Cyber Briefing: 2025.10.08
Chrome RCE flaw exposed, Redis bug allows RCE, Storm-1175 links to Medusa, DraftKings breach, Salesforce rejects ransom, Doctors Imaging leak, Kido arrests, Filigran $58M raise, Y2K38 risk.
👉 What are the latest cybersecurity alerts, incidents, and news?
Welcome to Cyber Briefing, the newsletter that informs you about the latest cybersecurity advisories, alerts, incidents and news every weekday.
First time seeing this? Please Subscribe
🚨 Cyber Alerts
1. Google Chrome RCE Flaw Details Leak
A severe vulnerability in Google Chrome’s V8 JavaScript engine, tracked as a WebAssembly (Wasm) type canonicalization bug, was exploited by researchers to achieve remote code execution (RCE). The exploit works by abusing a flaw in how Chrome handles nullability checks, allowing attackers to bypass sandboxing and run malicious code on a user’s machine.
2. Redis Use After Free Bug Enables RCE
A severe vulnerability, CVE-2025-49844, has been found in Redis, allowing an authenticated attacker to execute malicious code remotely. This flaw affects all versions of Redis that use the Lua scripting engine, posing a significant risk to data and network integrity.
3. Microsoft Ties Storm 1175 To Medusa
Microsoft recently linked the threat group Storm-1175 to the exploitation of a critical vulnerability in Fortra GoAnywhere software. The attackers used a critical deserialization bug, CVE-2025-10035, to install Medusa ransomware and gain remote access to systems.
For more alerts, click here!
💥 Cyber Incidents
4. DraftKings Warns Of Account Breaches
DraftKings, the sports betting company, recently informed a small number of customers that their accounts were compromised in a credential stuffing attack. The company stated that the attackers used login information stolen from other sources to access customer data, though no sensitive financial or personal information was exposed.
5. Salesforce Refuses To Pay Ransom
Salesforce won’t pay a ransom to the hackers who stole data from its customers this year, despite threats to leak the information. The company has informed affected clients and confirmed its decision to BleepingComputer, following the hackers’ attempt to extort 39 companies with stolen data.
6. Doctors Imaging Data Breach Hits 171K
In late August 2025, Doctors Imaging Group, a Florida-based radiology practice, discovered a data breach that exposed the personal and medical information of over 171,000 individuals. This breach occurred between November 5 and 11, 2024, when hackers accessed and copied files from the company’s network.
For more incidents, click here!
📢 Cyber News
7. Two Arrested Over Nursery Cyber Attack
Following a cyberattack on the Kido nursery chain, two individuals have been arrested on suspicion of computer misuse and blackmail. The attackers reportedly stole personal information, including photos and names, of approximately 8,000 children to demand ransom money.
8. Filigran Raises 58 Million Series C
French cybersecurity startup Filigran has secured $58 million in a Series C funding round led by Eurazeo, bringing its total funding to over $100 million. The company plans to use the investment to expand into new markets, hire more talent, and further develop its cyber threat prevention platform and open-source projects.
9. Y2K38 Bug Is A Security Vulnerability
Despite their projected 2036 and 2038 trigger dates, time-related software bugs, similar to the Y2K bug, can be exploited by hackers today to cause system failures in critical infrastructure and consumer devices. The challenge is that these bugs are widespread and require significant architectural changes to fix, making them a much more difficult problem to solve than Y2K.
For more news click here
📈Cyber Stocks
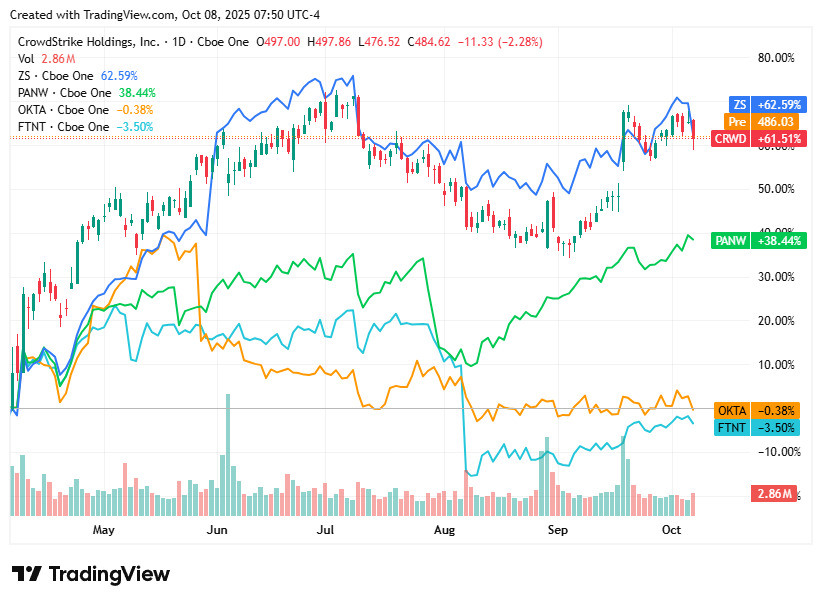
On Wednesday, 8th October, cybersecurity stocks broadly declined as part of a wider technology sell-off driven by investor caution over high valuations and mixed global economic signals. Despite continued demand for AI-driven defense platforms and zero-trust solutions, profit-taking and market rotation away from high-growth tech weighed on the sector. Geopolitical tensions and steady enterprise security spending provided some stability but weren’t enough to offset the downward momentum.
CrowdStrike closed at $484.62, down 2.3%, as investors reduced exposure following recent highs despite strong confidence in its AI-enhanced Falcon ecosystem.
Zscaler ended at $292.75, down 4.1%, reflecting risk-off sentiment in growth tech and worries about macroeconomic headwinds affecting cloud spending.
Palo Alto Networks finished at $211.04, down 0.7%, with mild profit-taking ahead of CyberArk integration updates and a softer short-term margin outlook.
Okta settled at $90.89, down 3.1%, as competitive pressure in identity management and valuation concerns outweighed optimism over AI-driven security initiatives.
Fortinet closed at $84.92, down 1.7%, dragged by concerns over slowing firewall upgrades and cautious corporate IT budgets, despite steady geopolitical demand for network protection.
💡 Cyber Tip
💥 Update Chrome Now to Block Public RCE Exploit
A critical remote code execution exploit targeting Chrome’s V8 JavaScript engine was published with full technical details and working proof of concept. The flaw allows an attacker to bypass sandboxing and run code via a malicious web page, so updating Chrome immediately is essential.
✅ What you should do
Update Google Chrome to the latest patched build right away and restart your browser.
Ensure automatic updates are enabled for Chrome and other Chromium based browsers.
Avoid visiting untrusted or suspicious websites and do not open unknown links in email or chat.
Keep your operating system and antivirus up to date to benefit from platform mitigations.
For high risk users, enable Chrome Site Isolation and other browser hardening features.
🔒 Why this matters
The exploit gives attackers a way to escape the browser sandbox and execute code on a user’s machine simply by visiting a crafted web page. Public release of the exploit code increases the risk of widespread attacks, so prompt patching and cautious browsing are the best defenses.
📚 Cyber Book
Phishing Pitfalls by Vlad Ivanusca
That concludes today’s briefing . You can check the top headlines here!
Copyright © 2025 CyberMaterial. All Rights Reserved.
Follow CyberMaterial on:
Substack, LinkedIn, Twitter, Reddit, Instagram, Facebook, YouTube, and Medium.