Cyber Briefing: 2025.08.19
PyPI blocks expired domain emails, Noodlophile infostealer spreads via fake notices, XenoRAT targets embassies, iiNet & Allianz breached, PayPal logins sold, two hackers sentenced.
👉 What's going on in the cyber world today?
Welcome to Cyber Briefing, the newsletter that informs you about the latest cybersecurity advisories, alerts, incidents and news every weekday.
First time seeing this? Please Subscribe
🚨 Cyber Alerts
1. PyPI Blocks 1800 Expired Domain Emails
The Python Package Index (PyPI) now checks for expired domains to prevent supply chain attacks. This new security measure aims to thwart domain resurrection attacks, where malicious actors take control of abandoned accounts by purchasing expired domains associated with their registered email addresses.
2. Noodlophile Infostealer Uses Fake Notices
Threat actors are targeting businesses with spear-phishing emails that use the guise of legal threats over copyright or intellectual property infringement to deliver the Noodlophile infostealer. These highly-tailored emails, which appear to come from a law firm, are being sent to specific employees and generic company inboxes across the US, Europe, Baltic countries, and the APAC region.
3. XenoRAT Malware Hits South Korea Embassies
A state-sponsored espionage campaign has been targeting foreign embassies in South Korea since March, using multi-stage spear-phishing attacks to deliver XenoRAT malware. The attackers utilize password-protected archives containing a malicious .LNK file that executes a PowerShell script to download the payload from legitimate cloud services and GitHub repositories.
For more alerts, click here!
💥 Cyber Incidents
4. iiNet Breach Exposes 280K Records
In a significant data breach, Australia's second-largest internet service provider, TPG Telecom, has announced that its subsidiary, iiNet, experienced a cyberattack affecting hundreds of thousands of customers. The breach, which was discovered on August 16, 2025, involved an unauthorized third party gaining access to an order management system, compromising various customer data points.
5. Allianz Life Breach Hits 1.1M Customers
Hackers stole the personal information of 1.1 million individuals in a Salesforce data theft attack that impacted U.S. insurance giant Allianz Life in July. The breach, linked to the ShinyHunters extortion group, also affected many other high-profile companies worldwide.
6. Hackers Claim Sale of 15.8M PayPal Logins
A threat actor named Chucky_BF is selling a massive data dump on a hacker forum, allegedly containing over 15.8 million PayPal logins, complete with email and plaintext password pairs. The data, which may be from infostealer malware logs, also includes specific PayPal URLs, making it a valuable tool for criminals.
For more incidents, click here!
📢 Cyber News
7. Nebraska Man Sentenced for Crypto Scheme
A Nebraska man, Charles O. Parks III, received a one-year prison sentence for a cryptocurrency mining scheme. He defrauded two cloud computing providers out of over $3.5 million to mine nearly $1 million worth of cryptocurrency.
8. UK Sentences Serial Hacker to 20 Months
A 26-year-old hacker from the UK, Al-Tahery Al-Mashriky, was sentenced to 20 months in prison after pleading guilty to a range of cybercrimes, including stealing millions of Facebook users' data and hacking government and news websites. His attacks were politically motivated, aimed at pushing the agenda of extremist groups he was associated with.
9. Microsoft Warns Windows 10 Support Ending
Microsoft has issued a final reminder that Windows 10 will reach its end of servicing on October 14, 2025, after which it will no longer receive essential security and preview updates. Customers are advised to upgrade to Windows 11 or enroll in the Extended Security Updates (ESU) program to maintain system security.
For more news, click here!
📈Cyber Stocks
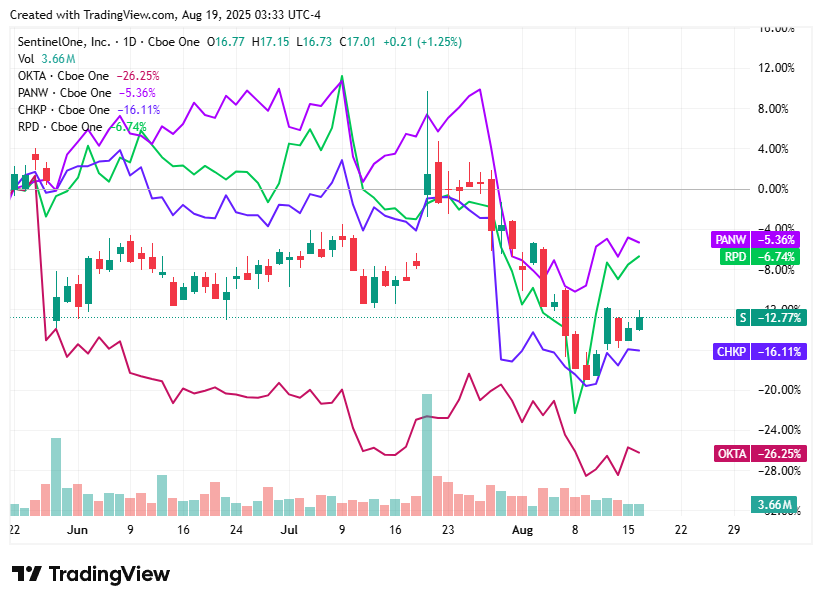
On Tuesday, August 19, 2025, cybersecurity stocks showed a mixed performance as markets digested recent earnings, strategic developments, and recently high valuations.
Okta (OKTA) slipped 0.70% to $91.38, as market participants exercised caution ahead of upcoming earnings and weighed concerns over sustaining growth in an environment of macroeconomic uncertainty
SentinelOne (S) ticked up 1.13% to $17.01, buoyed by continued interest around its AI security platform and support from institutional buying, even amid valuation scrutiny
Check Point Software Technologies (CHKP) eased 0.10% to $188.64, as investor sentiment remained anchored by recent softness in billings growth, despite stabilization in other metrics post-earnings
Rapid7 (RPD) edged up 0.75% to $21.46, lifted by momentum from bullish analyst revisions and confidence in its AI-enhanced security platform, even as it continues to navigate valuation adjustments
Palo Alto Networks (PANW) declined 0.43% to $176.17, as investors balanced enthusiasm from its strong Q4 results and CyberArk acquisition with caution over valuation after an extended rally and expectations of signals from the upcoming Jackson Hole Fed symposium
💡 Cyber Tip
📧 Beware of Fake Legal Threat Emails Spreading Noodlophile Infostealer
Attackers are running a spear-phishing campaign that delivers the Noodlophile infostealer by disguising emails as copyright or intellectual property infringement notices. These fraudulent messages impersonate law firms and are carefully tailored with company details to make the threats appear legitimate. Once an employee opens the malicious attachment or link, the malware executes and steals credentials, financial data, and proprietary business information.
✅ What you should do
Be cautious of unsolicited legal threat emails, especially those requesting urgent action
Verify law firm communications through official channels before responding
Train staff to report suspicious messages, even if they look official
Deploy advanced phishing detection and EDR tools to catch spear-phishing attempts
Monitor for unauthorized credential use and enable multi-factor authentication wherever possible
🔒 Why this matters
Noodlophile uses fear of legal action to manipulate employees into triggering malware. Its ability to harvest sensitive business data makes it especially dangerous for organizations across all sectors. The best defense is a combination of technical safeguards and well-trained employees who know how to spot and handle social engineering attempts.
📚 Cyber Book
Cybercriminal Networks: Origin, growth and criminal capabilities by Rutger Leukfeldt
That concludes today’s briefing . You can check the top headlines here!
Copyright © 2025 CyberMaterial. All Rights Reserved.
Follow CyberMaterial on:
Substack, LinkedIn, Twitter, Reddit, Instagram, Facebook, YouTube, and Medium.