Cyber Briefing: 2025.08.26
Fake CMC scam tricks crypto execs!; 77 malware pulled; AI browsers prompt risk; Farmers breach 1M; Arch DDoS!; Google to verify dev IDs; NPD relaunch.
👉 What's happening in cybersecurity today?
Welcome to Cyber Briefing, the newsletter that informs you about the latest cybersecurity advisories, alerts, incidents and news every weekday.
First time seeing this? Please Subscribe
🚨 Cyber Alerts
1. Fake CoinMarketCap Journalists Scam
A new spear-phishing campaign is using fake CoinMarketCap journalist profiles to trick crypto executives into a malicious Zoom interview. The elaborate scheme is designed to gain remote control of a victim's computer, potentially leading to malware deployment, data theft, and the loss of cryptocurrency wallets.
2. Malicious Apps Removed from Google Play
Security researchers discovered 77 malicious Android apps with over 19 million installations on Google Play, which were found to be distributing various malware families, including the Anatsa banking trojan. This trojan has evolved to target more than 831 financial institutions worldwide, using sophisticated anti-analysis techniques to evade detection and steal user credentials.
3. AI Browsers Pose Prompt Injection Risk
Artificial intelligence (AI) browsers are vulnerable to "prompt injection," a method where malicious instructions are embedded in web content to trick the AI into performing unauthorized actions. This is especially dangerous with "agentic browsers," which automate complex tasks and could be manipulated to steal sensitive data or make unauthorized purchases.
For more alerts, click here!
💥 Cyber Incidents
4. Farmers Insurance Cyberattack Hits 1M
Over one million customers of Farmers Insurance and its subsidiaries had their personal information exposed in a cyberattack on a third-party vendor. The stolen data included names, birth dates, and driver's license numbers, prompting the company to offer affected individuals two years of identity theft protection.
5. Arch Linux Hit by Ongoing DDoS Attack
A prolonged DDoS attack since mid-August 2025 has crippled core Arch Linux services, including its website, forums, and the Arch User Repository (AUR), forcing the community to rely on workarounds. The volunteer-driven team is working with providers to mitigate the attack but is facing a dilemma over adopting commercial solutions like Cloudflare, which may conflict with the project's open-source ethos. This incident highlights the security vulnerabilities of open-source projects and has sparked a broader conversation about the need for enhanced security measures and sustainable defenses against cyber threats.
6. Hackers Disrupt Iran Merchant Fleet Again
Hacker group Lab Dookhtegan, or "Sewn Lips," claims to have disrupted communications for 39 Iranian tankers and 25 containerships. The group reportedly achieved this by infiltrating Fanava Group, an Iranian IT and telecommunications company that provides services to the National Iranian Tanker Company (NITC) and the Islamic Republic of Iran Shipping Lines (IRISL).
For more incidents, click here!
📢 Cyber News
7. Google to Verify Android Developers
Google is implementing a new policy requiring all developers to verify their identity in order to distribute apps on certified Android devices, even for apps distributed outside of the Google Play Store. This initiative, which will roll out in phases starting in October 2025 and become mandatory in select regions by September 2026, is aimed at increasing accountability and combating malicious apps from repeat offenders.
8. Linux Celebrates 34 Years Worldwide
On August 25, 2025, the world celebrates the 34th anniversary of Linux, a free operating system that began as a hobby project by a 21-year-old Finnish student, Linus Torvalds. What started as a small project has now become the backbone of modern digital infrastructure, powering everything from smartphones to supercomputers.
9. National Public Data Relaunches After Breach
National Public Data (NPD), a data broker that leaked 2.9 billion records of sensitive personal information, is back online under new ownership, raising serious concerns about the lax regulation of the data brokerage industry. The new company, Perfect Privacy LLC, is operating the same services, and the same compromised data from the breach remains searchable, despite ongoing lawsuits against the previous owner.
For more news, click here!
📈Cyber Stocks
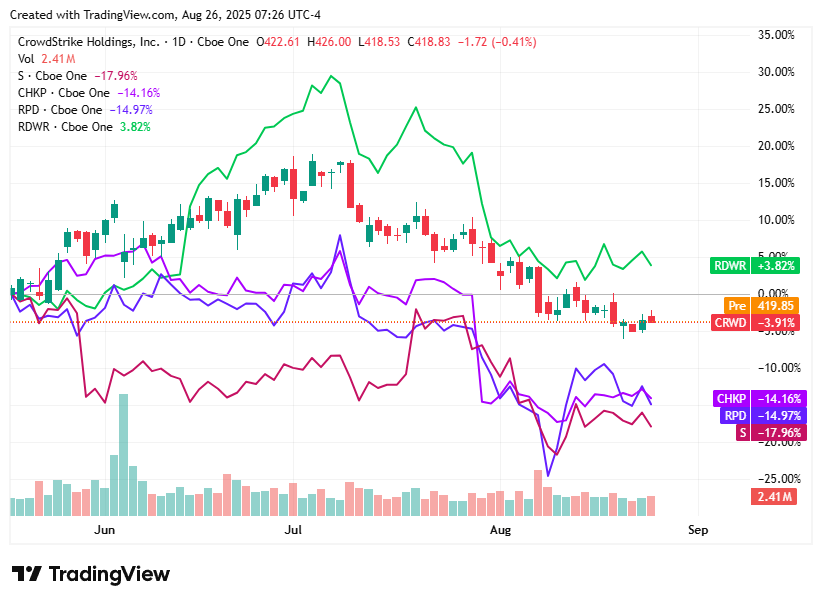
As trading opened on Tuesday, August 26, 2025, cybersecurity stocks leaned lower as investors weighed upcoming earnings, valuation pressures, and shifting institutional positions.
Radware (RDWR) slipped 1.79% to $24.71, with profit-taking and valuation concerns offsetting optimism from recent analyst upgrades following its strong Q2 results.
Rapid7 (RPD) fell 2.75% to $20.17, reversing part of its recent rally as declining trading volume signaled fading momentum.
Check Point Software Technologies (CHKP) eased 1.44% to $187.72, pressured by cautious analyst sentiment and mixed institutional moves despite a solid earnings beat earlier this month.
SentinelOne (S) dropped 2.27% to $16.58, as investors grew cautious ahead of its Q2 earnings release, balancing volatility signals against longer-term institutional interest.
CrowdStrike (CRWD) edged down 0.43% to $418.83, as strong technicals were tempered by uncertainty around its upcoming quarterly results.
💡 Cyber Tip
📱 Uninstall Malicious Apps Removed from Google Play
Security researchers have uncovered 77 malicious Android apps on Google Play with more than 19 million installs. These apps acted as droppers, spreading multiple malware families, including the Anatsa banking trojan, which now targets hundreds of financial institutions worldwide. The apps disguised themselves as legitimate utilities like file managers but were designed to steal banking credentials, financial data, and other sensitive information.
✅ What you should do
Uninstall any suspicious apps recently downloaded from Google Play, especially utilities requesting excessive permissions
Review app permissions and revoke unnecessary access (e.g., Accessibility services)
Update Android devices and ensure Google Play Protect is enabled
Use mobile security tools to scan for known malware strains
Monitor financial accounts for unusual activity and reset credentials if exposure is suspected
🔒 Why this matters
These malicious apps show how attackers can weaponize even official app stores to spread sophisticated malware. Anatsa and similar families use advanced evasion techniques to steal banking and crypto credentials at scale. Verifying app legitimacy and limiting permissions are critical to keeping your device secure.
📚 Cyber Book
Vapor: A True Story of How I Fell Victim to Catfishing by Debra Danielsen
That concludes today’s briefing . You can check the top headlines here!
Copyright © 2025 CyberMaterial. All Rights Reserved.
Follow CyberMaterial on:
Substack, LinkedIn, Twitter, Reddit, Instagram, Facebook, YouTube, and Medium.