Cyber Briefing: 2025.10.06
CISA adds flaws, Zimbra zero-day, Oracle RCE, Discord breach, Salesforce leaks, DeFi hack, Qantas case, Flagstar $31.5M, ParkMobile $1 credit.
👉 What are the latest cybersecurity alerts, incidents, and news?
Welcome to Cyber Briefing, the newsletter that informs you about the latest cybersecurity advisories, alerts, incidents and news every weekday.
First time seeing this? Please Subscribe
🚨 Cyber Alerts
1.CISA Adds New Flaws to KEV Catalog
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added five new vulnerabilities to its Known Exploited Vulnerabilities (KEV) catalog, mandating that federal agencies patch them. The flaws affect products from Smartbedded Meteobridge, Samsung, Juniper ScreenOS, Jenkins, and GNU Bash, with an urgent deadline of October 23, 2025, for compliance. This directive aims to secure federal networks against active threats. Private organizations are also strongly urged to address these same vulnerabilities in their systems.
2. Hackers Exploit Zimbra Zero Day Flaw
Threat actors exploited a zero-day vulnerability in Zimbra’s email software, using specially crafted calendar attachments to steal data from a military organization. The attack was discovered by security researchers who were monitoring for unusually large calendar files, and they found that the attackers were able to run malicious code and steal credentials and emails.
3. Oracle Issues Security Alert
An Oracle E-Business Suite vulnerability, CVE-2025-61882, is remotely exploitable without authentication, meaning it doesn’t require a username or password. A successful attack could lead to remote code execution, so Oracle strongly recommends applying the security updates immediately.
For more alerts, click here!
💥 Cyber Incidents
4. Discord Reveals Data Breach Incident
Hackers breached a third-party customer service provider used by Discord, leading to the theft of partial payment information and personally identifiable data from a limited number of users who had interacted with the company’s support or safety teams. The compromised data included names, email addresses, and in some cases, government-issued IDs.
5. Extortion Group Launches Salesforce Data Leak
An extortion group has launched a new data leak site, publicly targeting dozens of companies affected by breaches involving Salesforce. The group, calling themselves Scattered Lapsus$ Hunters, is leaking samples of stolen data and demanding ransoms from companies to prevent further exposure.
6. Abracadabra Hit by Third DeFi Hack
A DeFi project called Abracadabra has been exploited for about $1.7 million. A blockchain security firm, Go Security, identified the breach on October 4. The attacker managed to manipulate the platform’s smart contract to bypass solvency checks, which allowed them to borrow assets beyond the intended limit.
For more incidents, click here!
📢 Cyber News
7. Qantas Wins Injunction Before Data Leak
In July, Qantas obtained an injunction to prevent the publication of customer data stolen in a cyberattack. Despite this, the threat actors—ShinyHunters and Scattered Spider—ignored the order and later leaked court documents related to it.
8. Flagstar Settles Accellion Breach Case
Flagstar Bank will pay $31.5 million to settle a class-action lawsuit after a data breach exposed the personal information of 2.2 million customers. The settlement provides affected individuals with up to $25,000 for documented losses, three years of credit monitoring, and a portion of the remaining settlement fund.
9. ParkMobile Settles 2021 Data Breach
A recent class action lawsuit settlement with ParkMobile has left 22 million users affected by a 2021 data breach with a disappointing form of compensation. Instead of cash, they’re being offered a $1 credit that can only be used in the app, comes with an expiration date, and must be redeemed manually.
For more news click here
📈Cyber Stocks
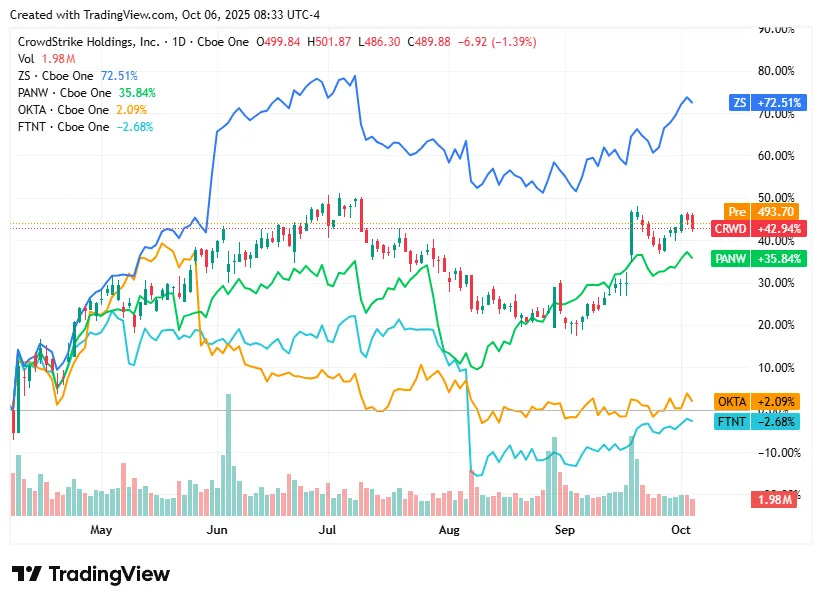
On Monday, 6th October, cybersecurity stocks edged lower as investors turned cautious following last week’s rally. A mix of profit-taking, renewed concerns about high valuations, and broader tech market weakness weighed on the sector. Despite the dip, long-term sentiment toward cybersecurity remained strong, supported by sustained global demand for AI-enhanced and cloud-based defense solutions.
CrowdStrike closed at $489.88, down 1.4%, as investors booked profits after recent highs and weighed the sustainability of its AI-driven growth momentum.
Zscaler ended at $305.41, down 0.7%, reflecting concerns over competition and tempered optimism following its recent earnings surge
Palo Alto Networks finished at $207.19, down 1.0%, amid investor skepticism over integration challenges tied to its CyberArk acquisition.
Okta settled at $93.30, down 1.7%, pressured by valuation concerns and questions over growth consistency in the identity management space.
Fortinet closed at $85.79, down 0.6%, with investors cautious about slowing firewall upgrade cycles despite steady demand for network security.
💡 Cyber Tip
⚠️ Oracle Issues Security Alert on Critical E-Business Suite Flaw
Oracle has released an urgent Security Alert for a critical vulnerability affecting Oracle E-Business Suite (versions 12.2.3 to 12.2.14). This flaw allows remote code execution without authentication, meaning attackers can exploit it without a username or password.
✅ What you should do
Apply the latest Oracle Security Alert patches immediately.
Ensure the October 2023 Critical Patch Update is installed first — it’s required for this fix.
If you’re running an older or unsupported version, upgrade to a supported release to receive security updates.
Review Oracle’s provided indicators of compromise (IOCs) such as suspicious IPs or commands to check for signs of intrusion.
🔒 Why this matters
This vulnerability can give attackers full control of affected systems remotely, posing a major risk to enterprise data. Oracle has confirmed active scanning and recommends immediate patching to prevent exploitation. Keeping software on supported versions and promptly applying security updates remains the most effective defense against these high-impact attacks.
📚 Cyber Book
Phishing, Vishing, & Smishing...Oh My! by Marc Weathers
That concludes today’s briefing . You can check the top headlines here!
Copyright © 2025 CyberMaterial. All Rights Reserved.
Follow CyberMaterial on:
Substack, LinkedIn, Twitter, Reddit, Instagram, Facebook, YouTube, and Medium.