Cyber Briefing: 2025.10.22
PolarEdge botnet grows, new Russian malware, Copilot leak, UK union hack, inmate breach, NSA data stolen, Pwn2Own $520K, Monolock sold, Meta anti-scam tools.
👉 What’s trending in cybersecurity today?
Welcome to Cyber Briefing, the newsletter that informs you about the latest cybersecurity advisories, alerts, incidents and news every weekday.
First time seeing this? Please Subscribe
🚨 Cyber Alerts
1. PolarEdge Expands Router Botnet
Cybersecurity researchers have dissected PolarEdge, a sophisticated botnet malware first documented in February 2025 that targets routers from Cisco, ASUS, QNAP, and Synology. This TLS-based ELF implant functions primarily as an Operational Relay Box (ORB) network, designed to send a host fingerprint to a command-and-control (C2) server and execute commands over a built-in TLS server, with evidence suggesting its activity may have begun as early as June 2023.
2. Google Finds New Russian Malware
The Russia-linked hacking group COLDRIVER has significantly increased its operations tempo, rapidly developing a new family of malware—NOROBOT, YESROBOT, and MAYBEROBOT—since May 2025, just after its previous LOSTKEYS malware was publicly disclosed. This new activity, which uses fake CAPTCHA verification lures to run malicious commands, suggests a swift, sustained effort by the threat actor to update its arsenal and evade detection for continued intelligence gathering against high-value targets.
3. Copilot Flaw Exposes Sensitive Data
An attack exposed a Microsoft 365 Copilot vulnerability that allowed indirect prompt injection to exfiltrate sensitive tenant data. By embedding hidden instructions in a document, attackers tricked the AI into fetching corporate emails, encoding them, and then hiding the stolen data within a malicious, clickable Mermaid diagram that forwarded the information to the attacker’s server.
For more alerts, click here!
💥 Cyber Incidents
4. Union Cyberattack Raises Concerns
A cyber-attack in June on the union Prospect—parent to the film and TV group Bectu—resulted in a data breach for the majority of its 150,000 members, compromising sensitive information like bank details and birth dates. The breach has raised serious concerns about the potential compromise of data relating to the UK’s national security, given Prospect’s extensive representation within the Ministry of Defence, military suppliers, and various government departments.
5. Romanian Prisoner Hacks Prison IT
A Romanian prisoner at a hospital complex in Dej successfully hacked the country’s national prison management platform between August and October, exploiting vulnerabilities in the tablets and kiosks provided to inmates. This breach allowed the prisoner to access an online system used to file requests, redeem time off sentences, and manage funds for purchases.
6. Hackers Claim Data On NSA Officials
A hacking group known as Scattered LAPSUS$ Hunters has significantly expanded its cache of stolen personal data, now possessing dossiers on over 22,000 U.S. government officials from numerous agencies, including the NSA, DIA, and CDC. The group claims to have compiled this extensive data by leveraging caches of stolen Salesforce customer data, following their earlier public doxing of hundreds of DHS and ICE officials.
For more incidents, click here!
📢 Cyber News
7. Hackers Make 520K At Pwn2Own
Participants at the Pwn2Own Ireland 2025 hacking competition, hosted by Trend Micro’s Zero Day Initiative (ZDI), earned a massive $522,500 on the first day by successfully demonstrating 34 previously unknown vulnerabilities. These zero-day exploits targeted a wide range of devices, including routers, printers, NAS devices, and smart home products, with the largest single prize of $100,000 going to a ‘SOHO Smashup’ exploit chain.
8. Monolock Ransomware Sold Online
The highly capable Monolock Ransomware V1.0 is now being aggressively sold on dark web forums, drawing serious concern from the cybersecurity community. This newly available malicious software, which incorporates AES-256 encryption, support for Windows and Linux, and a custom-built administrative panel, is being offered across several price tiers. Security experts warn that its advanced features, including the ability to spread via torrents and target modern cloud storage, represent a significant, evolving threat to organizations of all sizes.
9. Meta Launches New Anti Scam Tools
Meta is rolling out new security features for Messenger and WhatsApp to better protect users from scams. WhatsApp will now display a warning before a user shares their screen with an unknown contact during a video call, preventing the unintentional sharing of sensitive data. On Messenger, users can enable a new “Scam detection” setting that alerts them to suspicious messages from unknown connections, leveraging on-device AI to maintain end-to-end encryption unless the user opts to share the message for further review.
For more news click here
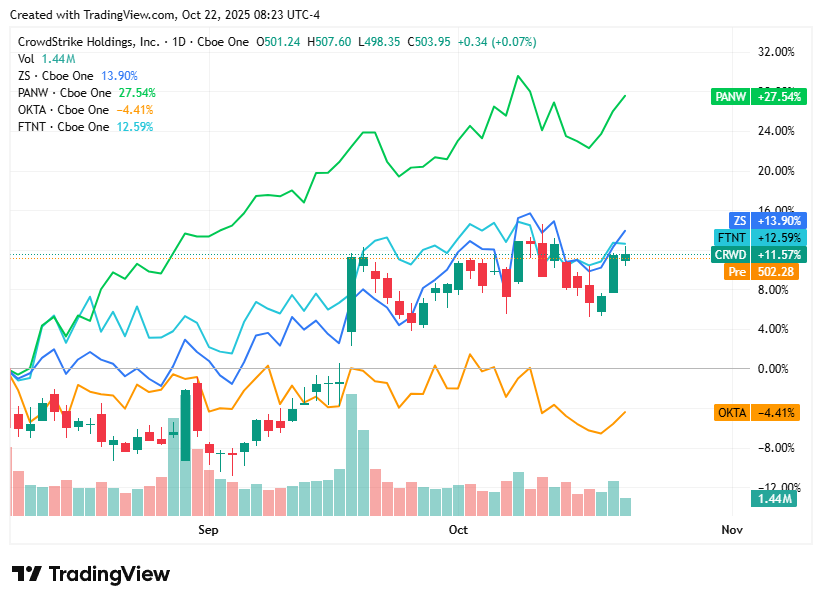
📈Cyber Stocks
On Wednesday, 22nd October, cybersecurity stocks closed mostly higher, buoyed by strong investor confidence in the sector’s AI-driven innovation and continued enterprise investment in zero-trust and identity security. Broader market stability and optimism around Q4 earnings season also lifted sentiment, though minor pullbacks in a few names reflected profit-taking and concerns over product-cycle maturity. Overall, the sector outperformed the broader tech index, signaling sustained resilience amid rising global cyber risks.
CrowdStrike closed at $503.95, up 0.07%, as confidence in its AI-powered Falcon platform and growing threat-intelligence dominance kept investor sentiment steady.
Zscaler ended at $310.37, up 1.5%, benefiting from continued enterprise migration to cloud-native zero-trust environments.
Palo Alto Networks finished at $214.40, up 1.3%, lifted by positive expectations around its platform consolidation strategy and identity-security acquisitions.
Okta settled at $89.45, up 1.2%, supported by renewed investor enthusiasm for its expanding role in AI-driven identity protection.
Fortinet closed at $84.78, down 0.1%, edging lower as some investors remained cautious about firewall refresh cycles despite strong geopolitical demand for network defense.
💡 Cyber Tip
Microsoft 365 Copilot Flaw Exposes Sensitive Data
Researchers discovered a vulnerability in Microsoft 365 Copilot that allowed attackers to steal corporate information through an indirect prompt injection. The exploit worked by embedding hidden instructions in a document that tricked Copilot into retrieving sensitive data such as corporate emails, encoding them, and embedding the stolen data inside a malicious Mermaid diagram. When a user clicked the diagram’s fake “Login” button, the encoded data was sent to the attacker’s server.
🔐 What You Should Do
Avoid summarizing or opening untrusted Office documents with Copilot until your environment is fully updated.
Ensure your Microsoft 365 Copilot and Office applications have the latest security patches.
Train employees to recognize AI-driven social engineering tactics, including suspicious prompts or diagrams.
Restrict access to sensitive data sources that Copilot or similar tools can query.
Implement data loss prevention (DLP) policies to detect and block unauthorized data transfers.
⚠️ Why This Matters
This flaw shows how AI assistants can be manipulated to perform actions outside their intended scope. By abusing trusted features like Mermaid diagrams, attackers can hide exfiltration channels inside normal business workflows. Keeping Copilot and Office apps updated and maintaining strict data governance are essential to prevent similar AI-based attacks.
📚 Cyber Book
If It’s Smart, It’s Vulnerable by Mikko Hypponen
That concludes today’s briefing . You can check the top headlines here!
Copyright © 2025 CyberMaterial. All Rights Reserved.
Follow CyberMaterial on:
Substack, LinkedIn, Twitter, Reddit, Instagram, Facebook, YouTube, and Medium.










Fascinating, this brief truly highlights the escalating sophistication of threats, paticularly how AI vulnerabilties are becoming a serious frontier, making me reflect on the broader implications of all these warnings, including your previous insights on state-sponsored attacks.