Cyber Briefing: 2025.09.24
AWS flaw exploited, SonicWall rootkit removed, BadIIS via SEO, US agency breached, Boyd & Morrisroe hit, telecom threat stopped, record DDoS blocked.
👉 What's happening in cybersecurity today?
Welcome to Cyber Briefing, the newsletter that informs you about the latest cybersecurity advisories, alerts, incidents and news every weekday.
First time seeing this? Please Subscribe
🚨 Cyber Alerts
1. Hackers Target AWS IMDS and Steal Credentials
A new report from cloud security company Wiz found a security flaw in the Linux utility Pandoc is being actively exploited to attack Amazon Web Services (AWS). This vulnerability, known as CVE-2025-51591, is a type of Server-Side Request Forgery (SSRF) that allows attackers to steal credentials from AWS’s Instance Metadata Service (IMDS).
2. SonicWall SMA100 Update Removes Rootkit
SonicWall released a firmware update for its SMA 100 series devices to remove rootkit malware. The update was prompted by a Google Threat Intelligence Group report on a threat actor, UNC6148, using the malware to maintain persistent access on end-of-life devices.
3. BadIIS Malware Spreads Via SEO Poisoning
Cybersecurity researchers are highlighting a malicious SEO campaign, dubbed Operation Rewrite, that’s using BadIIS malware to target users in East and Southeast Asia, particularly Vietnam. The campaign, which researchers believe is run by a Chinese-speaking threat actor, manipulates search engine results to redirect victims from legitimate websites to scam sites, often for gambling or pornography.
For more alerts, click here!
💥 Cyber Incidents
4. GeoServer Flaw Breaches US Agency Network
An unpatched vulnerability in GeoServer, tracked as CVE-2024-36401, allowed threat actors to breach a U.S. federal agency. This critical remote code execution flaw was later added to CISA’s Known Exploited Vulnerabilities catalog.
5. Boyd Gaming Reports Data Breach After Attack
Boyd Gaming, a major U.S. casino company, recently revealed that a cyberattack led to a data breach. The incident compromised information belonging to its employees and a small number of other individuals, although the company states that its operations were not affected.
6. Morrisroe UK Company Hit By Cyber Attack
A construction company, Morrisroe Ltd, has been the latest victim of a cyberattack, which may have compromised the personal and financial data of its employees. In response, the company has asked its staff to be extra vigilant and report any suspicious activity to their banks.
For more incidents, click here!
📢 Cyber News
7. Secret Service Dismantles UN Telecom Threat
In New York, just as world leaders gathered for the U.N. General Assembly, the Secret Service secretly dismantled a vast, hidden telecom network. This system, made up of over 300 SIM servers with more than 100,000 SIM cards, could have crippled cell towers, jammed 911 calls, and caused widespread chaos, posing a major threat to the city’s infrastructure at a time of heightened vulnerability.
8. Firefox Lets Devs Roll Back Bad Updates
Mozilla now allows Firefox extension developers to roll back to previous, approved versions, which helps them quickly fix critical bugs. Once an extension is reverted, it can’t be installed by new users, and existing users will automatically revert to the older version within 24 hours.
9. Cloudflare Mitigates 22Tbps DDoS Attack
Cloudflare recently mitigated a record-breaking distributed denial-of-service (DDoS) attack that peaked at 22.2 terabits per second (Tbps) and 10.6 billion packets per second (Bpps). This attack was 12% larger than the company’s previous record, but Cloudflare did not share additional technical details.
For more news, click here!
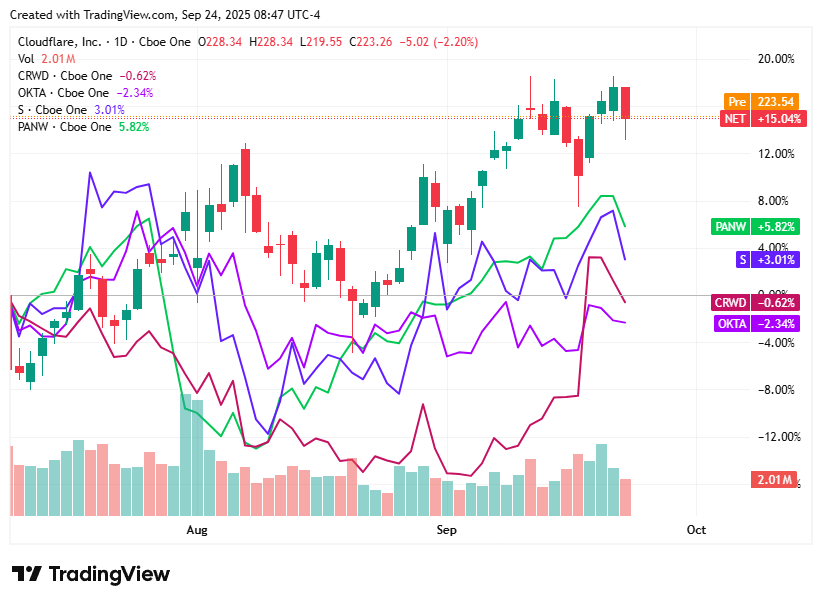
📈Cyber Stocks
On Wednesday, September 24, 2025, cybersecurity equities traded broadly lower as the sector mirrored the wider tech market pullback. Investors rotated out of high-growth names amid concerns about valuations and macroeconomic uncertainty. Although demand for AI-driven platforms and enterprise security solutions remains strong, overall sentiment was cautious, shaped by both market-wide pressures and company-specific developments.
Cloudflare (NET) closed at $223.26, down 2.20%, as macro-driven selling and growth stock rotation overshadowed optimism around its AI and edge networking services.
CrowdStrike (CRWD) finished at $484.10, down 1.83%, with profit-taking after strong ARR guidance compounded by investor scrutiny of high valuations in the cybersecurity sector.
Okta (OKTA) ended at $92.20, slipping 0.22%, as competitive challenges in identity management continued to weigh on sentiment despite growing long-term demand.
SentinelOne (S) settled at $18.46, falling 3.96%, pressured by concerns about forward guidance and volatility among smaller high-growth security firms.
Palo Alto Networks (PANW) closed at $203.25, down 2.35%, as questions about the near-term impact of its acquisition strategy weighed on shares despite its strong position in AI-enhanced cybersecurity.
💡 Cyber Tip
☁️ Hackers Target AWS IMDS via Pandoc Flaw
A new flaw in the Linux tool Pandoc is being exploited to target Amazon Web Services (AWS). Attackers are abusing the software to trick AWS into handing out temporary credentials from the Instance Metadata Service (IMDS), which can then be used to access cloud resources like storage and databases. While Wiz researchers observed attempts, the attacks failed where AWS’s more secure IMDSv2 was enforced.
✅ What you should do
Enable IMDSv2 across all AWS EC2 instances
Use Pandoc with “sandbox mode” to block malicious content
Apply the principle of least privilege for IAM roles
Monitor for suspicious cloud activity that could indicate credential misuse
🔒 Why this matters
This attack shows how even niche tools can become an entry point into cloud environments. Enforcing IMDSv2 and tightening IAM controls can block these kinds of credential theft attempts before they lead to full-scale breaches.
📚 Cyber Book
Introduction to Online Safety: A Practical Guide to Cybersecurity by John G. Jacob
That concludes today’s briefing . You can check the top headlines here!
Copyright © 2025 CyberMaterial. All Rights Reserved.
Follow CyberMaterial on:
Substack, LinkedIn, Twitter, Reddit, Instagram, Facebook, YouTube, and Medium.