p ransomware group, has allegedly impacted nearly 30 organizations in a recent campaign targeting customers of Oracle’s E-Business Suite (EBS) with extortion. The cybercriminals have listed alleged victims, including Harvard University and The Washington Post, and have leaked data supposedly stolen from 18 of them, with evidence suggesting the files originated from an Oracle environment, while the specific EBS vulnerabilities exploited remain under investigation.
For more incidents click here!
📢 Cyber News
7. Google Maps Adds Extortion Reporting
Google has launched a dedicated reporting form on Google Maps for businesses targeted by review bombing—a practice where threat actors post inauthentic negative reviews and then demand a ransom for their removal. This new approach directly combats extortion attempts against listed businesses.
8. FBI Demands Data From Tucows
Archive.today, a controversial snapshot website akin to the Wayback Machine but operating largely without rules, is facing a serious legal challenge from the FBI. The service, often used to bypass paywalls and alleged to disregard copyright, recently posted a cryptic “canary” warning, linking to a US court order demanding its Canadian domain provider, Tucows, hand over comprehensive user and payment data.
9. Cybersecurity Talent Gap Hits 50 Percent
India’s cybersecurity sector is grappling with a severe talent gap of 30-50% across critical roles like cloud security and Zero Trust, driven by a surge in active job openings, now up to 30,000, and the growing adoption of AI. This shortage is most acute at the mid-senior level, leading companies to pay significant salary premiums—up to 60% higher than comparable engineering jobs—for specialized skills like incident response and AI-linked security.
For more news click here
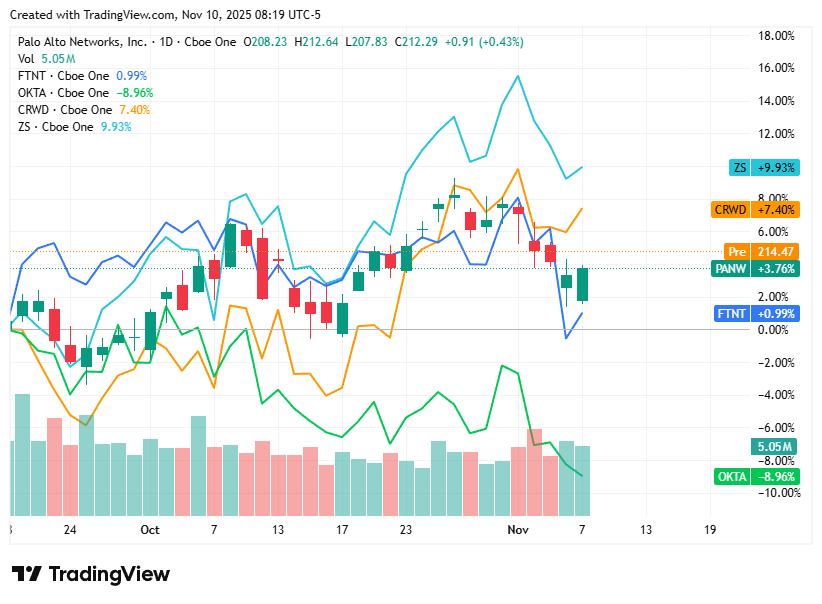
📈Cyber Stocks
On Monday, 10th November, cybersecurity stocks started the week on a positive note, rebounding from last week’s decline as investor confidence returned to the tech sector. Optimism was fueled by strong enterprise spending on AI-powered and zero-trust security solutions, coupled with heightened geopolitical cyber risks driving renewed demand for defense technologies. While a few identity-focused names lagged due to competitive pressures, the broader cybersecurity sector reflected steady upward momentum.
CrowdStrike closed at $539.81, up 1.4%, as investor enthusiasm grew around rising enterprise cybersecurity budgets and continued dominance of its AI-driven Falcon platform.
Zscaler ended at $320.01, up 0.6%, supported by sustained cloud adoption and confidence in its zero-trust architecture amid growing regulatory focus on digital resilience.
Palo Alto Networks finished at $212.29, up 0.4%, with steady gains reflecting optimism around its acquisition strategy and integrated platform expansion.
Okta settled at $85.21, down 0.8%, under pressure from intensified competition in the identity and access management space despite long-term demand growth.
Fortinet closed at $81.79, up 1.6%, benefiting from increased geopolitical cyber threats and continued enterprise investment in network security infrastructure.
💡 Cyber Tip
📱 Lost iPhone: Beware of Fake Text Messages Claiming Your Device Was Found
The Swiss National Cyber Security Centre (NCSC) is warning iPhone users about a phishing scam that targets people who have lost their devices. Scammers are sending fake texts claiming the lost iPhone has been found, directing victims to a fake Find My website to steal their Apple ID credentials.
🔐 What You Should Do
Do not click on links in messages claiming your lost iPhone has been found.
Always check the official Find My app or iCloud.com/find to verify your device’s location.
Ignore texts or emails requesting your Apple ID or password.
Report suspicious messages to Apple and delete them immediately.
⚠️ Why This Matters
These scams exploit the emotional stress of losing a device to trick victims into revealing their login details. Once attackers have your Apple ID credentials, they can access personal data, disable security features, and permanently lock you out of your account.
📚 Cyber Book
The Weakest Link by Arun Vishwanath
That concludes today’s briefing . You can check the top headlines here!
Copyright © 2025 CyberMaterial. All Rights Reserved.
Follow CyberMaterial on:
Substack, LinkedIn, Twitter, Reddit, Instagram, Facebook, YouTube, and Medium.