Cyber Briefing: 2025.08.25
Go SSH tool steals creds, Android backdoor spyware, Tableau flaw, Grok chats leaked, Data I/O ransomware, Russian TV hacked, NIST crypto, FTC warning, Redis malware.
👉 What's happening in cybersecurity today?
Welcome to Cyber Briefing, the newsletter that informs you about the latest cybersecurity advisories, alerts, incidents and news every weekday.
First time seeing this? Please Subscribe
🚨 Cyber Alerts
1. Fake Go SSH Tool Steals Credentials
A malicious Go module, designed to appear as an SSH brute-force tool, was found to secretly steal credentials. Once it successfully logs in to a system, it exfiltrates the username, password, and target IP address to a Telegram bot controlled by the attacker.
2. Fakes Android Antivirus Has Malware
A new Android malware, dubbed 'Android.Backdoor.916.origin,' is targeting Russian business executives by masquerading as an antivirus tool from Russia's Federal Security Services (FSB). The sophisticated spyware, which researchers believe is for targeted attacks, can steal sensitive data, eavesdrop on conversations, and exfiltrate information from popular messaging apps.
3. Tableau Server Flaw Enables Uploads
A critical security vulnerability in Tableau Server (CVE-2025-26496) allows attackers to upload and execute malicious files by exploiting a type confusion flaw, potentially leading to full system compromise. The issue, along with several other file upload and path traversal vulnerabilities, affects multiple versions of Tableau Server and Tableau Desktop on both Windows and Linux, necessitating immediate patching.
For more alerts, click here!
💥 Cyber Incidents
4. Grok Chat Data Exposed via Google
A significant data exposure has made hundreds of thousands of private conversations with Elon Musk’s AI chatbot, Grok, publicly accessible through search engines. This privacy breach was caused by the platform's "share" feature, which created public, indexable URLs for conversation transcripts without the users' explicit knowledge or consent.
5. Data I/O Halts Systems After Attack
Electronics manufacturer Data I/O reported a ransomware attack to the SEC on August 16, 2025, forcing the company to take key operational systems offline. While some systems have been restored, the attack has temporarily disrupted vital functions like manufacturing and shipping, and the full financial impact is still being investigated.
6. Hackers Hijack Russian TV Broadcast
On Ukraine's Independence Day, a cyberattack by Ukrainian partisans successfully hijacked 116 Russian television channels for over three hours, broadcasting uncensored footage of the war's true impact to over 50,000 Russian viewers. This sophisticated operation, which also blocked administrator access to the network, follows another significant cyberattack in July where a pro-Ukraine hacker group claimed to have destroyed thousands of servers and exfiltrated terabytes of data from Russian airline Aeroflot.
For more incidents, click here!
📢 Cyber News
7. NIST Issues Lightweight Crypto Standard
The National Institute of Standards and Technology (NIST) has released Special Publication 800-232, which establishes the Ascon family of algorithms as the new standard for lightweight cryptography. This standard is specifically designed to secure resource-constrained devices like those found in the Internet of Things (IoT), where traditional cryptographic methods are too demanding.
8. FTC Warns Big Tech on Encryption
The FTC has warned major U.S. tech companies that complying with foreign government demands that weaken data security or impose censorship could violate U.S. consumer protection law. This legal reminder, issued via a letter from FTC Chairman Andrew N. Ferguson, emphasizes that companies have a primary obligation to American users to protect their data and freedom of information, regardless of overseas regulatory pressure.
9. New Malware Pushes Cybercrime Limits
Cybersecurity researchers have uncovered multiple campaigns leveraging known vulnerabilities in exposed Redis servers and other devices for malicious purposes like cryptocurrency mining, residential proxy networks, and IoT botnets. These attacks utilize sophisticated, stealthy methods to monetize compromised systems, often flying under the radar by mimicking legitimate software and consuming minimal resources.
For more news, click here!
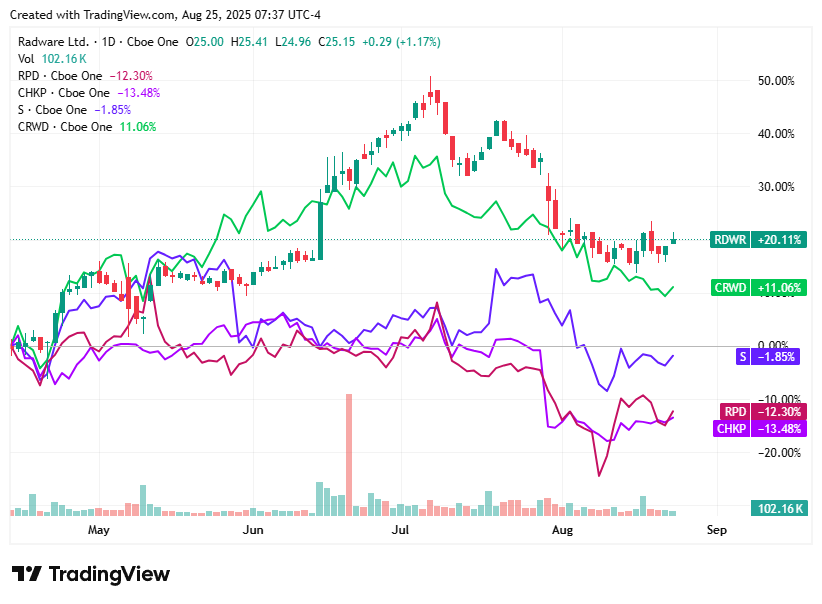
📈Cyber Stocks
At the early hours of Monday, August 25, 2025, cybersecurity stocks showed a cautious but upward tilt as investors balanced earnings momentum, institutional activity, and macroeconomic pressures.
Radware (RDWR) gained 1.17% to $25.15, supported by strong Q2 results that highlighted double-digit revenue growth and robust demand for cloud and AI-driven security offerings.
Rapid7 (RPD) advanced 3.08% to $20.75, continuing a two-week rally as rising trading volumes signaled renewed investor interest despite the stock remaining far below its 52-week high.
Check Point Software Technologies (CHKP) edged up 1.12% to $190.42, with sentiment recovering slightly after a sharp post-earnings decline, as investors balanced an earnings beat against mixed billing trends.
SentinelOne (S) rose 1.83% to $16.96, buoyed by technical buying even as the company faces macro headwinds and elongated sales cycles that pressured its stock performance earlier this month.
CrowdStrike (CRWD) ticked up 1.52% to $420.55, lifted by institutional accumulation from major funds including Vanguard and Goldman Sachs, though tempered by analyst caution following a lowered price target.
💡 Cyber Tip
📊 Update Tableau Server and Desktop to Patch Critical File Upload Flaws
Salesforce has patched multiple vulnerabilities in Tableau Server and Tableau Desktop that allowed attackers to upload and execute malicious files, potentially leading to full system compromise. The most severe bug exploited type confusion during file uploads, while others allowed unrestricted file uploads and path traversal, enabling attackers to overwrite or access sensitive files.
✅ What you should do:
Update Tableau Server and Tableau Desktop to the latest maintenance release immediately
Audit your environment for unexpected uploads or suspicious file activity
Restrict user access to file upload features where possible
Deploy a web application firewall (WAF) to filter malicious upload requests
Monitor system directories for signs of webshells or unauthorized file changes
🔒 Why this matters
These flaws could give attackers remote code execution, persistent backdoors, and access to sensitive system files, allowing them to escalate privileges and move across your network. Patching now is critical to prevent enterprise-wide compromise.
📚 Cyber Book
The Cuckoo's Egg: Tracking a Spy Through the Maze of Computer Espionage by Clifford Stoll
That concludes today’s briefing . You can check the top headlines here!
Copyright © 2025 CyberMaterial. All Rights Reserved.
Follow CyberMaterial on:
Substack, LinkedIn, Twitter, Reddit, Instagram, Facebook, YouTube, and Medium.