Cyber Briefing: 2025.08.11
WinRAR zero-day exploited, Lenovo BadUSB flaw, Tesla Google Ads scam, breaches hit Connex CU, Google Ads CRM, UWA; EU NIS2 delays, Scattered Spider leaks on Telegram, MedusaLocker recruits pentesters.
👉 What's going on in the cyber world today?
Welcome to Cyber Briefing, the newsletter that informs you about the latest cybersecurity advisories, alerts, incidents and news every weekday.
First time seeing this? Please Subscribe
🚨 Cyber Alerts
1. WinRAR Zero-Day Actively Exploited
WinRAR has patched a new zero-day vulnerability, CVE-2025-8088, which could allow attackers to execute arbitrary code through specially crafted archive files. This security flaw, along with a related vulnerability, CVE-2025-6218, has been exploited in real-world attacks targeting Russian organizations, with the hacking group Paper Werewolf suspected of being the perpetrator.
2. Lenovo Linux Webcam BadUSB Flaw
Researchers found vulnerabilities in some Lenovo webcams that could turn them into BadUSB attack devices. These flaws, named BadCam, could let attackers remotely inject keystrokes and compromise a computer, marking a new type of threat from already-connected USB peripherals.
3. Tesla-Themed Malware in Google Ads
A sophisticated malware operation is using fake Google Ads to deceive consumers into placing fraudulent preorders for Tesla's Optimus robot, exploiting the company's past deposit models to siphon money. These malicious sites, disguised as official Tesla pages, collect credit card information without processing payments, delaying detection and prioritizing data theft over immediate financial charges.
For more alerts, click here!
💥 Cyber Incidents
4. Connex Credit Union Data Breach
Connex Credit Union, a large credit union in Connecticut, announced that a data breach in early June compromised the personal and financial information of tens of thousands of its members. The stolen data includes names, account numbers, and Social Security numbers, among other sensitive details.
5. Google Ads Customers' Data Breach
Google has confirmed a data breach affecting a limited set of its Salesforce CRM data, which contained the information of potential Google Ads customers. The breach, attributed to the threat group ShinyHunters, exposed business names, phone numbers, and notes, but no payment or Google Ads account data was compromised.
6. University of WA Major Data Breach
In a recent data breach, the University of Western Australia (UWA) confirmed that unauthorized access exposed the password information of thousands of its staff and students. The university has since locked all accounts, initiated a full investigation, and urged everyone to reset their passwords.
For more incidents, click here!
📢 Cyber News
7. 8 Nations Miss EU NIS2 Deadline
The European Commission is taking action against several member states for failing to incorporate the NIS2 directive into their national laws by the October 17, 2024 deadline. This delay affects countries like Ireland, Spain, France, and others, potentially leading to further legal proceedings at the Court of Justice of the European Union (CJEU). The directive, aimed at bolstering cybersecurity across the bloc, requires member states to transpose it into domestic legislation, a process that differs from regulations like the GDPR which automatically become law.
8. Scattered Spider Lists Attacks on Telegram
A new Telegram channel has emerged, created by a group conflating three well-known cybercriminal gangs: Shiny Hunters, Scattered Spider, and Lapsus$. In less than 24 hours, the channel, described by observers as "chaotic" and "insane," has been used to leak numerous legal documents and data from major companies and government entities, as well as to sell data, make threats, and promote a new ransomware.
9. MedusaLocker Seeks Pentesters
The MedusaLocker ransomware gang is actively seeking new penetration testers to join their operation, as announced on their dark web leak site. This recruitment effort highlights a growing trend in cybercrime where ransomware groups are adopting business-like structures and hiring skilled professionals to enhance their attacks and profitability.
For more news, click here!
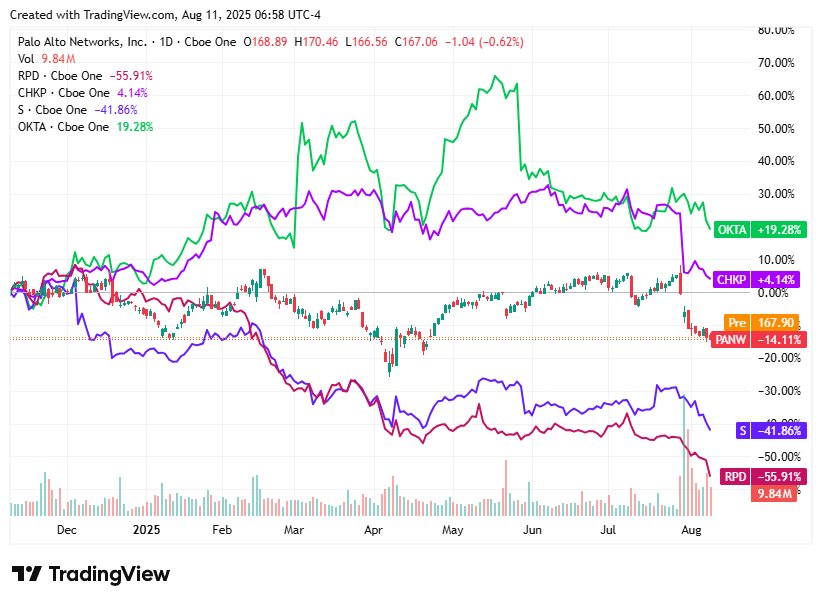
📈Cyber Stocks
Here’s how cybersecurity stocks moved on Monday, August 11, 2025, amidst continued macroeconomic caution, valuation pressures, and speculations around strategic developments.
Palo Alto Networks (PANW) slipped 0.64% to $167.06, as investors digested concerns over its $25 billion CyberArk acquisition diluting EPS and fueling uncertainty despite long-term strategic upside
Rapid7 (RPD) plunged 9.84% to $17.875, pressured by analyst downgrades, including a target cut by RBC, and mounting valuation concerns despite solid Q2 earnings and cash flow metrics
Check Point Software Technologies (CHKP) eased 0.88% to $183.32, as executives signaled more cautious cybersecurity spending plans amid economic uncertainty, dampening investor enthusiasm
SentinelOne (S) declined 3.84% to $16.03, as profit-taking intensified following earlier M&A-driven gains and continued skepticism over its high valuation
Okta (OKTA) fell 2.16% to $91.55, weighed down by concerns over its ability to sustain growth and justify its premium valuation in a volatile macro environment
💡 Cyber Tip
📦 Update WinRAR Now to Patch Zero-Day Exploited in Active Attacks
A critical WinRAR zero-day vulnerability (CVE-2025-8088) is being actively exploited to deliver malicious files and execute code on Windows systems. The flaw, along with a related bug (CVE-2025-6218), has been used in targeted phishing attacks, reportedly by the hacking group Paper Werewolf, against Russian organizations. WinRAR version 7.13 contains the fix.
✅ What you should do:
Update WinRAR immediately to version 7.13 or later from the official WinRAR website
Delete any suspicious archive files received via email or from untrusted sources
Use email security tools to scan attachments before opening
Enable endpoint protection that can detect malicious archive payloads
Consider disabling automatic extraction in archiving tools
🔒 Why this matters:
These vulnerabilities allow attackers to plant files in sensitive system directories and execute malicious code without detection. Rapid patching is essential to block ongoing exploitation.
📚 Cyber Book
IT Disaster Recovery Planning For Dummies - by Peter H. Gregory
That concludes today’s briefing . You can check the top headlines here!
Copyright © 2025 CyberMaterial. All Rights Reserved.
Follow CyberMaterial on:
Substack, LinkedIn, Twitter, Reddit, Instagram, Facebook, YouTube, and Medium.