Cyber Briefing: 2025.11.06
Russia Hyper-V exploit, Teams flaw, SkyCloak defense hack, Sandworm Ukraine, Qilin Swiss bank, Belgium DDoS, €600M crypto bust, ex-cyber extortion, Singapore caning law.
👉 What’s trending in cybersecurity today?
Welcome to Cyber Briefing, the newsletter that informs you about the latest cybersecurity advisories, alerts, incidents and news every weekday.
First time seeing this? Please Subscribe
🚨 Cyber Alerts
1. Russia Group Exploits Windows HyperV
Curly COMrades threat actors are exploiting Windows Hyper-V to create hidden Alpine Linux virtual machines, which allows them to bypass traditional Endpoint Detection and Response (EDR) tools and covertly deploy custom Linux-based malware for long-term access. This technique, uncovered by Bitdefender and Georgia’s CERT, demonstrates an advanced virtualization-based evasion strategy used by the Russian-linked group to maintain persistence and conduct undetected operations.
2. Teams Bugs Let Hackers Impersonate
A critical security vulnerability has been discovered and patched in the popular Cybersecurity researchers found four flaws in Microsoft Teams that could allow attackers to manipulate conversations and notifications, essentially enabling impersonation and social engineering attacks. Microsoft has since patched these medium-severity vulnerabilities, which allowed malicious actors to alter message content and sender identities without detection, posing a serious risk to user trust and data security.
3. SkyCloak Backdoor Targets Defense Firms
Threat actors are deploying a sophisticated, multi-stage malware campaign, dubbed Operation SkyCloak, primarily targeting the defense sectors of Russia and Belarus through weaponized email attachments. The campaign establishes a persistent backdoor on compromised systems, utilizing OpenSSH and a customized Tor hidden service with obfs4 for communication obfuscation and includes anti-analysis checks to evade sandbox detection.
For more alerts, click here!
💥 Cyber Incidents
4. Sandworm Wipers Hit Ukraines Grain Hub
The Russian state-sponsored hacker group Sandworm (also known as APT44) has recently targeted Ukraine’s government, education, and vital grain sector with multiple families of data-wiping malware
5. Hackers Steal Data From Swiss Bank
The Qilin ransomware gang, a prominent group of Russian hackers, claims to have breached Habib Bank AG Zurich, an international bank based in Switzerland. The attackers allege they stole over 2.5 terabytes of customer data and the bank’s source code, listing the bank on their dark web blog as part of a common tactic to force a ransom payment.
6. Belgian Telecoms Hit By Cyberattack
Pro-Russian hacker group NoName057 claimed responsibility for a brief Distributed Denial of Service (DDoS) cyberattack that disrupted Belgian telecom operators Proximus and Scarlet early Wednesday morning. The group cited recent comments by the Belgian Defense Minister, who had warned Russia that NATO would “flatten” Moscow if it attacked Brussels, as the motivation for the attack
For more incidents click here!
📢 Cyber News
7. Nine Arrested In Crypto Laundering
A major crypto money laundering ring that stole over €600 million was dismantled in a coordinated operation led by Eurojust, resulting in nine arrests across Cyprus, Spain, and Germany. The fraudsters ran numerous fake crypto investment sites, luring victims with promises of high returns via social media, cold calls, and fabricated endorsements before stealing and laundering the funds through complex blockchain transactions.
8. Ex Cyber Employees Extort US Firms
Three Florida men, including two who worked in the cybersecurity field, have been charged by U.S. prosecutors for using BlackCat ransomware to hack and attempt to extort at least five U.S. companies between May and November 2023. Ryan Clifford Goldberg and Kevin Tyler Martin face multiple federal charges of computer hacking and extortion for their alleged roles in the scheme, which successfully netted $1.27 million in cryptocurrency from one medical device company.
9. Singapore Law Imposes Caning For Scams
Singapore’s parliament has passed amendments to its criminal law, introducing mandatory caning for scammers and those involved in scam syndicates, a measure aimed at deterring what the nation calls its “most prevalent crime type.” This new legislation also recalibrates caning for certain other offenses, while simultaneously introducing stiffer penalties for issues like large-scale circulation of sexual media and the doxxing of public servants.
For more news click here
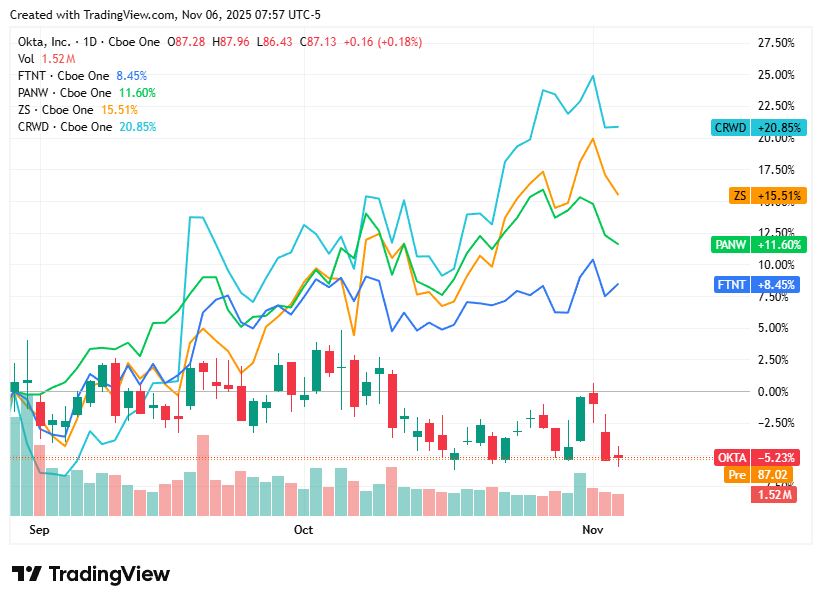
📈Cyber Stocks
On Thursday, 6th November, cybersecurity stocks traded mixed as the market digested recent volatility in the broader tech sector. While renewed investor caution and profit-taking weighed on some high-growth cloud names, steady enterprise demand and sustained geopolitical cyber risks kept the sector broadly resilient. The day’s movement reflected consolidation rather than weakness, with most stocks holding firm on long-term optimism around AI-driven and zero-trust security innovation.
CrowdStrike closed at $534.14, flat on the day, as broader tech headwinds balanced optimism surrounding its AI-powered endpoint protection platform.
Zscaler ended at $323.90, down 1.4%, amid continued investor rotation away from high-growth cybersecurity names and margin sensitivity in cloud segments.
Palo Alto Networks finished at $213.18, down 0.6%, as concerns over acquisition integration offset strong platform adoption momentum.
Okta settled at $87.13, up 0.2%, supported by steady identity-security demand despite persistent competitive challenges in the IAM market.
Fortinet closed at $85.99, up 1.0%, lifted by rising geopolitical tensions and enterprise focus on network defense and threat prevention.
💡 Cyber Tip
💬 Teams Bugs Let Hackers Impersonate Coworkers
Researchers discovered four flaws in Microsoft Teams that let attackers impersonate colleagues, alter messages, and manipulate notifications without detection. The vulnerabilities, rated medium in severity, allowed changes to message content and sender identity, creating serious risks for social engineering. Microsoft has patched the issues under CVE-2024-38197 and related updates.
🔐 What You Should Do
Keep Microsoft Teams and Office apps updated across all devices.
Be cautious with unexpected or suspicious messages, even if they appear to come from trusted coworkers.
Verify unusual requests through another communication channel before taking action.
Report suspicious activity to your IT or security team immediately.
⚠️ Why This Matters
These flaws undermined the trust and authenticity of business communications. Exploiting them could have allowed attackers to spread malware, steal data, or trick users into sharing credentials. Regular patching and user awareness are essential to prevent impersonation-based attacks.
📚 Cyber Book
Social Engineering by Robert W. Gehl & Sean T. Lawson
That concludes today’s briefing . You can check the top headlines here!
Copyright © 2025 CyberMaterial. All Rights Reserved.
Follow CyberMaterial on:
Substack, LinkedIn, Twitter, Reddit, Instagram, Facebook, YouTube, and Medium.