Cyber Briefing: 2025.11.05
SmudgedSerpent targets US experts, React Native flaw, Post SMTP exploit, Apache denies hack, Nikkei breach, UK water attacks, US sanctions DPRK, LAPSUS$ alliance, €300M fraud bust.
👉 What’s trending in cybersecurity today?
Welcome to Cyber Briefing, the newsletter that informs you about the latest cybersecurity advisories, alerts, incidents and news every weekday.
First time seeing this? Please Subscribe
🚨 Cyber Alerts
1. Smudged Serpent Targets US Experts
A newly identified threat group, UNK_SmudgedSerpent, executed cyberattacks against academics and foreign policy experts between June and August 2025, during a period of intense geopolitical strain between Iran and Israel. The group utilized domestic political topics, such as societal changes in Iran and scrutiny of the IRGC, as lures in their campaigns, which share tactical similarities with established Iranian cyber espionage groups like Charming Kitten and MuddyWater.
2. React Native CLI Flaw Exposed
A critical security vulnerability has been discovered and patched in the popular @react-native-community/cli npm package, enabling remote attackers to potentially execute malicious operating system (OS) commands without authentication on a developer’s machine. Tracked as CVE-2025-11953 with a critical CVSS score of 9.8, the flaw exists because the development server used by React Native, called Metro, binds to external interfaces by default and exposes a vulnerable endpoint. Developers using the affected package, which is maintained by Meta and sees millions of weekly downloads, are strongly urged to update immediately to version 20.0.0 or later to mitigate the risk of remote OS command injection.
3. Post SMTP Plugin Hijacks Admins
Threat actors are currently exploiting a critical vulnerability in the Post SMTP plugin affecting over 400,000 WordPress sites, with the goal of gaining complete control by hijacking administrator accounts. The popular email delivery solution, marketed as a reliable replacement for the default WordPress mail function, has a flaw that allows unauthenticated attackers to read sensitive email logs, which can include administrator password reset links.
For more alerts, click here!
💥 Cyber Incidents
4. Apache OpenOffice Denies Breach
The Apache Software Foundation (ASF) is investigating claims by the Akira ransomware group that it breached and stole 23 GB of sensitive corporate and employee data from the Apache OpenOffice project. The ASF, however, strongly disputes these claims, stating it doesn’t even possess the types of confidential data the threat actors allege to have exfiltrated.
5. Nikkei Data Breach Hits 17000
Japanese media company Nikkei recently disclosed that hackers accessed employee Slack accounts, stealing personal information and chat histories belonging to over 17,000 users, including employees and business partners. The breach was traced back to infostealer malware on an employee’s personal computer that compromised their Slack credentials, although the company confirmed that no information related to sources or reporting activities was compromised.
6. Hackers Target UK Water Suppliers
Since the start of 2024, Britain’s drinking water suppliers have endured five cyberattacks, a record number for a two-year period, as reported to the Drinking Water Inspectorate (DWI). While none of the breaches affected the safe supply of drinking water itself, the incidents underscore the heightened cyber threat to the country’s critical infrastructure, which officials are now seeking to address through updated legislation.
For more incidents click here!
📢 Cyber News
7. US Sanctions 10 North Korean Entities
The U.S. Treasury Department sanctioned eight individuals and two entities involved in North Korea’s global financial network for laundering illicit revenue from cybercrime and fraudulent overseas IT worker schemes. Treasury officials assert that these actions directly target the facilitators enabling the DPRK regime to move millions of dollars through digital and traditional channels to fund its nuclear weapons programs.
8. Cybercrime Groups Join Forces
A newly formed cybercrime collective, uniting the notorious groups Scattered Spider, LAPSUS$, and ShinyHunters, has been relentlessly establishing a public presence on Telegram since August 8, 2025. Despite platform moderation, the group, dubbed Scattered LAPSUS$ Hunters (SLH), has created and recreated at least 16 different Telegram channels to market their extortion-as-a-service (EaaS) model, disseminate messaging, and coordinate attacks against organizations.
9. Credit Card Fraud Ring Busted
International law enforcement, in a massive operation called “Chargeback,” dismantled three sophisticated credit card fraud and money laundering networks responsible for over €300 million in losses and impacting 4.3 million cardholders across 193 countries. The joint action, led by German authorities and coordinated by Eurojust and Europol, resulted in the arrest of 18 people, including executives from major German payment service providers who allegedly facilitated the crime by enabling access to payment infrastructure.
For more news click here
📈Cyber Stocks
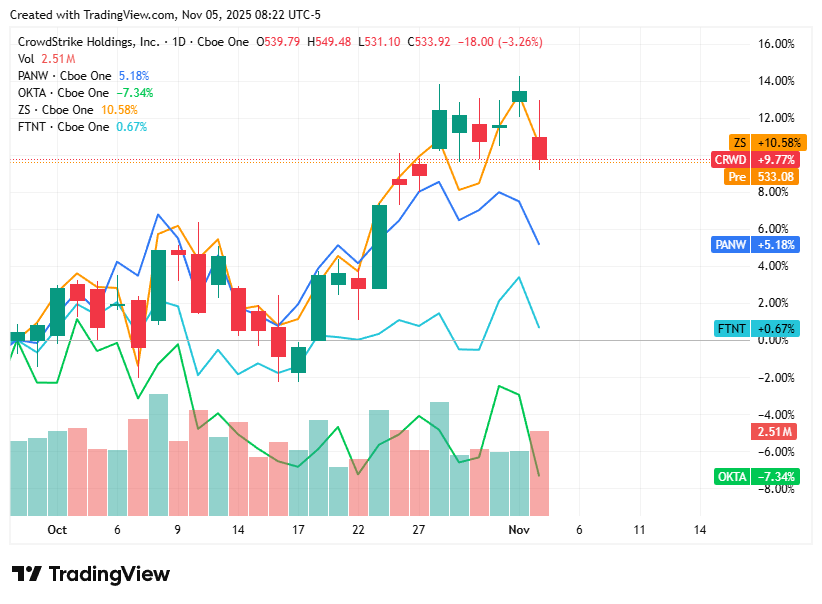
On Wednesday, 5th November, cybersecurity stocks declined across the board, tracking a broader pullback in the technology sector. Investor sentiment weakened as concerns over stretched valuations, profit-taking, and macroeconomic uncertainty outweighed continued optimism in AI-driven and zero-trust security adoption. Despite the sell-off, analysts noted that underlying demand for enterprise cybersecurity remains robust, signaling a healthy long-term outlook beyond short-term volatility.
CrowdStrike closed at $533.92, down 3.3%, as investors reassessed high valuations amid uncertainty around sustaining its rapid AI-driven growth trajectory.
Zscaler ended at $328.30, down 2.3%, reflecting a sector-wide rotation out of high-growth cloud names and increased margin scrutiny.
Palo Alto Networks finished at $214.52, down 2.1%, pressured by concerns over integration costs and near-term margin impacts from recent acquisitions.
Okta settled at $86.97, down 4.5%, extending losses on competitive pressures in identity management and investor caution over execution risk.
Fortinet closed at $85.22, down 2.6%, mirroring broader tech weakness as questions about firewall upgrade cycles limited support from geopolitical demand tailwinds.
💡 Cyber Tip
💥 Post SMTP Plugin Hijacks Admins
Hackers are exploiting a critical flaw (CVE-2025-11833) in the Post SMTP WordPress plugin, used by over 400,000 sites, to hijack administrator accounts. The vulnerability lets unauthenticated attackers read email logs containing password reset links, allowing them to take full control of affected websites. A patched version (3.6.1) is available, but nearly half of users have yet to update, leaving thousands of sites exposed.
🔐 What You Should Do
Update Post SMTP to version 3.6.1 immediately or disable the plugin until patched.
Check for unauthorized logins or password changes in your admin accounts.
Delete all email logs that may contain sensitive information.
Enable multi-factor authentication (MFA) for admin users.
Regularly audit installed plugins and keep them updated to the latest versions.
⚠️ Why This Matters
This vulnerability allows attackers to take over entire WordPress sites without authentication. With active exploitation already underway, updating or disabling the plugin is critical to prevent account hijacking and full site compromise.
📚 Cyber Book
Practical Internet of Things Security by Brian Russell, Drew Van Duren
That concludes today’s briefing . You can check the top headlines here!
Copyright © 2025 CyberMaterial. All Rights Reserved.
Follow CyberMaterial on:
Substack, LinkedIn, Twitter, Reddit, Instagram, Facebook, YouTube, and Medium.