Cyber Briefing: 2025.10.31
Dassault, XWiki exploited, CISA-NSA warn, NFC malware surge, Merkle hack, Ribbon breach, EY leak, Conti extradition, Palantir suit, Pixel hackable.
👉 What’s trending in cybersecurity today?
Welcome to Cyber Briefing, the newsletter that informs you about the latest cybersecurity advisories, alerts, incidents and news every weekday.
First time seeing this? Please Subscribe
🚨 Cyber Alerts
1. Active Exploits Hit Dassault And XWiki
Threat actors are currently exploiting multiple security flaws in Dassault Systèmes DELMIA Apriso and XWiki, prompting alerts from the U.S. Cybersecurity and Infrastructure Security Agency (CISA) and VulnCheck. For DELMIA Apriso, a critical exploit chain involving missing authorization (CVE-2025-6205, CVSS 9.1) and code injection (CVE-2025-6204, CVSS 8.0) allows attackers to gain privileged access and execute arbitrary code, leading to a full application compromise.
2. CISA And NSA Warn To Secure Microsoft
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) and the National Security Agency (NSA), collaborating with partners from Australia and Canada, have issued joint guidance to strengthen the security of on-premise Microsoft Exchange Server instances against cyberattacks. The advice emphasizes restricting administrative access, using multi-factor authentication, and adopting Zero Trust (ZT) security principles to safeguard critical enterprise communications and functions.
3. NFC Relay Malware Surge In Europe
NFC relay malware is rapidly spreading in Eastern Europe, with over 760 malicious Android apps recently discovered stealing payment card information by abusing the Host Card Emulation (HCE) feature. Unlike traditional banking trojans, this sophisticated technique either emulates contactless cards or manipulates payment responses in real-time to authorize fraudulent transactions at point-of-sale terminals without the victim’s physical card.
For more alerts, click here!
💥 Cyber Incidents
4. Merkle Hit By Major Cyberattack
The global marketing giant Dentsu confirmed that its U.S. subsidiary, Merkle, was hit by a cyberattack, which forced the company to take certain systems offline as part of its immediate response. The breach resulted in the theft of files exposing sensitive personal, payroll, and client information belonging to current and former employees.
5. Ribbon Breached By State Hackers
A key provider of networking and secure communications to the U.S. government and major telecom companies globally, Ribbon Communications, disclosed that nation-state hackers breached its IT network, with access dating back to December 2024. The company did not discover the intrusion until September 2025, and though the ongoing investigation has found no evidence of theft of “material information,” the attackers did manage to access files belonging to several customers stored on two company laptops.
6. EY Data Leak On Microsoft Azure
A massive 4TB SQL Server backup file belonging to global accounting firm Ernst & Young (EY) was found publicly accessible on Microsoft Azure, an exposure discovered by Neo Security that highlights the risk of sensitive data being inadvertently left vulnerable to automated internet scanners. Although EY quickly secured the file and stated no client or confidential data was impacted, the incident underscores how even large, well-resourced organizations must implement continuous cloud visibility to prevent brief data exposures that can lead to rapid compromise by modern botnets.
For more incidents click here!
📢 Cyber News
7. Ukrainian Extradited Over Ransomware
A Ukrainian national believed to be a key member of the Conti ransomware operation, 43-year-old Oleksii Oleksiyovych Lytvynenko, has been extradited to the United States from Ireland to face federal charges. Lytvynenko is accused of controlling stolen victim data and sending ransom demands in double extortion attacks between 2020 and 2022, facing up to 25 years in prison if convicted of wire fraud and computer fraud conspiracy.
Palantir has filed a lawsuit in the Southern District of New York against two former employees, Radha Jain and Joanna Cohen, alleging they breached non-compete agreements to launch a “copycat” business called Percepta, which is backed by General Catalyst. The company claims the pair weaponized their insider knowledge, including access to Palantir’s “crown jewels” like its source code and customer workflows, to steal trade secrets and harm the company.
9. Pixels Vulnerable To Cellebrite Hacking
Smartphones now hold a wealth of personal information and have improved security, but companies like Cellebrite provide law enforcement with tools capable of bypassing these defenses on various devices. The specifics of these vulnerabilities are usually secret, but an anonymous source recently leaked a Cellebrite briefing detailing which of Google’s Pixel phones are susceptible to their hacking technology.
For more news click here
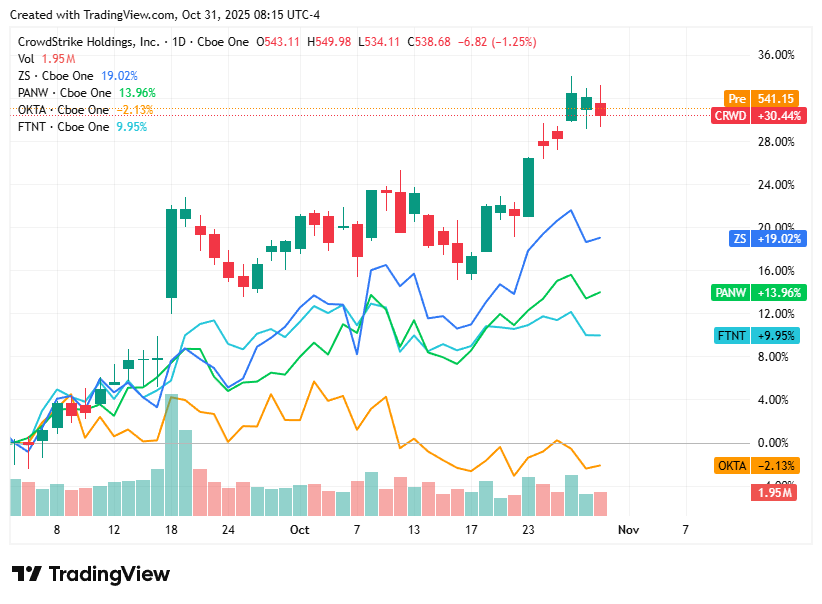
📈Cyber Stocks
On Friday, 31st October, cybersecurity stocks ended the week on a mixed note as investors weighed strong sector fundamentals against broader market volatility. While steady enterprise demand for AI-enhanced and zero-trust solutions kept the group resilient, profit-taking and valuation pressures persisted across high-growth tech names. The day’s trading reflected consolidation rather than weakness, underscoring the sector’s stability amid shifting global and macroeconomic conditions.
CrowdStrike closed at $538.68, down 1.2%, as elevated valuations and softer tech sentiment offset optimism around its expanding Falcon AI platform.
Zscaler ended at $322.04, up 0.3%, supported by continued enterprise migration toward zero-trust cloud frameworks and positive analyst commentary.
Palo Alto Networks finished at $218.27, up 0.5%, lifted by investor confidence in its AI-driven platform consolidation and steady acquisition momentum.
Okta settled at $87.91, up 0.3%, posting modest gains as identity security remains a growing enterprise priority despite competitive headwinds.
Fortinet closed at $84.20, flat on the day, with stable demand for network defense tempered by concerns over slowing firewall refresh cycles.
💡 Cyber Tip
CISA and NSA Warn to Secure Microsoft Exchange
CISA and the NSA, along with partners from Australia and Canada, have issued new guidance urging organizations to secure or decommission on-premises Microsoft Exchange servers. Attackers continue to target outdated or misconfigured systems, making them high-risk entry points. The agencies recommend enabling multi-factor authentication, enforcing least privilege, and adopting Zero Trust principles to strengthen defenses.
🔐 What You Should Do
Keep Exchange and Windows fully patched, disable unnecessary remote PowerShell access, and restrict admin privileges.
Enable TLS, HSTS, and Extended Protection for encryption and authentication.
Use antivirus, AMSI, and EDR tools to detect and block attacks.
Ensure WSUS servers are patched for CVE-2025-59287 and monitor for suspicious PowerShell activity.
⚠️ Why This Matters
Unsecured Exchange and WSUS servers are prime targets for cyberattacks. Following the agencies’ recommendations helps prevent remote code execution, data theft, and persistent intrusions.
📚 Cyber Book
7 Days To Remove Your Digital Footprint by G Davila
That concludes today’s briefing . You can check the top headlines here!
Copyright © 2025 CyberMaterial. All Rights Reserved.
Follow CyberMaterial on:
Substack, LinkedIn, Twitter, Reddit, Instagram, Facebook, YouTube, and Medium.