Cyber Briefing: 2025.07.18
Cybercriminals are leveraging new tactics and platforms, from GitHub repos to Microsoft Teams and npm packages, to spread sophisticated malware, launder crypto and disrupt critical services. This edit
👉 What's the latest in the cyber world today?
Welcome to Cyber Briefing, the newsletter that informs you about the latest cybersecurity advisories, alerts, incidents and news every weekday.
First time seeing this? Please Subscribe
🚨 Cyber Alerts
1. Hackers Host Amadey Malware via GitHub Repos
Threat actors are actively exploiting public GitHub repositories to host and distribute malicious payloads, particularly through the Amadey malware, as part of a sophisticated malware-as-a-service (MaaS) operation. These campaigns, which often leverage malware loaders like Emmenhtal, aim to bypass traditional security measures and deliver information stealers or other secondary payloads.
2. Matanbuchus Malware Spread via Teams Voice Calls
The Matanbuchus malware loader is currently being distributed through social engineering tactics via Microsoft Teams calls, with attackers impersonating IT helpdesks. This malware-as-a-service operation, first advertised in early 2021, has evolved significantly, demonstrating enhanced evasion and obfuscation techniques.
3. Malicious npm Packages Deliver Protestware
A sophisticated protestware campaign is targeting Russian-language users via compromised npm packages, weaponizing nearly 2,000 versions of malicious code to disrupt interactions on Russian and Belarusian websites. This attack marks a significant escalation in supply chain attacks, distributing politically motivated malware through JavaScript package repositories.
For more alerts, click here!
💥 Cyber Incidents
4. Co-op Data Stolen of 6.5M Members
UK retailer Co-op confirmed that a cyberattack in April resulted in the theft of personal contact information for all 6.5 million of its members, though no financial data was compromised. The attack, attributed to a group linked with Scattered Spider and DragonForce ransomware, caused system shutdowns and food shortages.
5.Stormous Hits North Country Health, Claims 600K Records
The Stormous ransomware group claims to have stolen sensitive personal and health data belonging to 600,000 patients from North Country HealthCare, a nonprofit health provider in northern Arizona. The group initially planned to sell 100,000 records and release the remaining 500,000 for free, and has since published the files.
6. BigONE Crypto Exchange Hit, Loses $27M in Attack
Crypto exchange BigONE suffered a third-party supply chain attack on its hot wallet infrastructure, resulting in an estimated $27 million loss across various cryptocurrencies. BigONE has pledged to fully cover all user losses using its internal security reserves and by securing external liquidity.
For more incidents, click here!
📢 Cyber News
7. BADBOX 2.0 Infects 10M Devices And Google Sues
Google has filed a lawsuit against 25 unnamed cybercriminals, believed to be based in China, for operating the BADBOX 2.0 botnet, which has compromised over 10 million uncertified Android devices globally, causing significant harm to Google's reputation and expending substantial resources. This legal action aims to dismantle the criminal enterprise responsible for pre-installing malware and tricking users into downloading malicious applications, which are then used for various fraudulent and criminal activities.
8. Cross-Chain Crypto Laundering Tops $21.8 Billion
A new report reveals a significant surge in crypto criminals using cross-chain methods to obscure illicit transactions, with the estimated value of such activity exceeding $21.8 billion. This sophisticated tactic involves moving funds across multiple blockchains, decentralized exchanges, and coin swap services to evade detection, complicating investigations into a range of crimes from hacks to scams.
9. Train Brakes Hackable via Radio Known for 20 Years
A disclosed vulnerability (CVE-2025-1727) in the unencrypted remote linking protocol of train End-of-Train and Head-of-Train systems allows hackers to remotely send brake commands. This critical flaw, affecting both freight and passenger trains, could cause sudden stops, derailments, or even shut down national rail systems, a risk that researchers have tried to bring to light for over a decade.
For more news, click here!
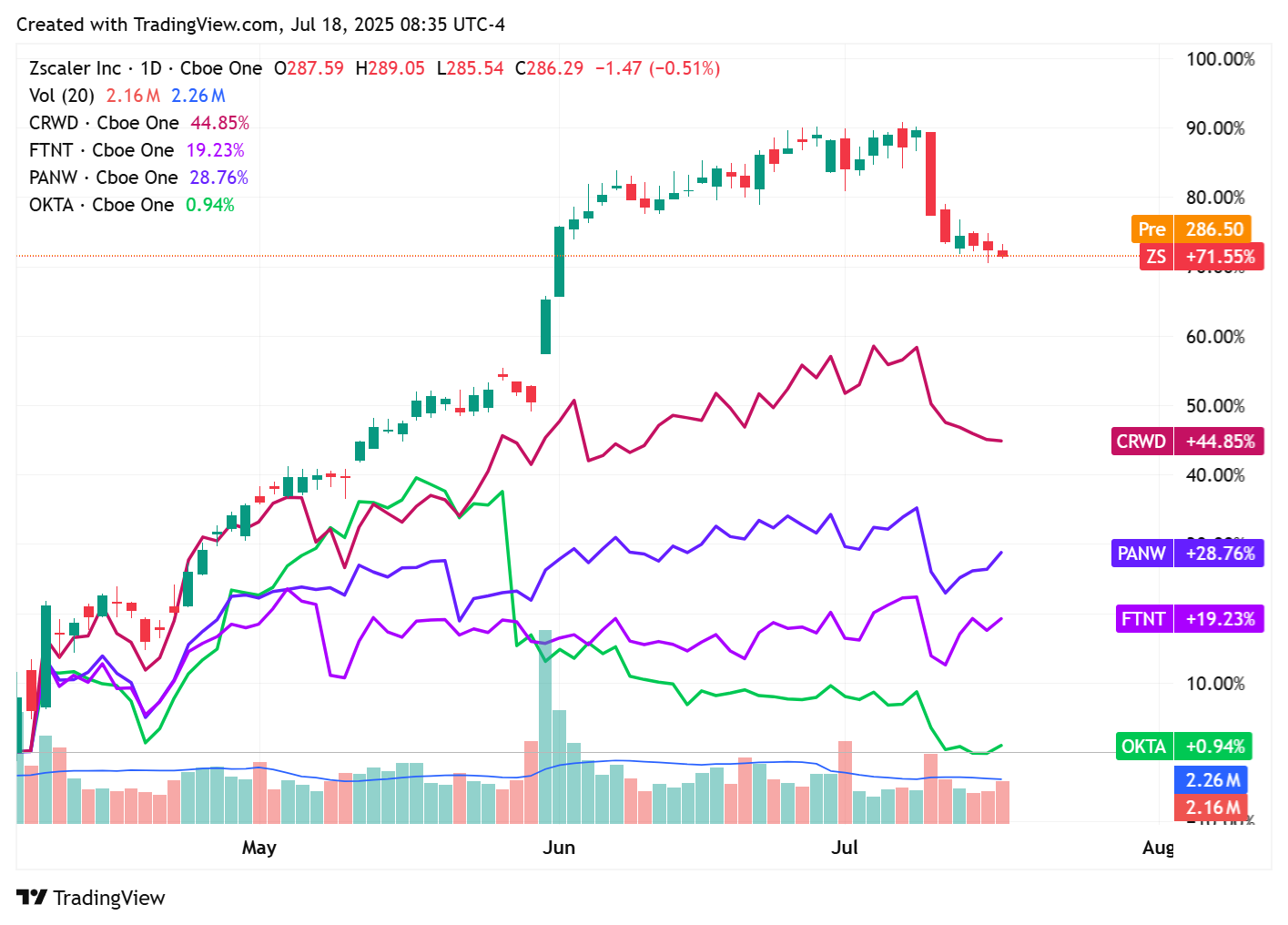
📈Cyber Stocks
On Thursday, July 17, 2025, cybersecurity market closed facing mixed performance as investor sentiment turned cautious amid newly announced tariffs, sector-wide profit-taking, and valuation concerns after a months-long rally.
Zscaler (ZS) rose 38.28%, outperforming peers amid renewed investor enthusiasm for zero-trust architectures and strong growth in subscription revenues, driven by robust enterprise adoption of cloud-native security solutions.
CrowdStrike (CRWD) gained 26.47%, benefiting from continued strength in endpoint security demand and investor confidence following recent upbeat earnings and rising demand for threat intelligence services.
Palo Alto Networks (PANW) advanced 13.34%, supported by optimism surrounding its AI-driven threat detection tools and steady momentum in its consolidated security platform offerings.
Fortinet (FTNT) edged up 6.97%, helped by stable demand in SMB markets and interest in its appliance-based solutions, though growth remains moderate compared to more cloud-focused peers.
Okta (OKTA) fell 12.60%, under pressure from slowing billings growth and concerns over identity platform competition, with momentum stalling after early-year gains.
💡 Cyber Tip
Watch Out for Fake IT Support Calls on Microsoft Teams Delivering Matanbuchus Malware
Attackers are exploiting Microsoft Teams voice calls by impersonating IT helpdesk staff to trick users into launching remote support tools like Quick Assist. Once remote access is granted, they instruct victims to run malicious PowerShell scripts that install the Matanbuchus malware loader. This sophisticated malware uses advanced evasion techniques to avoid detection and can execute harmful payloads on your device.
✅ What you should do:
Always verify the identity of anyone claiming to be IT support before granting remote access, preferably by contacting them through an official channel outside Teams.
Never launch Quick Assist or run scripts from unsolicited or unexpected Teams calls.
Be cautious if asked to execute commands or scripts remotely; confirm legitimacy first.
Report suspicious Teams calls or unusual IT requests to your internal security team immediately.
🔒 Why this matters:
Matanbuchus 3.0 is designed to bypass many security tools, making it hard to detect once inside your system. Falling for this social engineering tactic can give attackers full control of your device, risking data theft, system damage, and broader network compromise. Vigilance and strict verification can stop the attack before it starts.
📚 Cyber Review
Join us for a compelling edition of Cyber Review featuring Matthew Webster, renowned cybersecurity expert and author of the eye-opening book Do No Harm: Protecting Connected Medical Devices, Healthcare, and Data from Hackers and Adversarial Nation States. In this timely conversation, Webster is joined by healthcare and security professionals to discuss the critical vulnerabilities in modern medical technologies and the growing threat posed by adversarial nation-state actors.
From pacemakers and insulin pumps to hospital IT networks and health apps, we explore the intersection of digital innovation and patient safety. Webster shares what inspired him to write Do No Harm, alarming real-world scenarios he's encountered, and actionable strategies for building resilience in healthcare environments. This session offers valuable takeaways for cybersecurity practitioners, healthcare executives, policymakers, and everyday users of connected health devices.
Tune in to understand how we can better protect human lives in a world where healthcare is increasingly digital. Don’t miss exclusive resources, expert insights, and practical tools.
Be sure to like, comment, and subscribe for more thought-provoking episodes of Cyber Review.
That concludes today’s briefing . You can check the top headlines here!
Copyright © 2025 CyberMaterial. All Rights Reserved.
Follow CyberMaterial on:
Substack, LinkedIn, Twitter, Reddit, Instagram, Facebook, YouTube, and Medium.








