Cyber Briefing: 2025.10.30
AI cloaking, Windows flaw patch, npm malware, Canada ICS breach, Tas Gov data leak, Family Health hack, cities drop Flock, FINTOCH arrest, Vermont hacker probation.
👉 What’s trending in cybersecurity today?
Welcome to Cyber Briefing, the newsletter that informs you about the latest cybersecurity advisories, alerts, incidents and news every weekday.
First time seeing this? Please Subscribe
🚨 Cyber Alerts
1. Cloaked AI Attack Makes Crawlers Cite Lies
A new threat called AI-targeted cloaking allows attackers to manipulate what agentic AI web browsers, like those in ChatGPT and Perplexity, see on websites by serving them different content than human users. This simple technique, which exposes AI models to context poisoning attacks, can be used as a powerful misinformation weapon to undermine trust and introduce bias in AI-generated outputs and decision systems.
2. Windows Cloud Files Minifilter Exploited
Microsoft has fixed a critical race condition vulnerability ($CVE-2025-55680$) in the Windows Cloud Files Minifilter driver ($cldflt.sys$) that could allow a low-privileged local attacker to escalate privileges to SYSTEM level and create arbitrary files in restricted directories, primarily through DLL side-loading. The flaw, discovered by Exodus Intelligence, stems from a Time-of-Check to Time-of-Use (TOCTOU) weakness that allows the attacker to alter a file path after it has been validated but before the file is created, bypassing security checks and achieving code execution in the kernel context.
3. PhantomRaven Npm Campaign Hides Bad Code
A sophisticated malware campaign, dubbed PhantomRaven, has compromised developer credentials by deploying over 126 malicious npm packages with more than 86,000 total downloads since August 2025. This attack pioneered the use of Remote Dynamic Dependencies to conceal its true malicious payload—a script that harvests npm tokens, GitHub credentials, and CI/CD secrets—from standard security and static analysis tools.
For more alerts, click here!
💥 Cyber Incidents
4. Canada Warns Hackers Breach Critical ICS
Canadian authorities have issued an urgent alert after cybercriminals compromised internet-accessible Industrial Control Systems (ICS) across the nation’s critical infrastructure, with confirmed attacks on water facilities, energy companies, and agricultural operations. These coordinated incidents, often driven by hacktivists seeking attention, reveal dangerous security vulnerabilities and raise serious concerns about the potential for widespread service failures across Canada’s essential services.
5. Tasmanian Gov Agencies Hit By Cyber Attack
Student data may have been compromised. A recent cyberattack on ReadyTech’s VETtrak student management software—used by multiple Tasmanian government agencies, including the Department for Education—resulted in the theft of pupil data. While initially stating no sensitive information was accessed, ReadyTech later confirmed that hackers posted a small number of documents containing personal information online, prompting the company to notify authorities and the government to warn citizens about potential fraud.
6. Family Health West Hit By Cyberattack
Family Health West Hospital in Fruita experienced a cyberattack on Tuesday morning, forcing a shutdown of electronic systems, but patient care remains unaffected due to staff switching to manual operations. The hospital reported no evidence of patient or employee data loss or encryption, and its IT department is working with external cybersecurity experts to securely restore systems.
For more incidents click here!
📢 Cyber News
7. Cities Roll Back License Plate Cameras
Cities across the country are moving to pause or end contracts with Flock Safety, a manufacturer of automated license plate reader (ALPR) cameras, following reports that the company has shared data with federal immigration authorities
8. Alleged FINTOCH Scam Mastermind Arrested
Liang Ai-Bing, the alleged architect of the $\mathbf{$31}$ million FINTOCH crypto Ponzi scheme, was apprehended by Thai authorities in a luxury Bangkok residence on October 29, 2025, following a collaborative cross-border intelligence effort. The Chinese national now faces additional weapons charges after police discovered an unlicensed pistol and ammunition during the raid at his long-term rental home.
9. Vermont Hacker Avoids Jail For Data Theft
A Vermont man, Nicholas Moses, was sentenced to four years of probation for operating a massive international hacking scheme that stole personal data and passwords from over 65,000 victims globally using the SmokeLoader malware. Moses, who sold the stolen credentials for as little as $1 to $5 each, received the probationary sentence after pleading guilty and with both the prosecution and defense citing his mental health challenges and cooperation.
For more news click here
📈Cyber Stocks
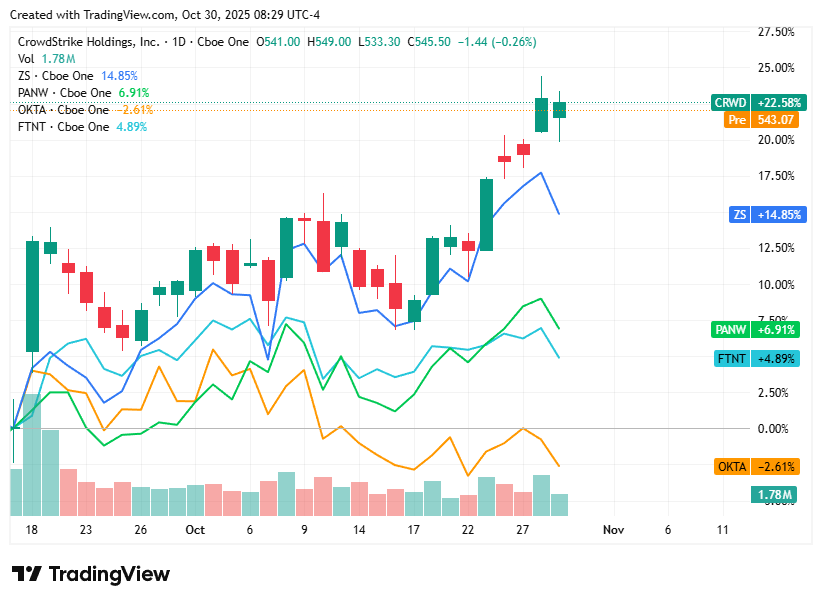
On Thursday, 30th October, cybersecurity stocks ended lower, mirroring weakness across the broader technology market. Investor sentiment cooled as profit-taking and renewed concerns over high valuations weighed on growth-oriented tech names, despite strong underlying demand for AI-driven and zero-trust security solutions. The pullback reflected consolidation rather than fundamental weakness, as the sector remains supported by geopolitical tensions and rising enterprise cybersecurity budgets.
CrowdStrike closed at $545.50, down 0.2%, as investors took a breather following recent highs amid persistent valuation concerns.
Zscaler ended at $320.96, down 2.4%, pressured by macroeconomic uncertainty and cautious sentiment toward high-growth cloud-security stocks.
Palo Alto Networks finished at $217.16, down 1.9%, with margin and integration risks from recent acquisitions prompting mild profit-taking.
Okta settled at $87.65, down 1.9%, as competitive challenges in identity management offset optimism around its AI-driven strategy.
Fortinet closed at $84.22, down 1.9%, slipping on investor concerns about firewall upgrade fatigue despite sustained global cyber-risk demand.
💡 Cyber Tip
Cross-reference critical AI-generated facts using multiple trusted sources.
Always cross-reference critical facts from AI-generated summaries or overviews using multiple trusted sources, especially for sensitive topics. 1 sentence explanation: The new “AI-targeted cloaking” attack tricks AI web browsers into citing fabricated information as verified facts, making their summaries unreliable.
🔐 What You Should Do
Manually search for the original source website cited by the AI.
Confirm the information by comparing it with other authoritative outlets.
⚠️ Why This Matters
It’s a powerful misinformation weapon that rapidly undermines public trust in AI tools. The cloaked content becomes “ground truth,” introducing widespread biases into AI overviews and decision systems.
📚 Cyber Book
How To Reduce Your Digital Footprint by Maya Lane
That concludes today’s briefing . You can check the top headlines here!
Copyright © 2025 CyberMaterial. All Rights Reserved.
Follow CyberMaterial on:
Substack, LinkedIn, Twitter, Reddit, Instagram, Facebook, YouTube, and Medium.










Wow, the part about AI-targeted cloaking really stood out to me. You hit the nail on the head calling it a 'powerful misinformation weapon to undermine trust and introduce bias'. As someone who teaches computer science and is passionate about AI, this context poisoning is exactly the kind of threat we need to watch for to ensure AI reliability.
Great daily roundup! The CrowdStrike stock movement is interesting in context. Down just 0.2% while the broader cybersecurity sector pulled back harder shows they're holding up well compared to peers. The "valuation concerns" mentioned are worth noting, but CRWD has consistently proven they can grow into their multiple through expaned enterprise penetration and platform consolidation.
What really stands out is their resilience after the summer outage incident. A lot of companies would have seen sustained sell offs, but CrowdStrike bounced back because their technology moat and customer retention metrics remained strong. The slight pullback here looks more like profit taking than any fundemental shift in investor sentiment.
Looking at the competitive landscape you mention (Zscaler down 2.4%, Palo Alto down 1.9%), CrowdStrike's relative outperformance suggests the market still sees them as a leader in endpoint security and XDR. The ongoing shift to AI powered security agents should be a tailwind for them going forward.