Cyber Briefing: 2025.08.15
Recent cyber incidents reveal an escalating surge of sophisticated attacks targeting both public and private sectors worldwide. From ransomware campaigns in the Middle East and Norway, Croatia.
👉 What's going on in the cyber world today?
Welcome to Cyber Briefing, the newsletter that informs you about the latest cybersecurity advisories, alerts, incidents and news every weekday.
First time seeing this? Please Subscribe
🚨 Cyber Alerts
1. Charon Ransomware Hits Middle East
A new ransomware family, Charon, has been targeting the Middle East's public sector and aviation industry with advanced persistent threat (APT)-style tactics. The malware uses sophisticated techniques like DLL side-loading, EDR evasion, and victim-specific ransom notes to encrypt files and maximize disruption.
2. Hackers Use CrossC2 to Target Linux, macOS
Japan's JPCERT/CC discovered a new attack campaign between September and December 2024 that utilized a cross-platform command-and-control framework called CrossC2 to target systems, including those in Japan. This attack, which shares some overlap with BlackSuit/Black Basta ransomware activity, involved a custom malware loader named ReadNimeLoader that was used to deliver Cobalt Strike Beacon to compromise Linux and macOS systems.
3. Zoom Patches Critical Windows Flaw
Zoom has patched a critical vulnerability (CVE-2025-49457) in its Windows client that an unauthenticated user could exploit to gain elevated privileges through an untrusted search path. This flaw posed a significant risk as it could allow an attacker to gain full control of a user's system and access sensitive data.
For more alerts, click here!
💥 Cyber Incidents
4. Croatian Institute Hit by Ransomware
The Ruđer Bošković Institute (RBI) in Croatia confirmed it was a victim of the global ransomware attack on Thursday, July 31, 2025, which exploited Microsoft SharePoint “ToolShell” vulnerabilities. The institute is refusing to pay the ransom and is instead working to restore its data from backups and rebuild its IT infrastructure.
5. Norway Dam Breached by Pro-Russian Hackers
Pro-Russian hackers seized control of a dam in Bremanger, Norway, in April, opening a floodgate for four hours. Norway's security service, PST, stated that the attack was a demonstrative act of "hybrid warfare" intended to cause fear and showcase their capabilities rather than cause destruction.
6. Hackers Leak Allianz Life Data
In July 2025, insurance giant Allianz Life disclosed a data breach that exposed the personal information of 2.8 million individuals, including customers and business partners. The breach, which was part of a larger campaign targeting Salesforce instances, was carried out by the hacker group ShinyHunters, which subsequently leaked the stolen data.
For more incidents, click here!
📢 Cyber News
7. ShinyHunters, Spider Join Forces
An ongoing data extortion campaign is targeting Salesforce customers, with evidence suggesting that threat groups ShinyHunters and Scattered Spider are collaborating. Their partnership, which shows a shift in tactics from simple data theft to more sophisticated social engineering, may soon set its sights on the financial services and technology sectors.
8. US Updates Sanctions on Garantex
U.S. officials have renewed sanctions against the Russian cryptocurrency exchange Garantex, which is accused of laundering over $100 million for cybercriminals and ransomware gangs since 2019. The sanctions also target Garantex's successor, Grinex, and several associated companies and individuals, in an effort to curb their role in facilitating cybercrime and sanctions evasion.
9. Stolen Police Emails Sold for $40
Active police and government email accounts are being sold on the dark web for as little as $40, providing cybercriminals with a direct and credible way to infiltrate trusted systems. These accounts, which are still in legitimate use by agencies in several countries, allow attackers to impersonate officials, send fraudulent requests, and access sensitive data with a high degree of credibility.
For more news, click here!
📈Cyber Stocks
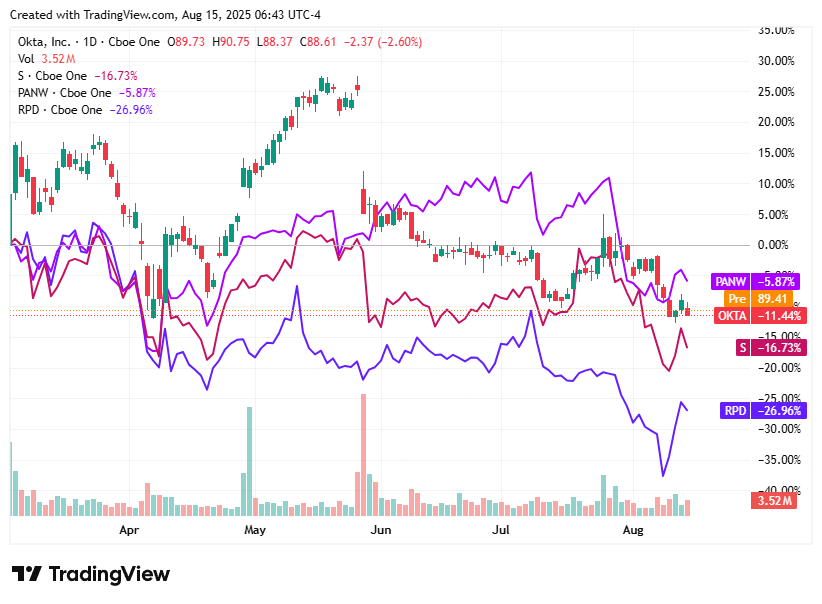
On Friday, August 15, 2025, cybersecurity stocks weakened as markets contended with valuation recalibrations, merger uncertainties, and macroeconomic pressure.
Palo Alto Networks (PANW) slipped 1.83% to $173.55, as the market digested recent strategic moves amid a broader tech pullback and valuation recalibration following optimism around acquisitions.
Rapid7 (RPD) declined 1.78% to $20.94, pulled down by valuation pressure despite strong Q2 earnings results, as markets remained cautious of its elevated cloud commitments and growth trajectory.
Check Point Software Technologies (CHKP) eased 1.57% to $185.32, impacted by continued investor concern over modest billings growth despite steady revenue and earnings.
SentinelOne (S) dropped 3.61% to $16.57, as buyer interest waned amid cooling acquisition speculation and heightened scrutiny around its valuation.
Okta (OKTA) fell 2.64% to $88.61, as sentiment dampened due to concerns over growth sustainability and valuation in a volatile macroeconomic environment.
💡 Cyber Tip
🌐Immediately update your Zoom client to the latest version.
A critical security vulnerability in the Zoom Windows client could allow an attacker to take control of your computer. The flaw, CVE-2025-49457, allows for a privilege escalation attack. Keeping your software up to date is crucial for your personal and professional security.
✅ What you should do
Immediately update your Zoom client to the latest version to patch the critical vulnerability.
For Zoom Workplace for Windows, the patched version is 6.3.10 or later.
Open the Zoom application, click your profile picture, and select "Check for Updates" to install the patch.
Ensure all other Zoom products on Windows, such as Zoom VDI, Rooms, and Meeting SDK, are also updated to the latest secure versions.
Regularly check for and apply security updates for your operating system and all other software.
🔒 Why this matters
This type of vulnerability allows an attacker to elevate their access from a limited user to a system administrator, essentially granting them complete control over your device. Without the patch, your machine is at risk of being compromised, leading to data theft, malware installation, or becoming a part of a larger network attack.
📚 Cyber Book
📚 Cyber Book
Cybersecurity and Financial System Resilience Report by The board of Governors of the Federal Reserve System
That concludes today’s briefing . You can check the top headlines here!
Copyright © 2025 CyberMaterial. All Rights Reserved.
Follow CyberMaterial on:
Substack, LinkedIn, Twitter, Reddit, Instagram, Facebook, YouTube, and Medium.