Cyber Briefing: 2025.08.27
AI prompts hidden in images steal data, MixShell hits supply chains, WhatsApp flaw risks RCE, NJ & Auchan breached, Salesloft OAuth theft, NK IT threat, Durov protests, $29M hacker extradited.
👉 What's happening in cybersecurity today?
Welcome to Cyber Briefing, the newsletter that informs you about the latest cybersecurity advisories, alerts, incidents and news every weekday.
First time seeing this? Please Subscribe
🚨 Cyber Alerts
1. AI Attack Hides Prompts In Images
Researchers have created a new attack that steals user data by embedding malicious prompts in images processed by AI systems. The prompts, invisible to the human eye, become readable by the AI when the image is downscaled, leading to data exfiltration without the user's knowledge.
2. MixShell Hts US Supply Chain Firms
In a new and concerning cyberattack, threat actors are using a social engineering campaign named ZipLine to target companies critical to the global supply chain, luring them into multi-week conversations before deploying the in-memory malware MixShell. Unlike typical phishing attacks, this campaign initiates contact through a company's public 'Contact Us' form and patiently builds trust before delivering the malicious payload.
3. WhatsApp Desktop Code Execution Risk
WhatsApp Desktop on Windows is vulnerable to a flaw that could allow arbitrary code execution through maliciously crafted Python archive files (.pyz). Attackers can gain complete control of a user's system with a single click, as the application fails to properly handle and validate these files, and Meta has not yet classified the issue as a security vulnerability.
For more alerts, click here!
💥 Cyber Incidents
4. NJ Social Services Reports Data Breach
Legacy Treatment Services in New Jersey recently confirmed a data breach from October 2024 that compromised the personal and medical information of 41,826 people. The ransomware group Interlock, which claimed responsibility for the attack, reportedly stole 170 GB of sensitive data, including Social Security numbers, financial information, and clinical records.
5. Auchan Retailer Reports Data Breach
French retailer Auchan has informed several hundred thousand of its customers that their sensitive loyalty account data was exposed in a recent cyberattack. The exposed data includes names, addresses, phone numbers, and loyalty card numbers, though the company states that financial data and passwords were not compromised.
6. Salesloft Breach Exposes OAuth Tokens
Hackers breached Salesloft to steal OAuth and refresh tokens from its Drift chat agent integration, using them to pivot into customer Salesforce environments and exfiltrate sensitive data. The threat actors, identified by Google's Threat Intelligence team as UNC6395, sought to steal credentials like AWS access keys, passwords, and Snowflake tokens to further their access and compromise other systems.
For more incidents, click here!
📢 Cyber News
7. Tokyo Meeting on North Korea IT Threat
In a collaborative effort, multiple governments and companies convened in Tokyo to address North Korea's ongoing campaign of illicitly hiring its IT workers. The forum, organized by the U.S. State Department with Japan and South Korea, aimed to foster a collective defense against this scheme, which funds North Korea's weapons programs.
8. Durov Calls France Arrest Unfair
Telegram CEO Pavel Durov, who was briefly detained in France a year ago for alleged criminal activity on his platform, has been vocally critical of the ongoing legal process, calling his arrest "absurd" and complaining about the requirement to return to France every 14 days without an appeal date. Despite his release on bail and permission to travel, he remains under judicial supervision while the complicated case, which he argues is unprecedented and based on the actions of his users, slowly proceeds.
9. $29M Hacking Ring Mastermind Extradited
A Chinese national suspected of leading a hacking group that stole $29 million from Korean victims, including BTS member Jungkook, has been extradited from Thailand to Korea. The suspect allegedly used illegally obtained personal data to open new mobile phone accounts in victims' names to access their financial and cryptocurrency accounts.
For more news, click here!
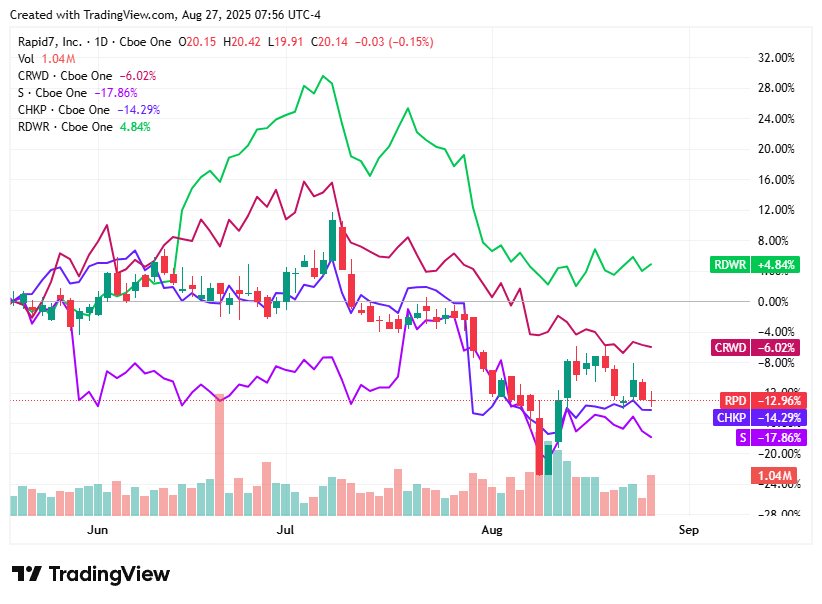
📈Cyber Stocks
As markets opened on Wednesday, August 27, 2025, cybersecurity stocks traded with muted momentum as investors looked ahead to key earnings reports and industry conference updates.
Radware (RDWR) inched up 0.91% to $24.92, benefiting from lingering optimism around strong Q2 execution and recent analyst upgrades despite broader valuation concerns.
Rapid7 (RPD) slipped 0.15% to $20.14, as cautious sentiment around slowing growth and revised guidance overshadowed stability in its subscription revenues.
Check Point Software Technologies (CHKP) edged down 0.06% to $187.62, with investors awaiting strategic commentary from its participation in the Deutsche Bank Technology Conference.
SentinelOne (S) dropped 1.1% to $16.42, pressured by pre-earnings jitters as traders weighed upcoming results against steady ARR growth and new institutional backing.
CrowdStrike (CRWD) declined 0.35% to $417.60, as concerns over softening EPS growth tempered enthusiasm, even as anticipation built for its post-market earnings release later in the day.
💡 Cyber Tip
💻 WhatsApp Desktop Users at Risk of Code Execution via Malicious Files
A flaw in WhatsApp Desktop for Windows exposes users to remote code execution if they open specially crafted Python archive files (.pyz). Attackers can send a malicious .pyz file through WhatsApp, and with a single click, the file executes if Python is installed on the system. This grants attackers full control of the victim’s computer, including access to files, data theft, and malware installation. The issue remains unpatched as Meta has not yet classified it as a vulnerability.
✅ What you should do:
Do not open or preview .pyz files received via WhatsApp or other messaging apps
If you do not use Python, consider removing it from Windows PATH settings or uninstalling it altogether
Use endpoint protection that can detect suspicious script execution
Keep backups of important files to reduce impact if compromised
Be extra cautious of files with unfamiliar extensions sent by unknown or even trusted contacts
🔒 Why this matters
This flaw turns a trusted communication app into an attack vector. Because it leverages normal file handling on Windows, it bypasses common defenses and can fool non-technical users. Until Meta issues a fix or mitigation, the best defense is user awareness and strict caution with unknown file types.
📚 Cyber Book
Hate Speech against Women Online: Concepts and Countermeasures by Louise Richardson-Self
That concludes today’s briefing . You can check the top headlines here!
Copyright © 2025 CyberMaterial. All Rights Reserved.
Follow CyberMaterial on:
Substack, LinkedIn, Twitter, Reddit, Instagram, Facebook, YouTube, and Medium.