Cyber Briefing: 2025.11.03
BankBot and DeliveryRAT exposed, Kimsuky HttpTroy, China PlugX attacks, Penn breach claim, rogue ransomware staff, massage scam, Edge scareware fix, Meduza arrests, Apple Wallet ID.
👉 What’s trending in cybersecurity today?
Welcome to Cyber Briefing, the newsletter that informs you about the latest cybersecurity advisories, alerts, incidents and news every weekday.
First time seeing this? Please Subscribe
🚨 Cyber Alerts
1. BankBot YNRK And DeliveryRAT Exposed
Cybersecurity researchers have uncovered BankBot-YNRK and DeliveryRAT, two potent Android trojans designed to steal sensitive data from infected devices. BankBot-YNRK, in particular, employs sophisticated anti-analysis techniques, targets specific Android versions and device models, and leverages accessibility services to gain elevated privileges for data harvesting and initiating fraudulent transactions.
2. HTTPTroy Backdoor Poses As VPN Invoice
The North Korea-linked hacking group Kimsuky recently deployed a novel backdoor, dubbed HttpTroy, in a targeted spear-phishing attack against a single victim in South Korea. Simultaneously, the infamous Lazarus Group was caught using two variants of the Comebacker dropper to deploy an upgraded version of its potent BLINDINGCAN remote access trojan in an attack detected mid-chain against two victims in Canada.
3. China Linked Hackers Exploit Shortcut In
A China-affiliated threat actor, UNC6384, launched a new wave of attacks between September and October 2025 targeting European diplomatic and government organizations using spear-phishing emails that exploit an unpatched Windows shortcut vulnerability (ZDI-CAN-25373/CVE-2025-9491) to deploy the PlugX Remote Access Trojan (RAT). This campaign, which targeted entities in countries like Hungary, Belgium, Italy, the Netherlands, and Serbia, uses diplomatic-themed lures to entice victims into a multi-stage attack chain that ultimately grants the attackers comprehensive remote access and system reconnaissance capabilities.
For more alerts, click here!
💥 Cyber Incidents
4. Penn Hacker Claims Major Data Breach
A hacker claimed a data breach at the University of Pennsylvania (Penn) was far more extensive than the university initially acknowledged, alleging they exposed data on 1.2 million students, alumni, and donors and accessed internal documents. The incident began with offensive emails sent to the Penn community, which the university described as “fraudulent.”
5. FBI Says Rogue Workers Behind Hacks
Two employees from DigitalMint, a company specializing in negotiating cyber-attack ransoms, along with an accomplice from another firm, are facing federal charges for allegedly conducting five of their own ransomware attacks and netting over $1 million in an extortion plot. Prosecutors accuse the rogue insider employees of a Chicago-area cyber-incident response company of using their expertise to carry out a piracy scheme designed to extort millions from targeted businesses.
6. Hackers Extort 350K From Massage Clients
A crime ring that stole data from massage parlor owners’ phones to scam clients out of millions of won has been busted by police. The suspects blackmailed victims by threatening to release non-existent “massage videos” if they didn’t pay.
For more incidents click here!
📢 Cyber News
7. Microsoft Edge Adds Scareware Sensor
Microsoft is enhancing its Edge web browser with a new scareware sensor that works alongside Defender SmartScreen to detect tech support scam pages and block them globally much faster. This new feature aims to quickly flag the aggressive, full-screen scam tactics, like fake virus alerts or fraudulent law enforcement warnings, that try to trick users into calling fake support or paying a fine.
8. Meduza Stealer Malware Admins Arrested
Russian authorities have arrested three individuals in Moscow suspected of creating and operating the Meduza Stealer information-stealing malware. This action, announced by a Russian Ministry of Internal Affairs official, follows an investigation into the group who had been distributing the sophisticated malware-as-a-service on hacker forums for about two years, leading to the theft of credentials and cryptocurrency data from victims globally.
9. Apple Pay VP Unveils Wallet Updates
Apple is expanding its Wallet app to include a new digital ID feature allowing U.S. users to create a verified ID using their passport. This feature, which will roll out in a future software update after the iOS 26 release, will enable travelers to use their digital passport ID at select TSA checkpoints for domestic travel, streamlining the verification process alongside existing digital boarding passes.
For more news click here
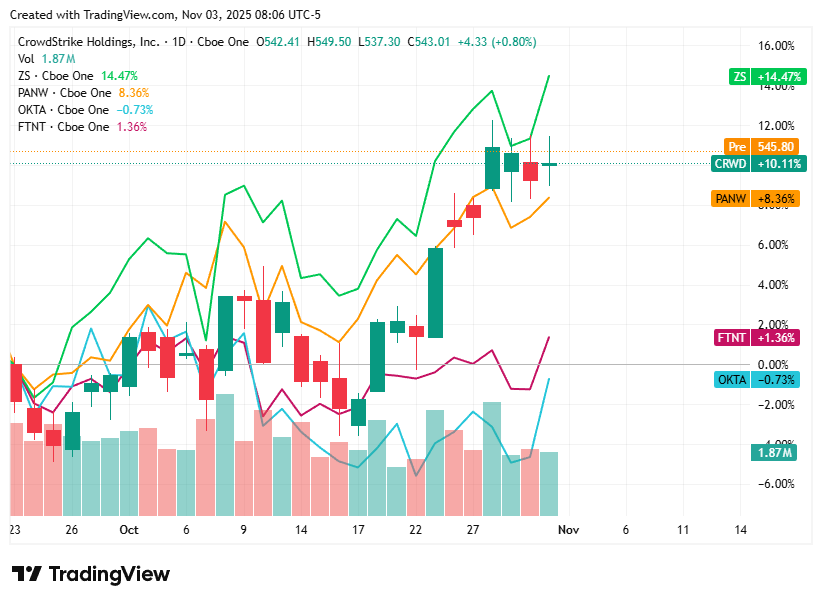
📈Cyber Stocks
On Monday, 3rd November, cybersecurity stocks started the new week on a positive note, supported by rising enterprise security budgets and optimism around AI-driven defense technologies. Investor sentiment improved as geopolitical cyber risks and regulatory emphasis on critical infrastructure protection continued to highlight the sector’s long-term resilience. Overall, most cybersecurity names posted modest gains, reflecting a steady start to November’s trading despite broader market uncertainty.
CrowdStrike closed higher, lifted by sustained investor enthusiasm for its AI-powered Falcon platform and growing enterprise adoption across global markets.
Zscaler ended in positive territory, buoyed by increasing migration to zero-trust architectures and upbeat analyst outlooks on its cloud-native growth trajectory.
Palo Alto Networks finished slightly up, as confidence in its integrated platform and recent strategic acquisitions continued to drive investor interest.
Okta settled higher, benefiting from renewed focus on identity and access management solutions amid tightening data protection mandates.
Fortinet edged upward, supported by ongoing geopolitical tensions that reinforced demand for its network defense and threat prevention technologies.
💡 Cyber Tip
📱 BankBot YNRK and DeliveryRAT Steal Data from Android Phones
Researchers have uncovered two Android trojans, BankBot-YNRK and DeliveryRAT, that steal sensitive data and enable financial fraud. BankBot-YNRK is highly evasive, targets specific device models and Android versions, uses accessibility services to gain elevated privileges, mutes audio to avoid alerts, and maintains persistence to harvest contacts, messages, location data, clipboard contents, and banking credentials.
🔐 What You Should Do
Update your device to Android 14 or later where possible.
Avoid installing apps from third-party sites or unknown APKs.
Disable accessibility and device admin access for untrusted apps.
Use Google Play Protect or a trusted mobile security app to scan for malware.
Revoke suspicious permissions and uninstall unknown apps immediately.
If you suspect infection, disconnect from the internet, back up data, and perform a factory reset.
Monitor bank and crypto accounts for suspicious transactions and enable multi-factor authentication
⚠️ Why This Matters
These trojans are stealthy and focused on financial theft. By abusing accessibility features and persisting after reboot, they can silently steal credentials and execute unauthorized transactions. Keeping your device updated, restricting permissions, and avoiding sideloaded apps are your best defenses.
📚 Cyber Book
Little Black Book of Safety by Keisha Gebre
That concludes today’s briefing . You can check the top headlines here!
Copyright © 2025 CyberMaterial. All Rights Reserved.
Follow CyberMaterial on:
Substack, LinkedIn, Twitter, Reddit, Instagram, Facebook, YouTube, and Medium.