Cyber Briefing: 2025.11.07
Gootloader returns, CentOS exploit, VS Code malware, US Budget hack, Clop hits WaPo, Hyundai breach, crypto arrests, UK blocks spoofing, Google warns on AI.
👉 What’s trending in cybersecurity today?
Welcome to Cyber Briefing, the newsletter that informs you about the latest cybersecurity advisories, alerts, incidents and news every weekday.
First time seeing this? Please Subscribe
🚨 Cyber Alerts
1. Gootloader Returns With New Tricks
The Gootloader malware operation has resumed its SEO poisoning campaigns after a seven-month break, promoting fake legal document websites to trick users into downloading malicious JavaScript files. These files provide threat actors with initial access to corporate networks, which is typically used for subsequent ransomware attacks.
2. CISA Warns Of CentOS Panel Exploit
The U.S. Cybersecurity & Infrastructure Security Agency (CISA) has issued an urgent warning regarding a severe vulnerability, CVE-2025-48703, in CentOS Web Panel (CWP). Threat actors are actively exploiting this critical flaw, which allows remote, unauthenticated attackers to execute arbitrary shell commands on affected Linux servers simply by knowing a valid username.
CISA has added this high-risk vulnerability to its Known Exploited Vulnerabilities (KEV) catalog, mandating that federal agencies apply necessary security updates or discontinue use of CWP by November 25.
3. Malicious VS Code Extension Found
A malicious Visual Studio Code (VS Code) extension, likely developed using AI (or “vibe-coded”), was flagged for basic ransomware functionality, including file encryption and exfiltration. Microsoft has since removed the extension, “susvsex,” which also used a private GitHub repository for command-and-control (C2) operations.
For more alerts, click here!
💥 Cyber Incidents
4. US Budget Office Hit By Cyberattack
The Congressional Budget Office (CBO) has confirmed it experienced a cybersecurity incident, suspected to be the work of a foreign hacker, which may have exposed sensitive data including communications with congressional offices. The agency stated it took immediate action to contain the breach and is investigating, though some congressional offices have reportedly paused email contact due to security concerns.
5. Clop Claims Washington Post Breach
The Clop Ransomware group, which is known for its big-game hunting and double-extortion tactics, recently announced the successful hack of the prestigious American daily newspaper, The Washington Post. The cybercrime group immediately created a dedicated page for the newspaper on its Tor data leak site, where it declared its intention to leak the stolen data soon. This breach was claimed by the group in mid-October.
6. Hyundai AutoEver Reports Data Breach
The North American subsidiary of Hyundai AutoEver, the IT services division of Hyundai Motor Group, has revealed a data breach stemming from a hacker attack earlier this year.
For more incidents click here!
📢 Cyber News
7. French Police Seize Millions In Crypto
An international cryptocurrency investment scam and money laundering network has been dismantled following a joint European law enforcement operation, resulting in the arrest of nine individuals across Cyprus, Germany, and Spain. Authorities seized over $1.84 million in assets, cash, and crypto, and the suspects are accused of defrauding hundreds of victims for an estimated $700 million in laundered crypto assets.
8. UK Carriers To Block Spoofed Calls
Britain’s major mobile carriers have agreed to upgrade their networks within a year to eliminate the ability of scammers to spoof phone numbers, a key measure under the new Telecoms Charter aimed at combating widespread fraud. This partnership, which includes law enforcement and government agencies, mandates carriers to implement advanced call tracing and indicate when calls originate internationally, making it significantly harder for fraudsters to impersonate trusted organizations and ensuring better support for scam victims.
9. Google Warns AI Will Boost Cybercrime
Google’s Cybersecurity Forecast 2026 warns that the threat landscape is rapidly transforming due to AI, which is now central to both automated, large-scale attacks and advanced defense strategies. Cybercrime is simultaneously expanding, with record-breaking ransomware and data theft incidents exploiting supply chains, virtualization platforms, and sophisticated social engineering tactics.
For more news click here
📈Cyber Stocks
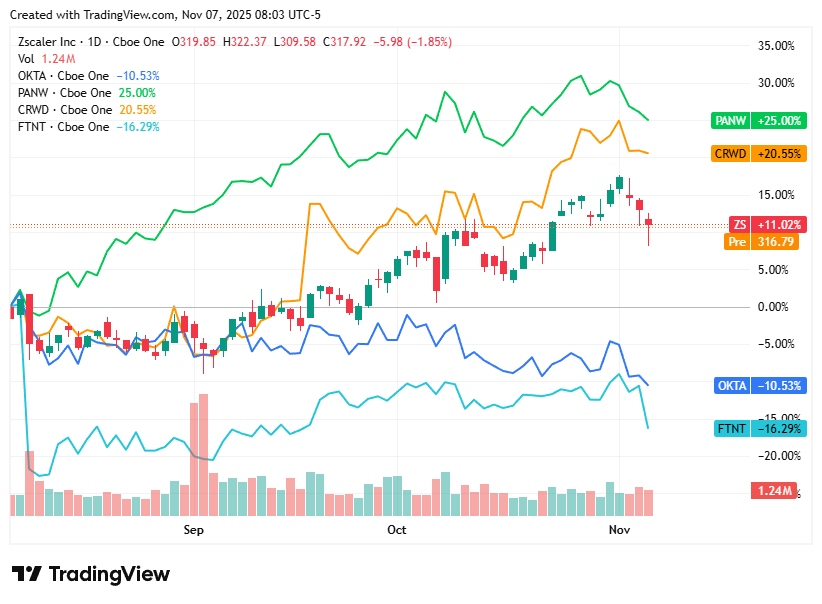
On Friday, 7th November, cybersecurity stocks closed broadly lower as investors booked profits following a strong start to the month. The pullback reflected broader tech market weakness, persistent macroeconomic caution, and renewed focus on valuation risks across high-growth security names. Despite the day’s declines, analysts noted that underlying enterprise demand and AI-driven innovation continue to underpin long-term sector confidence, suggesting this was a period of consolidation rather than concern.
CrowdStrike closed at $532.52, down 0.3%, as investors reassessed elevated valuations even as demand for its AI-powered Falcon platform remained robust.
Zscaler ended at $317.92, down 1.9%, pressured by rotation away from high-growth cloud and zero-trust players amid a cautious tech sentiment.
Palo Alto Networks finished at $211.37, down 0.8%, with investor attention shifting toward integration costs and margin pressures despite strong platform adoption.
Okta settled at $85.87, down 1.4%, as competitive dynamics in identity management and execution risks kept the stock under pressure.
Fortinet closed at $80.54, down 6.3%, sharply lower after concerns surfaced around the slowing firewall refresh cycle, overshadowing broader cybersecurity demand trends.
💡 Cyber Tip
⚠️ CISA Warns of Critical CentOS Web Panel Vulnerability
CISA has warned that threat actors are actively exploiting a critical vulnerability in CentOS Web Panel (CWP), tracked as CVE-2025-48703. The flaw allows remote, unauthenticated attackers to execute arbitrary shell commands on affected servers if they know a valid username. CISA added the vulnerability to its Known Exploited Vulnerabilities catalog and requires federal agencies to patch or stop using CWP by November 25.
🔐 What You Should Do
Apply the vendor patch for CWP immediately or upgrade to a fixed version.
If patching is not possible, take CWP offline or disable the vulnerable file-manager endpoint.
Restrict network access to CWP with IP allow lists and firewall rules.
Rotate credentials and audit user accounts for unauthorized additions.
Search logs for suspicious POST requests to the changePerm endpoint and signs of command execution.
Ensure backups are isolated and verified before restoring any affected systems.
⚠️ Why This Matters
This vulnerability is unauthenticated and easy to exploit. Attackers can gain shell access with only a known username, enabling data theft, ransomware deployment, or persistent access. Rapid patching, access restrictions, and detection are essential to prevent widespread compromise.
📚 Cyber Book
Phishing for Phools by George A. Akerlof
That concludes today’s briefing . You can check the top headlines here!
Copyright © 2025 CyberMaterial. All Rights Reserved.
Follow CyberMaterial on:
Substack, LinkedIn, Twitter, Reddit, Instagram, Facebook, YouTube, and Medium.