Cyber Briefing: 2025.09.01
North Korea’s APT37 is deploying RokRAT in phishing campaigns against academics. Android devices are being targeted by Brokewell malware spread via fake TradingView ads.
👉 What's happening in cybersecurity today?
Welcome to Cyber Briefing, the newsletter that informs you about the latest cybersecurity advisories, alerts, incidents and news every weekday.
First time seeing this? Please Subscribe
🚨 Cyber Alerts
North Korea's state-sponsored hacking group, ScarCruft (APT37), launched "Operation HanKook Phantom," a phishing campaign using a fake newsletter and malicious files to target South Korean academics, researchers, and ex-officials. The campaign deploys the RokRAT malware, which enables data theft, espionage, and remote control of compromised systems through a complex, multi-stage infection process designed to evade detection.
Cybercriminals are exploiting Meta's advertising platforms by promoting fake offers of a free TradingView Premium app for Android, which actually distributes the dangerous Brokewell malware to steal cryptocurrency and other sensitive data. This malicious campaign, operational since at least late July, specifically targets mobile users, gaining full control over their devices by exploiting accessibility permissions.
WhatsApp has issued threat notifications to users who were targeted by advanced, "zero-click" spyware in the last 90 days. The malicious campaign exploited vulnerabilities in both WhatsApp and the device's operating system to compromise a user's data without any interaction from the victim.
For more alerts, click here!
💥 Cyber Incidents
4. MathWorks Confirms Cyberattack Data Stolen
MathWorks, the company behind MATLAB and Simulink, has confirmed a cyberattack that resulted in the theft of sensitive personal information from an undisclosed number of users between April and May 2025. The compromised data may include names, addresses, Social Security Numbers, and other personal information, potentially exposing users to a risk of identity theft and fraud.
5. Fraudster Stole Millions From Baltimore
A scammer successfully defrauded the city of Baltimore out of over $1.5 million by impersonating a vendor and tricking city staff into changing the vendor's bank account details. This incident, which is a classic example of a Business Email Compromise (BEC) attack, highlights the city's ongoing struggle with weak internal controls and insufficient fraud prevention measures.
6. Google Warns Salesloft Breach Hit Accounts
The Salesloft Drift breach is now considered larger than initially thought, with Google reporting that attackers also used stolen OAuth tokens to access a small number of Google Workspace email accounts. Google has warned all Salesloft Drift customers to treat all authentication tokens stored in or connected to the platform as potentially compromised and to take immediate action to revoke and rotate credentials.
For more incidents, click here!
📢 Cyber News
7. Amazon Dismantles Russian APT29 Network
Amazon's threat intelligence team uncovered a sophisticated watering hole campaign in late August 2025, orchestrated by the Russian state-sponsored threat actor APT29 (Midnight Blizzard), which compromised legitimate websites to redirect users to fake Cloudflare pages to harvest credentials and gain access to corporate environments. The operation marked an evolution in the group's tactics, as they used malicious JavaScript injections instead of traditional phishing to broaden their victim pool and achieve persistent access through Microsoft's device code authentication flow.
8. Microsoft To Enforce MFA For Azure
Beginning in October, Microsoft will enforce multi-factor authentication (MFA) for all Azure resource management actions, a move that is part of the company's "Secure Future Initiative" aimed at protecting clients from unauthorized access. This change, which will be gradually rolled out across global tenants, requires users to enable MFA on a variety of tools, including the Azure CLI, PowerShell, SDKs, and APIs, though global administrators have the option to postpone the enforcement until July 2026.
9. Apple May Remove SIM Card In iPhone 17
Apple is preparing to expand its eSIM-only iPhone strategy to the European Union and other international markets, as evidenced by mandatory training for authorized reseller employees. This shift, which is expected to be announced at the "Awe Dropping" event on September 9, would remove the physical SIM card slot from upcoming iPhone 17 models in many countries.
For more news, click here!
📈Cyber Stocks
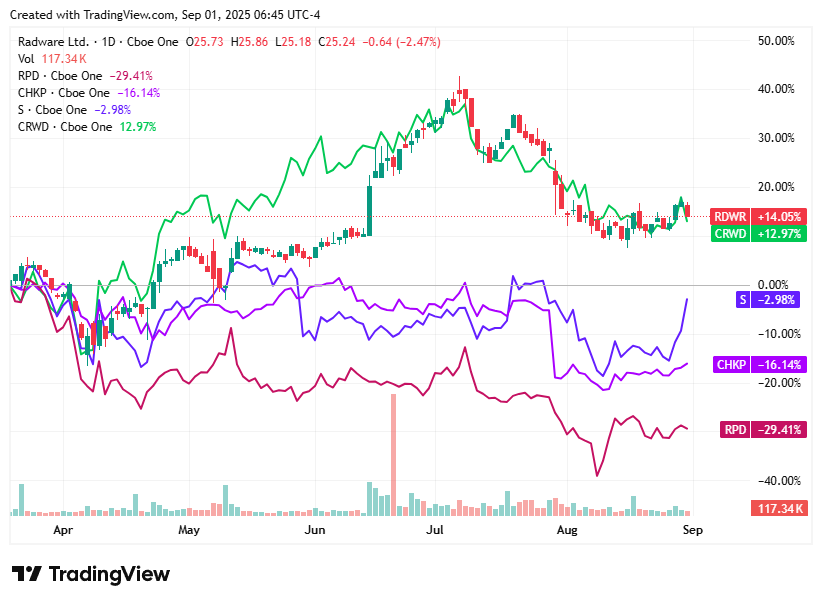
At the early hours of Monday, September 1, 2025, cybersecurity stocks showed mixed performance as investors balanced sector resilience, recent earnings momentum, and valuation pressures.
Radware (RDWR) closed at $25.24, slipping as profit-taking followed recent recognition in the KuppingerCole 2025 Leadership Compass for web application and API protection.
Rapid7 (RPD) ended at $20.71, edging lower as growth concerns and valuation pressure weighed on sentiment despite steady full-year guidance.
Check Point Software Technologies (CHKP) settled at $193.14, climbing modestly as investors favored its stable margins and dependable post-earnings performance.
SentinelOne (S) finished at $18.86, rising strongly on momentum from its Q2 earnings beat and boosted by a raised “Outperform” rating from Bernstein.
CrowdStrike (CRWD) closed at $423.70, declining after mixed revenue guidance tempered enthusiasm, even as ARR growth and acquisition upside provided longer-term support.
💡 Cyber Tip
📱 WhatsApp Warns of Zero-Click Spyware Attacks
WhatsApp has sent alerts to users targeted by zero-click spyware in the past three months. This advanced attack chained together vulnerabilities in WhatsApp and device operating systems, allowing attackers to compromise data without any user interaction. Victims included high-risk individuals such as journalists and human rights defenders, showing signs of state-sponsored surveillance activity.
✅ What you should do
Update WhatsApp and your device OS immediately to the latest version
Consider enabling Lockdown Mode on iOS or Advanced Protection on Android for added defense
Treat any suspicious activity or unusual device behavior as a potential compromise
If you receive a threat notification, perform a full factory reset as advised
Stay vigilant, especially if you are in a high-risk group like activists, researchers, or political figures
🔒 Why this matters
Zero-click spyware is one of the most dangerous forms of attack because it requires no user action. By exploiting multiple flaws across apps and operating systems, attackers can silently infiltrate devices and exfiltrate sensitive data. Regular patching and enabling advanced security features are the strongest defenses.
📚 Cyber Book
Mastering Malware Analysis: The complete malware analyst's guide by Alexey Kleymenov , Amr Thabet
That concludes today’s briefing . You can check the top headlines here!
Copyright © 2025 CyberMaterial. All Rights Reserved.
Follow CyberMaterial on:
Substack, LinkedIn, Twitter, Reddit, Instagram, Facebook, YouTube, and Medium.