Cyber Briefing: 2025.08.04
Akira exploits SonicWall VPNs, PlayPraetor infects Androids, fake OAuth apps hit Microsoft 365, Luxembourg probes Huawei outage, Aeroflot data leaked, DermCare breach, Flo settles lawsuit
👉 What are the latest cybersecurity alerts, incidents, and news?
Welcome to Cyber Briefing, the newsletter that informs you about the latest cybersecurity advisories, alerts, incidents and news every weekday.
First time seeing this? Please Subscribe
🚨 Cyber Alerts
1. Akira Hits SonicWall VPNs in Zero‑Day
The Akira ransomware group is actively targeting SonicWall SSL VPN devices in a new attack wave, with researchers suspecting the use of a zero-day vulnerability. Organizations are being advised to disable the affected VPN service and enforce multi-factor authentication as immediate mitigation steps.
2. PlayPraetor Trojan Android Devices
A new Android remote access trojan (RAT) named PlayPraetor has infected over 11,000 devices by abusing accessibility services for remote control and data theft. Distributed through fake Google Play Store pages promoted via ads and SMS, the malware uses overlay screens to steal credentials from nearly 200 banking and crypto apps.
3. Fake OAuth Apps Breach Microsoft 365
Cybersecurity researchers have identified a phishing campaign where attackers use fake Microsoft OAuth applications impersonating legitimate companies to facilitate account takeovers. This multi-stage attack tricks users into interacting with a consent screen before redirecting them to an Adversary-in-the-Middle phishing site designed to steal credentials and bypass multi-factor authentication.
For more alerts, click here!
💥 Cyber Incidents
4. Luxembourg Probes Huawei Tech Outage
A nationwide telecommunications outage in Luxembourg, caused by a sophisticated cyberattack reportedly targeting Huawei equipment, is now under formal government investigation. The incident, which blocked access to mobile networks and emergency services, has triggered a national resilience review and consideration of new regulations for network failures.
5. Hackers Leak Alleged Aeroflot Data
Following a major cyberattack that grounded numerous flights, hackers have leaked the alleged flight records of Aeroflot's CEO, Sergei Aleksandrovsky. Despite this, Russia's internet watchdog, Roskomnadzor, officially denies that any data breach occurred at the state-owned airline.
6. Dermatology Clinics Hit by Data Breach
A third-party data breach at DermCare Management, a business services provider, has exposed the sensitive personal and medical information of patients at numerous dermatology clinics. The full scope of the attack, first detected in February 2025, is still under investigation, but it is known to have compromised highly sensitive data from at least ten practices.
For more incidents, click here!
📢 Cyber News
7. EU Plans Biometric Checks for Visitors
Beginning October 12, travelers from outside the European Union will be required to provide fingerprint and facial scans to enter 29 European nations under the new Entry/Exit System (EES). This biometric data will replace manual passport stamping to streamline border crossings, will be stored for at least three years, and refusal to comply will result in being denied entry.
8. Flo Settles Data‑Sharing Lawsuit
The period tracking app Flo has settled a class-action lawsuit alleging it improperly shared sensitive user data with companies like Meta. This last-minute agreement leaves Meta as the sole defendant to face a potential multi-billion dollar verdict from a class of 38 million women as the trial nears its conclusion.
9. Russia Mobile Internet Shutdowns Spike
Russia implemented a record number of mobile internet shutdowns in July, officially citing security threats from Ukrainian drones as the cause. These blackouts are part of a wider digital crackdown, causing severe economic and social disruption, with rights groups arguing the drone threat is a pretext to control information and suppress free speech.
For more news, click here!
📈Cyber Stocks
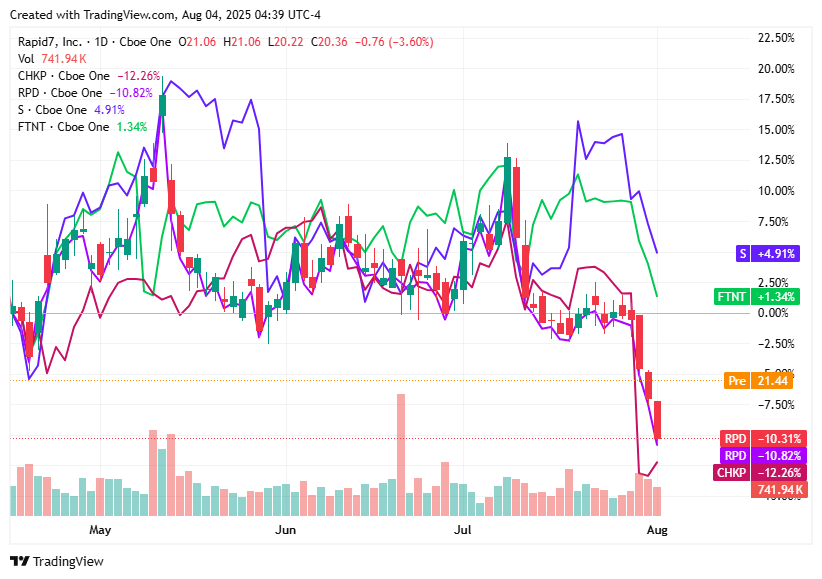
On Monday, August 4, 2025, cybersecurity stocks declined broadly as the market digested weak economic data, fresh tariff developments, and renewed pressure on high-multiple tech names.
Zscaler (ZS) slid 1.79% to $280.27, as caution around richly valued cloud-security stocks contributed to profit-taking despite strong ThreatLabz metrics and growth expectations.
Rapid7 (RPD) dropped 3.55% to $20.36, weighed down by valuation concerns as investors braced for earnings on August 7, leaving sentiment cautious ahead of the release.
Check Point Software Technologies (CHKP) rose 1.41% to $188.58, reflecting a rebound following last week’s Q2 earnings shock that drove sharp multiple compression, as optimism returned over long-term billings growth.
SentinelOne (S) declined 2.29% to $17.94, lamenting lingering uncertainty around acquisition speculation and ongoing concerns over its elevated valuation profile
Fortinet (FTNT) fell 2.55% to $97.36, pressured by broad rotation away from cybersecurity hardware names even as analysts reaffirmed bullish guidance and strong operating margins.
💡 Cyber Tip
Block Fake OAuth Apps Targeting Microsoft 365 Accounts
Cybercriminals are using fake Microsoft OAuth applications to impersonate trusted brands like DocuSign and SharePoint, tricking users into granting access to malicious apps. Once access is attempted, users are funneled through a Tycoon phishing kit and an Adversary-in-the-Middle (AitM) attack that captures login credentials, MFA tokens, and session cookies. This allows attackers to fully compromise Microsoft 365 accounts.
✅ What you should do:
Review and restrict third-party app permissions in Microsoft 365 admin settings
Enable admin consent workflows for all OAuth app integrations
Educate employees on suspicious consent screens and verify app legitimacy before approval
Monitor logs for unexpected OAuth grant activity and unusual login behavior
Implement continuous session monitoring and secure MFA enforcement with phishing-resistant methods
🔒 Why this matters:
This campaign has already targeted thousands of Microsoft 365 users by abusing trusted login flows. The combination of OAuth misuse and AitM phishing makes it highly evasive. Preventing unauthorized app access and monitoring token-based authentication flows are key to defense.
📚 Cyber Book
Online Dating (2017) by Mila Lewis
That concludes today’s briefing . You can check the top headlines here!
Copyright © 2025 CyberMaterial. All Rights Reserved.
Follow CyberMaterial on:
Substack, LinkedIn, Twitter, Reddit, Instagram, Facebook, YouTube, and Medium.