Cyber Briefing: 2025.10.28
LastPass phishing, ChatGPT Atlas flaw, Chrome zero-day, Google insider leak, Vibra breach, Swedish grid hack, F5 hit, Gmail safe, 183M logins sold.
👉 What’s going on in the cyber world today?
Welcome to Cyber Briefing, the newsletter that informs you about the latest cybersecurity advisories, alerts, incidents and news every weekday.
First time seeing this? Please Subscribe
🚨 Cyber Alerts
1. Fake LastPass Death Claims Breach Vaults
LastPass is currently warning users about a sophisticated phishing campaign, attributed to the financially motivated group CryptoChameleon (UNC5356), that sends emails claiming a family member requested emergency access to their password vault as part of a legacy inheritance process. This enhanced campaign, which redirects users to a fraudulent login page to steal their master password and has even involved direct calls to victims, now also includes efforts to steal user passkeys using dedicated phishing domains.
2. ChatGPT Atlas Browser Fooled By Fake Url
The newly launched OpenAI ChatGPT Atlas web browser is vulnerable to a prompt injection attack that exploits its combined address/search bar, or omnibox, by disguising malicious commands as seemingly harmless URLs. This technique allows attackers to bypass security checks and trick the built-in AI agent into executing harmful instructions, such as redirecting users to phishing sites or performing unauthorized actions.
3. Chrome Zero Day Delivers LeetAgent
A zero-day flaw in Google Chrome, CVE-2025-2783, was actively exploited in a campaign known as Operation ForumTroll to distribute espionage tools, including the newly discovered LeetAgent spyware, developed by the Italian vendor Memento Labs. The highly targeted operation leveraged phishing emails with malicious links to compromise organizations, particularly in Russia, with evidence linking it to a broader threat actor also utilizing the more sophisticated Dante spyware.
For more alerts, click here!
💥 Cyber Incidents
4. Google Contractor Steals Play Files
Google’s security was significantly compromised when a contractor with privileged access orchestrated a prolonged data breach, capturing nearly 2,000 screenshots and exfiltrating critical files detailing the Play Store’s infrastructure and security protocols. This incident underscores the major risk posed by insider threats and third-party access, prompting an internal audit and a swift response to contain the damage and prevent potential widespread vulnerabilities in its core app distribution ecosystem.
5. Vibra Hospital Data Breach Probe
Two law firms, Shamis & Gentile, P.A., and Strauss Borrelli PLLC, have initiated investigations into a data breach at Vibra Hospital of Sacramento that exposed patients’ personally identifiable information (PII) and protected health information (PHI). This compromised data could be used in fraud or identity theft schemes, and those affected may be entitled to compensation for out-of-pocket expenses, time, or emotional distress.
6. Hackers Target Swedish Power Grid
Swedish state-owned power grid operator Svenska kraftnät confirmed a recent cyberattack that resulted in a data breach involving an isolated, external file transfer solution, emphasizing that the country’s critical electricity supply was not impacted. The Everest ransomware group has claimed responsibility for the incident, threatening to leak an alleged $\approx 280$ gigabytes of stolen data if the company does not comply with its demands.
For more incidents click here!
📢 Cyber News
7. F5 Faces Revenue Hit From Cyber Attack
A recent cyber attack that compromised F5’s software is expected to significantly slow the company’s revenue growth, with the CEO citing the potential for customers to delay or cancel deals. The software and cybersecurity company projects its fiscal year 2026 revenue growth will be only flat to 4%, which is notably lower than the 9% growth analysts had anticipated.
8. Google Denies Massive Gmail Breach
Google was recently forced to publicly deny sensational news reports claiming a massive data breach had exposed 183 million Gmail accounts. The company clarified that the compromised credentials were not from a new Gmail breach but rather a compilation of stolen data gathered over time through information-stealing malware and other attacks, which were later added to the Have I Been Pwned (HIBP) platform.
9. Cybercriminals Trade 183M Stolen Logins
Cybersecurity firm Synthient compiled a massive database of 183 million leaked credentials, primarily sourced from information stealer malware shared across platforms like Telegram, and submitted the data to Have I Been Pwned (HIBP). While the discovery was mischaracterized as a “Gmail breach,” the data verified by Troy Hunt added 16.4 million new email addresses to the HIBP service, prompting experts and Google to urge users to enable multi-factor authentication (MFA) for security.
For more news click here
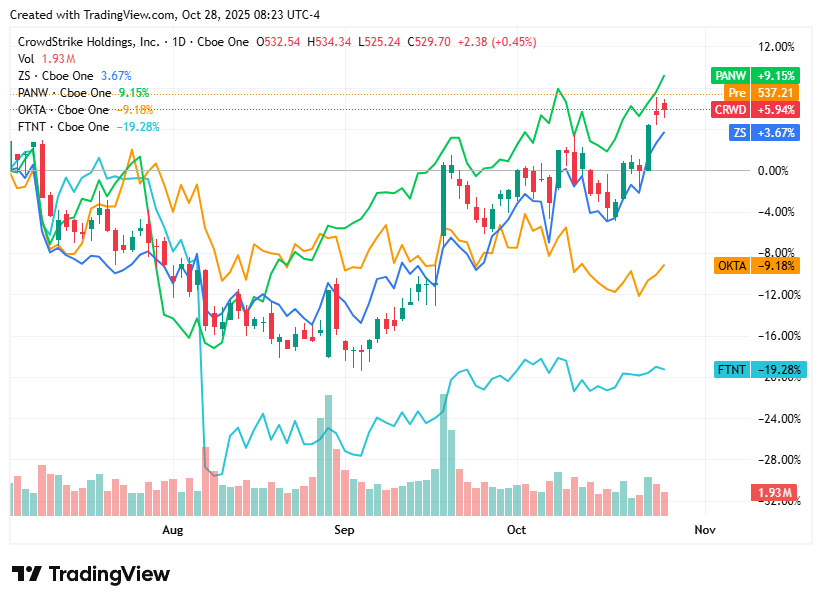
📈Cyber Stocks
On Tuesday, 28th October, cybersecurity stocks extended their winning streak, supported by strong enterprise demand for AI-driven and zero-trust solutions. The sector benefited from broader market stability and investor optimism ahead of key quarterly earnings reports, while geopolitical tensions and regulatory focus on cyber resilience continued to highlight cybersecurity as a defensive growth play. Overall, the gains reflected sustained confidence in the industry’s long-term fundamentals despite lingering valuation concerns.
CrowdStrike closed near $529, up 0.4%, as investor enthusiasm for its AI-powered Falcon platform and expanding enterprise adoption boosted sentiment.
Zscaler ended around $326, up 1.0%, driven by accelerating cloud migration trends and positive analyst outlooks for its zero-trust model.
Palo Alto Networks finished near $220, up 1.5%, supported by institutional buying and confidence in its platform consolidation and M&A-driven growth strategy.
Okta settled around $89.60, up 0.6%, aided by renewed interest in identity security demand and new enterprise contract wins.
Fortinet closed near $85.80, up 0.3%, with steady geopolitical cyber risks reinforcing demand for its network security infrastructure.
💡 Cyber Tip
Fake LastPass Death Claims Breach Vaults
LastPass is warning users about a sophisticated phishing campaign by the group CryptoChameleon (UNC5356), which sends fake “legacy inheritance” emails claiming a family member uploaded a death certificate to request emergency access to a user’s password vault. The scam redirects victims to a fake login site, lastpassrecovery[.]com, to steal master passwords and now also targets passkeys through domains such as mypasskey[.]info and passkeysetup[.]com. Some victims have even received phone calls from attackers posing as LastPass support.
🔐 What You Should Do
Do not click on links in any LastPass-related emails claiming emergency or inheritance access.
Verify all alerts by logging in directly through the official LastPass website or app.
Never share or enter your master password on third-party pages.
Report phishing attempts to security@lastpass.com and delete suspicious messages.
Enable multi-factor authentication (MFA) and review account activity for unauthorized logins.
Be cautious of phone calls claiming to be from LastPass support staff.
⚠️ Why This Matters
This campaign exploits trust in legitimate LastPass features and manipulates users with emotional triggers around death and inheritance. By stealing both passwords and passkeys, attackers can access vaults and linked accounts. Staying alert, verifying all communications through official channels, and using strong MFA are essential to protect against this evolving social engineering threat.
📚 Cyber Book
Identity Theft Privacy by Robert Siciliano
That concludes today’s briefing . You can check the top headlines here!
Copyright © 2025 CyberMaterial. All Rights Reserved.
Follow CyberMaterial on:
Substack, LinkedIn, Twitter, Reddit, Instagram, Facebook, YouTube, and Medium.