Cyber Briefing: 2025.09.22
FBI warns on spoofed IC3, macOS hit by info-stealers, SonicWall urges resets, EU airports disrupted, Qilin leads 467 ransomware attacks in August.
👉 What's happening in cybersecurity today?
Welcome to Cyber Briefing, the newsletter that informs you about the latest cybersecurity advisories, alerts, incidents and news every weekday.
First time seeing this? Please Subscribe
🚨 Cyber Alerts
The FBI issued a public warning about scammers creating fake versions of its official Internet Crime Complaint Center (IC3) website to steal people's personal information. These fraudulent sites are designed to trick users who are trying to report cybercrimes like identity theft or hacking.
Threat actors are using fraudulent GitHub repositories to impersonate major brands and infect macOS users with info-stealing malware. The attackers use search engine optimization (SEO) to promote these fake repositories, tricking users into downloading malicious software like the Atomic macOS Stealer (AMOS).
SonicWall is advising customers to reset all credentials after an exposed cloud backup feature risked unauthorized access to their networks. These exposed backup files contained sensitive information that could potentially be used by malicious actors.
For more alerts, click here!
💥 Cyber Incidents
A cyberattack on a widely used airport check-in system caused long lines and flight delays across several major European airports on Friday. The disruption, which impacted software from the company Collins Aerospace, forced airports to switch to manual operations like hand-written baggage tags and boarding passes.
The ransomware gang Qilin has claimed responsibility for a cyberattack on Spartanburg County, South Carolina, alleging a significant data breach and widespread disruption of services. While the county confirmed a limited breach of employee data, they have not verified the gang's more extensive claims regarding the scale of the attack and the nature of the compromised information.
A gamer raising money for cancer treatment lost $32,000 from his crypto wallet after a verified game he downloaded from Steam was secretly updated with malware. The game, called Block Blasters, was later found to have drained nearly $150,000 from hundreds of other Steam users.
For more incidents, click here!
📢 Cyber News
The Royal Canadian Mounted Police (RCMP) has shut down the TradeOgre cryptocurrency exchange and seized over $40 million in assets, marking the first time Canadian law enforcement has taken down a crypto exchange. The exchange was targeted for operating illegally without registering with the Financial Transactions and Reports Analysis Centre of Canada (FINTRAC) and failing to comply with Know Your Customer (KYC) policies, which investigators believe made it a hub for money laundering.
A pair of highly active Russian hacking units, Turla and Gamaredon, have been caught working together to compromise high-value devices in Ukraine, according to security researchers. This unusual collaboration involves one group known for its sophisticated and stealthy tactics and another that operates on a much broader, less subtle scale.
Qilin remained the most active ransomware group in August, but the rapid growth of rivals like Sinobi and The Gentlemen suggests a shift in the threat landscape. A total of 467 ransomware attacks occurred in August, with the U.S. accounting for nearly 60% of them.
For more news, click here!
📈Cyber Stocks
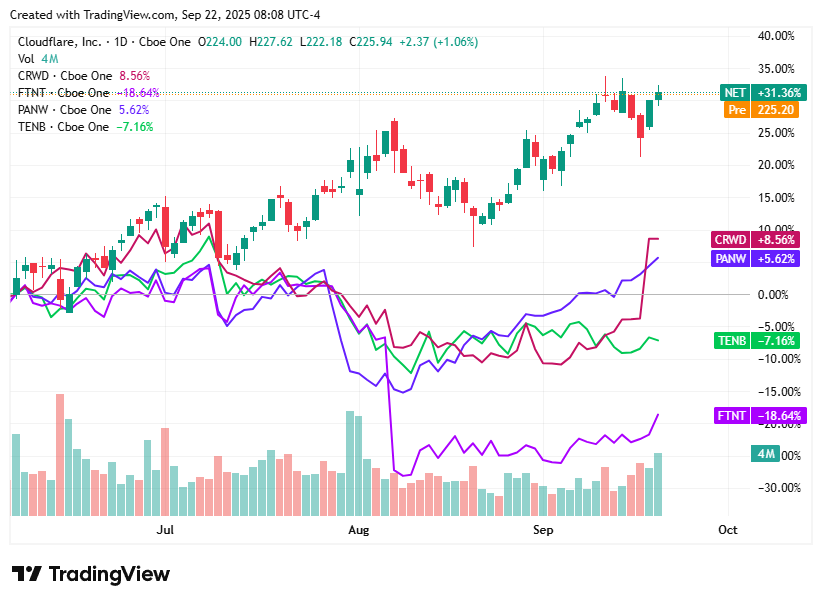
On Monday, September 22, 2025, cybersecurity pure-play stocks traded with moderate strength as investors weighed stabilizing inflation data, expectations for Federal Reserve policy clarity, and company-specific developments that continued to shape sentiment in the sector. Gains were generally supported by strong product demand, positive analyst ratings, and enthusiasm around AI-driven security platforms.
Cloudflare (NET) closed at $225.94, up 1.02 percent, as investors responded positively to steady revenue growth of nearly 28 percent year over year and guidance that reinforced confidence in its edge networking and Zero Trust offerings.
CrowdStrike (CRWD) ended at $502.55, essentially flat, with sentiment supported by strong long-term ARR guidance and new AI-driven platform announcements at its recent Fal.Con 2025 investor event.
Fortinet (FTNT) finished at $84.21, gaining 3.98 percent on renewed demand for its firewall refresh cycle and relief that its quarterly revenue momentum held steady despite macroeconomic concerns.
Palo Alto Networks (PANW) settled at $208.19, up 1.22 percent, as favorable analyst ratings and its acquisition of CyberArk strengthened optimism around its leadership in identity-focused cybersecurity and AI-augmented tools.
Tenable (TENB) closed at $30.23, trading flat as strong demand for its vulnerability and exposure management platform was tempered by concerns about profitability and less aggressive forward guidance compared to peers.
💡 Cyber Tip
🌐 FBI Warns of Spoofed IC3 Websites Stealing Data
The FBI has issued a warning about fraudulent websites impersonating the Internet Crime Complaint Center (IC3) to trick victims into sharing sensitive information. These fake sites use lookalike domains such as .com instead of the legitimate .gov and are designed to harvest personal and financial details from people trying to report cybercrime.
✅ What you should do:
Always type www.ic3.gov directly into your browser to access the real IC3, and report any suspicious or spoofed IC3 websites directly to the FBI
Avoid clicking on sponsored search results, which can lead to fake sites
Verify that the URL ends in .gov, since IC3 does not use any other domains
Never pay money to recover funds, because IC3 will never request payment
🔒 Why this matters
Scammers are exploiting trust in IC3 to steal personal data and money from victims of cybercrime, turning one scam into another. Awareness and careful verification of websites are essential to avoid being victimized twice.
📚 Cyber Book
The Ask Leo! Guide to Staying Safe on the Internet by Leo Notenboom
That concludes today’s briefing . You can check the top headlines here!
Copyright © 2025 CyberMaterial. All Rights Reserved.
Follow CyberMaterial on:
Substack, LinkedIn, Twitter, Reddit, Instagram, Facebook, YouTube, and Medium.