Cyber Briefing: 2025.10.23
Jingle Thief cloud fraud, fake Zoom Ukraine hack, MuddyWater spying, Jewett ransomware, Salt Typhoon telecom hack, JFL losses, NY DFS rules, Keycard $38M, JLR $2.5B hit.
👉 What’s going on in the cyber world today?
Welcome to Cyber Briefing, the newsletter that informs you about the latest cybersecurity advisories, alerts, incidents and news every weekday.
First time seeing this? Please Subscribe
🚨 Cyber Alerts
1. Gift Card Heist Via Cloud Hackers
A persistent cybercriminal group known as Jingle Thief is actively targeting cloud environments, primarily in the retail and consumer services sectors, to execute sophisticated gift card fraud by stealing credentials through phishing and smishing. This group, which has been active since at least 2021 and is believed to originate from Morocco, maintains long-term access within victim organizations to perform extensive reconnaissance, issue unauthorized high-value gift cards, and then resell them for monetary gain.
2. Fake Zoom Calls Target Ukraine Aid
A sophisticated spear-phishing campaign dubbed PhantomCaptcha targeted humanitarian and Ukrainian government organizations on October 8, 2025, attempting to deliver a potent Remote Access Trojan (RAT) that uses a WebSocket for command-and-control (C2). The attack, which involved emails impersonating the Ukrainian President’s Office, used a malicious PDF to lure victims into a complex chain that included a fake Zoom site and a deceptive Cloudflare CAPTCHA page to execute a PowerShell dropper, signaling extensive operational planning by a highly capable, though unattributed, adversary.
3. MuddyWater Launches Global Spying
The Iranian nation-state group MuddyWater is exploiting a compromised email account to deploy the Phoenix backdoor against over 100 government and diplomatic organizations, as well as international and telecommunications firms, across the Middle East and North Africa (MENA) for intelligence gathering. This sophisticated campaign leverages weaponized Microsoft Word documents to trick users into enabling malicious macros, ultimately deploying the new backdoor variant alongside custom credential-stealers and legitimate remote management tools for enhanced stealth.
For more alerts, click here!
💥 Cyber Incidents
4. Ransomware Hits Jewett Cameron
Fencing and pet solutions provider Jewett-Cameron Company recently suffered a cyberattack that involved the deployment of encryption and monitoring software, leading to system disruptions and the theft of sensitive financial and IT-related information. While the company is working to restore its systems and believes it has contained the intrusion, the hackers have threatened to leak the stolen data unless a ransom is paid.
5. Salt Typhoon Hacks European Telecom
A European telecom company was compromised in July 2025 by the China-linked espionage group Salt Typhoon, which gained initial access by exploiting a vulnerability in a Citrix NetScaler Gateway. The group, known for its extensive global targeting of telecommunications, then deployed a custom backdoor called SNAPPYBEE (Deed RAT) using DLL sideloading with legitimate antivirus programs to evade detection.
6. JFL Loses 800K Weekly After Hack
The April cyberattack on the Juan F. Luis Hospital cost the facility an estimated $750,000 to $800,000 per week due to delayed electronic billing and forced a complete, five-month shift to manual operations, though no patient or staff data was compromised. CEO Darlene A. Baptiste detailed the massive recovery effort, which included a full rebuild and modernization of the hospital’s technology infrastructure with a focus on cloud security, redundancy, and real-time threat monitoring to prevent future breaches.
For more incidents click here!
📢 Cyber News
7. NY DFS Updates Third Party Cyber Rules
The New York State Department of Financial Services ($\text{DFS}$) Acting Superintendent, Kaitlin Asrow, has issued new cybersecurity guidance during Cybersecurity Awareness Month to address the growing risks that $\text{DFS}$-regulated entities face when using third-party service providers ($\text{TPSPs}$). This guidance clarifies existing compliance obligations and shares best practices, reminding entities that they are ultimately accountable for protecting consumers and managing risk, even when leveraging $\text{TPSPs}$.
8. Keycard Raises 38 Million Funding
AI identity infrastructure company Keycard has exited stealth with $38 million in total funding across a seed and Series A round, backed by investors like Andreessen Horowitz, Boldstart Ventures, and Acrew Capital. The San Francisco-based firm, founded by former Snyk and Okta leaders, is building a platform for Identity and Access Management (IAM) for AI agents, using cryptography and dynamic tokens to ensure trusted and controlled deployment of AI into production environments.
9. Jaguar Land Rover Cyberattack Hits UK
The cyberattack on Jaguar Land Rover (JLR) in early September is now estimated by the Cyber Monitoring Centre (CMC) to have cost the UK economy $2.5 billion (£1.9 billion), making it the most economically damaging cyber incident ever to impact the country. JLR’s immediate shutdown of systems to mitigate the attack led to a severe disruption of production at the Solihull plant and retail operations, including delays in car registrations and parts supply for UK dealers.
For more news click here
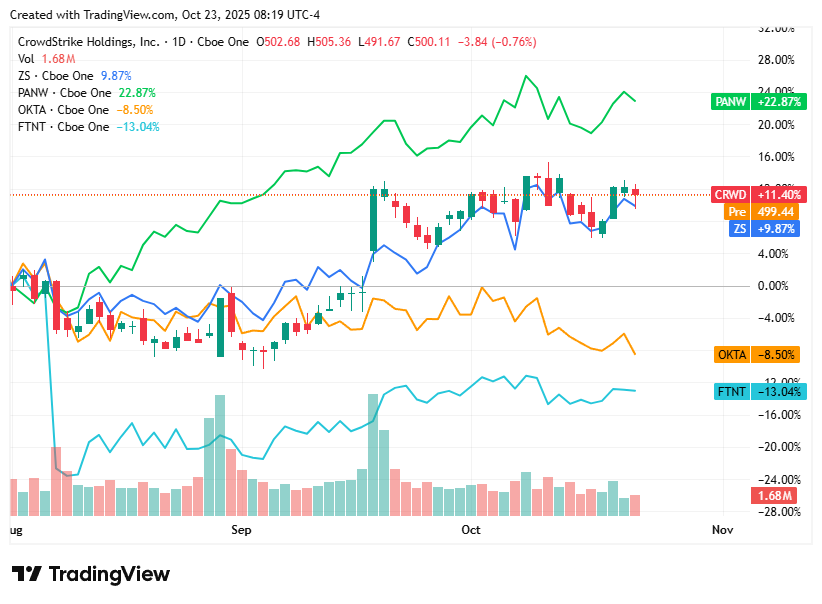
📈Cyber Stocks
On Thursday, 23rd October, cybersecurity stocks finished broadly lower, mirroring weakness across the wider technology sector. Investor sentiment turned cautious amid renewed concerns over slowing enterprise IT spending, margin pressures from recent acquisitions, and competitive dynamics in the identity and cloud security segments. Despite the pullback, analysts noted that long-term demand for AI-enhanced and zero-trust security platforms remains solid, leaving the sector’s fundamentals intact.
CrowdStrike closed at $500.11, down 0.8%, as broader tech softness and growth moderation concerns offset optimism around its AI-driven endpoint defense capabilities.
Zscaler ended at $307.92, down 0.8%, pressured by investor rotation away from high-growth cloud names amid macroeconomic uncertainty.
Palo Alto Networks finished at $212.42, down 0.9%, with concerns over acquisition integration and short-term margin compression weighing on sentiment.
Okta settled at $87.04, down 2.7%, as competitive pressures in identity management and execution risks surrounding its AI roadmap led to sharper declines.
Fortinet closed at $84.66, down 0.1%, holding relatively steady as steady geopolitical cyber threats cushioned the impact of a sector-wide pullback.
💡 Cyber Tip
Gift Card Heist Via Cloud Hackers
A persistent group known as Jingle Thief is targeting cloud environments in retail and consumer services to carry out large scale gift card fraud. The attackers steal credentials via phishing and smishing, maintain long term access to Microsoft 365 and cloud systems, locate gift card issuance workflows, issue high value cards, and resell them for profit. Researchers say the group focuses on identity theft and cloud reconnaissance rather than custom malware, making detection harder.
🔐 What You Should Do
Enforce strong multi factor authentication and require phishing-resistant methods for admin and issuance accounts.
Apply conditional access and least privilege so gift-card issuance systems are not accessible from standard user accounts.
Limit who can issue or approve gift cards and require multi person controls for high value redemptions.
Monitor and block unusual inbox rules, automatic forwards, and silent mailbox changes.
Audit SharePoint, OneDrive, and cloud storage for gift card templates, issuance spreadsheets, and privileged credentials.
Enable logging and extended retention for authentication events, mailbox activity, and issuance workflows.
Use anomaly detection for unusual issuance patterns and rapid increases in gift card creation.
Run targeted phishing simulations and train staff to spot smishing and credential harvesting lures.
Rotate credentials and review registered authenticator devices after any suspicious access.
⚠️ Why This Matters
Jingle Thief converts stolen identity into direct financial gain by abusing cloud workflows. Because the attacks rely on stolen credentials and long term stealth, they can bypass endpoint controls and cause large, hard to trace losses. Strong identity controls, strict issuance procedures, and vigilant monitoring are the best defenses.
📚 Cyber Book
The AI Scam Survival Guide by Alex East
That concludes today’s briefing . You can check the top headlines here!
Copyright © 2025 CyberMaterial. All Rights Reserved.
Follow CyberMaterial on:
Substack, LinkedIn, Twitter, Reddit, Instagram, Facebook, YouTube, and Medium.