Cyber Briefing: 2025.11.04
China Tick exploit, Airstalk malware, Linux flaw, Balancer $128M hack, Qilin hits Malibu, cargo thefts, Google AI mode, Android blocks scams, Proton breach report.
👉 What’s trending in cybersecurity today?
Welcome to Cyber Briefing, the newsletter that informs you about the latest cybersecurity advisories, alerts, incidents and news every weekday.
First time seeing this? Please Subscribe
🚨 Cyber Alerts
1. China Linked Tick Exploits Lanscope
The cyber espionage group Tick (also known as Bronze Butler or Swirl Typhoon), which is believed to be Chinese and focuses on East Asia, has been actively exploiting a critical, recently disclosed vulnerability in Motex Lanscope Endpoint Manager (CVE-2025-61932, CVSS 9.3) to compromise systems. This exploitation allows the attackers to execute arbitrary commands with SYSTEM privileges and has been confirmed to drop a sophisticated backdoor called Gokcpdoor, along with the Havoc post-exploitation framework and other tools, primarily targeting sectors in Japan.
2. Nation State Hackers Deploy Airstalk
A suspected nation-state threat actor is deploying new Airstalk malware through a likely supply chain attack, using it to establish a covert command-and-control channel by misusing the AirWatch API for mobile device management. This sophisticated malware, tracked as CL-STA-1009, is capable of extensive espionage, including harvesting browser data like cookies and history, and capturing screenshots from compromised systems.
3. CISA Warns Linux Flaw Exploited
The Linux kernel vulnerability CVE-2024-1086, a high-severity privilege escalation flaw, is actively being exploited in ransomware attacks, allowing local attackers to gain root access and take over compromised systems. This use-after-free weakness in the netfilter: nf_tables component affects numerous major Linux distributions running kernel versions between 3.15 and 6.8-rc1 and requires immediate patching.
For more alerts, click here!
💥 Cyber Incidents
4. Balancer Suffers 128 Million Exploit
Decentralized exchange and liquidity protocol Balancer has suffered a major security breach, with total losses now exceeding $128.6 million in digital assets. This significant exploit, which targeted vaults across multiple chains including Sonic, Polygon, and Base networks, underscores persistent vulnerabilities in the DeFi sector
5. Malibu Boats Australia Hit By Ransomware
Malibu Boats Australia, a manufacturer of water sports towboats, has reportedly become a victim of a recent ransomware attack with the Qilin group listing the company on its dark web leak site. Qilin alleges it stole 160 gigabytes of data.
6. Cybercriminals Exploit Remote Monitoring
Cybercriminals are increasingly attacking trucking and logistics companies to gain access using remote monitoring software, ultimately aiming to steal physical cargo freight for financial profit. This threat cluster is collaborating with organized crime to breach the surface transportation industry, with the primary targets for these cyber-enabled heists being food and beverage products.
For more incidents click here!
📢 Cyber News
7.Google Search AI Mode Knows Everything
Google is planning to make its ‘AI mode’ in Search highly personalized by allowing it to access user data from services like Gmail and Drive, which will be an opt-in feature. This enhanced personalization aims to use your private information to deliver truly customized responses, such as summarizing email details or creating schedules based on your documents.
8. Google AI Blocks 10B Scam Messages
Google’s Android scam defenses are stopping over 10 billion malicious calls and messages monthly, alongside blocking over 100 million suspicious RCS numbers from sending scams.
9. Proton Launches Data Breach Observatory
Proton has established the Data Breach Observatory to highlight severe online security issues, revealing that over 300 million stolen credentials are actively circulating on dark web cybercrime markets. This massive exposure disproportionately affects small businesses, with four out of five experiencing a recent data breach that can cost over a million dollars, often going unreported for months or years.
For more news click here
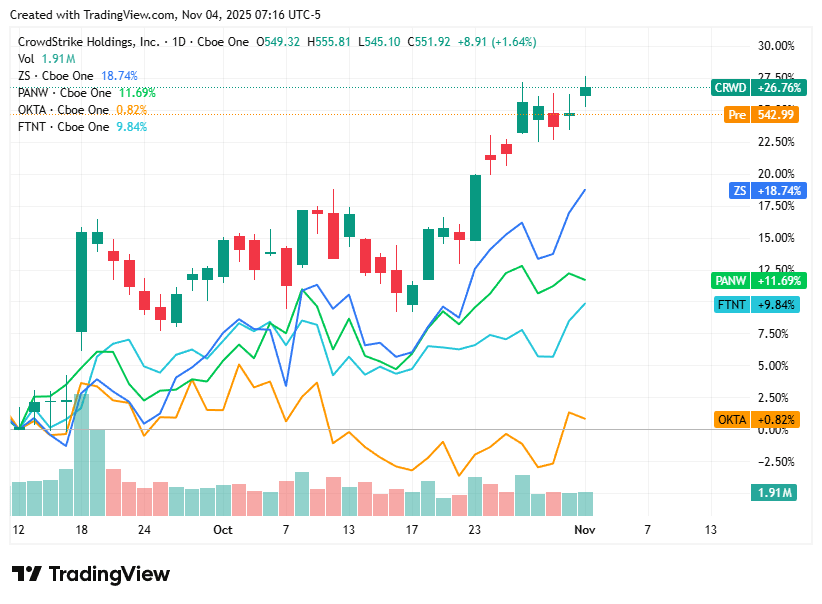
📈Cyber Stocks
On Tuesday, 4th November, cybersecurity stocks posted modest gains as investor sentiment warmed amid elevated cyber-threat awareness and improving enterprise spend, even as valuation discipline and macro headwinds kept gains in check.
CRWD (CrowdStrike) closed higher, buoyed by optimism around its AI-powered Falcon endpoint platform and rising demand for advanced threat intelligence.
ZS (Zscaler) advanced, supported by accelerating enterprise cloud migration and the growing prominence of its zero-trust architecture.
PANW (Palo Alto Networks) edged up, helped by confidence in its platform consolidation strategy and recent M&A positioning in identity and cloud security.
OKTA (Okta) moved slightly lower, weighed by competition in the identity-access market and investor caution about execution despite strong structural demand.
FTNT (Fortinet) posted a modest gain, supported by persistent geopolitical cyber-risk and demand for network-security solutions, though concerns linger over its firewall-upgrade cycle.
💡 Cyber Tip
📱 High Severity Linux Vulnerability Now Actively Exploited By Ransomware Gangs
A critical Linux kernel vulnerability, CVE-2024-1086, is currently being exploited by ransomware gangs. This high-severity privilege escalation flaw allows attackers with local access to gain root-level control, potentially leading to full system compromise and network-wide impact.
🔐 What You Should Do
Identify Vulnerable Systems: Check all Linux systems running kernel versions 3.15 through 6.8-rc1.
Apply Patches Immediately: Update to the latest patched kernel released by your distribution (Debian, Ubuntu, Fedora, Red Hat, etc.).
Limit Local Access: Restrict user accounts and services that could allow untrusted local access until patches are applied.
Monitor Logs & Alerts: Watch for unusual privilege escalation attempts or unexpected root-level activity.
Review Incident Response Plans: Ensure backup and recovery procedures are up-to-date in case of compromise.
⚠️ Why This Matters
Exploitation of CVE-2024-1086 allows attackers to take full control of Linux systems, disable security defenses, install malware, and move laterally across networks. With a public proof-of-concept available, the risk of ransomware attacks and data breaches is high and immediate, making rapid patching critical to protecting infrastructure.
📚 Cyber Book
IoT Penetration Testing Cookbook by Aaron Guzman, Aditya Gupta
That concludes today’s briefing . You can check the top headlines here!
Copyright © 2025 CyberMaterial. All Rights Reserved.
Follow CyberMaterial on:
Substack, LinkedIn, Twitter, Reddit, Instagram, Facebook, YouTube, and Medium.