Cyber Briefing: 2025.10.17
Microsoft stops ransomware, NK blockchain malware, EtherHiding attacks, Hamas airport hack, Prosper & Sotheby’s breaches, Qilin rise, Matters.AI $6M, healthcare leaks.
👉 What are the latest cybersecurity alerts, incidents, and news?
Welcome to Cyber Briefing, the newsletter that informs you about the latest cybersecurity advisories, alerts, incidents and news every weekday.
First time seeing this? Please Subscribe
🚨 Cyber Alerts
1. Microsoft Pulls 200 Suspicious Certificates
Microsoft successfully disrupted a Vanilla Tempest ransomware campaign that aimed to deploy the Rhysida file encryptor, primarily by revoking over 200 fraudulent certificates the cybercriminals used to sign their malware.
2. NK Hackers Hide Malware In Blockchain
This North Korean state-sponsored hacking group is now using a novel technique called EtherHiding to distribute malware and steal cryptocurrency, a first for a nation-state actor. This method involves hiding malicious code within a smart contract on a public blockchain like Ethereum, making it resistant to takedowns and difficult to trace.
3. Hackers Spread Malware With Blockchain
The financially motivated threat group UNC5142 is distributing various information stealers, including Atomic, Lumma, Rhadamanthys, and Vidar, by exploiting compromised WordPress sites and an evasion technique called EtherHiding, which stores malicious code on public blockchains like the BNB Smart Chain to resist detection. This sophisticated operation employs a multi-stage JavaScript downloader, CLEARSHORT, to deliver malware to both Windows and macOS users via social engineering and has evolved its blockchain infrastructure for increased agility and resilience against takedowns.
For more alerts, click here!
💥 Cyber Incidents
4. Pro Hamas Hackers Target Airport Speakers
Unauthorized messages supporting Hamas and including slurs against U.S. and Israeli leaders blasted from loudspeakers at airports in Pennsylvania and British Columbia on Tuesday, startling passengers. This digital security breach also involved pro-Hamas messages flashing on flight information displays, though authorities confirmed the cyber-vandalism caused no flight safety issues.
5. Prosper Breach Hits 17 Million Accounts
Hackers breached the systems of the financial services company Prosper, stealing the personal information, including Social Security Numbers, of over 17.6 million customers and loan applicants. The peer-to-peer lender, which detected the intrusion on September 2nd, is actively investigating the full extent of the data theft and plans to offer free credit monitoring to affected individuals.
6. Sothebys Data Breach Exposes Customers
Major international auction house Sotheby’s has announced a data breach where unauthorized actors stole sensitive customer information, including Social Security numbers and financial account details. The breach was discovered on July 24, 2025, and a two-month investigation confirmed the scope of the stolen data and the affected individuals.
For more incidents, click here!
📢 Cyber News
7. Qilin Ransomware Claims New Victims
Resecurity’s new report reveals the Qilin ransomware-as-a-service (RaaS) group is heavily dependent on a global network of rogue bullet-proof-hosting (BPH) providers to support its extensive extortion operations. This reliance allows Qilin to discreetly host illicit infrastructure and stolen victim data, effectively operating beyond the immediate reach of law enforcement and cybersecurity researchers.
8. Matters AI Raises 6 Million For Security
Matters.AI, a San Francisco-based enterprise data security startup founded in 2023, has secured $6.25 million in seed and pre-seed funding to fuel its growth. The company has developed an autonomous platform, dubbed an ‘AI Security Engineer,’ which uses semantic intelligence and behavioral context to unify data security functions, proactively safeguarding data across all enterprise environments by learning how and why it is used.
9. Five Healthcare Providers Warn Patients
A flurry of cyberattacks and data breaches has been announced by five healthcare providers across the United States. Each organization has engaged third-party cybersecurity experts to investigate the attacks, which led to the potential compromise of a wide range of sensitive patient data, including Social Security numbers, medical records, and financial information.
For more news click here
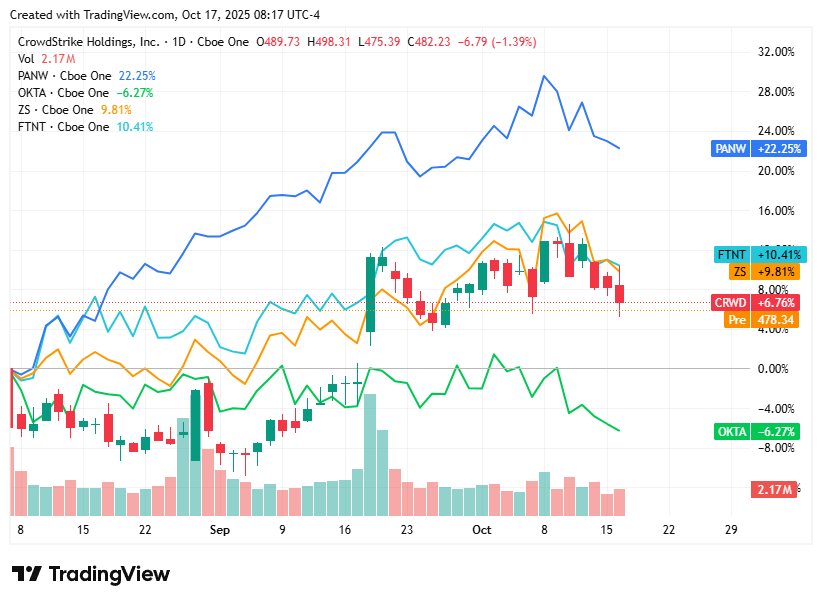
📈Cyber Stocks
As the week ended on Friday, 17th October, cybersecurity stocks closed mixed, reflecting a cautious tone across the broader technology sector. Investor sentiment was shaped by profit-taking after a strong early-month rally, renewed concerns over high valuations, and persistent macroeconomic uncertainty. Despite the subdued finish, long-term optimism around AI-enhanced security, zero-trust adoption, and heightened geopolitical risks continued to anchor confidence in the sector’s growth outlook.
CrowdStrike closed around $487, edging lower as investors took profits after recent gains and weighed stretched valuations against sustained AI-driven growth momentum.
Zscaler ended near $301, slipping slightly amid sector rotation away from high-growth cloud names despite firm enterprise demand for zero-trust solutions.
Palo Alto Networks finished at roughly $205, easing modestly as investors monitored integration progress and margin pressures from recent acquisitions.
Okta settled close to $88, facing mild weakness on continued competitive pressures in identity management and execution risks tied to its AI expansion plans.
Fortinet closed near $83, holding steady as ongoing geopolitical tensions and elevated cyberattack activity reinforced demand for its network security offerings.
💡 Cyber Tip
Microsoft Pulls 200 Certificates to Disrupt Ransomware Campaign
Microsoft has disrupted a campaign by a threat group tracked as Vanilla Tempest that aimed to deploy the Rhysida ransomware. The company revoked more than 200 fraudulent code signing certificates the attackers used to sign fake Microsoft Teams installers. The signed installers delivered a backdoor called Oyster, which was then used to deploy the Rhysida encryptor. The fraudulent files were hosted on deceptive domains and likely reached victims via manipulated search results.
🔐 What You Should Do
Block and investigate any unexpected Microsoft Teams installers before running them.
Verify downloaded installers by checking publisher signatures and obtaining software from official vendor sites.
Use application allowlisting so only approved installers can run on endpoints.
Ensure endpoint detection and response solutions are updated and scanning for signed malicious binaries.
Monitor network traffic and logs for suspicious connections to new domains or unusual post-install activity.
Revoke or rotate any internal certificates if you detect related compromise.
⚠️ Why This Matters
By abusing legitimate code signing, attackers can make malware appear trustworthy and bypass many security controls. Revoking the fraudulent certificates reduces the immediate risk, but persistent threat actors may obtain new certificates. Strong verification of installers, allowlisting, and vigilant detection are essential to stop similar supply chain style attacks.
📚 Cyber Book
Cyber Smart: Five Habits to Protect Your Family, Money, and Identity from Cyber Criminals by Bart R. McDonough
That concludes today’s briefing . You can check the top headlines here!
Copyright © 2025 CyberMaterial. All Rights Reserved.
Follow CyberMaterial on:
Substack, LinkedIn, Twitter, Reddit, Instagram, Facebook, YouTube, and Medium.