Cyber Briefing: 2025.07.16
Google patches Chrome Zero-day CVE; Interlock spreads new PHP RAT; Konfety Android malware evolves; major breaches hit Episource, Albemarle, Fitify; US Guard hacked by Salt Typhoon.
👉 What's the latest in the cyber world today?
Welcome to Cyber Briefing, the newsletter that informs you about the latest cybersecurity advisories, alerts, incidents and news every weekday.
First time seeing this? Please Subscribe
🚨 Cyber Alerts
1. Google Realeases Critical Chrome Update
Google has released an urgent Chrome update patching six security flaws, including one, CVE-2025-6558, actively exploited in the wild. This critical vulnerability, involving an incorrect validation of untrusted input in ANGLE and GPU components, could allow attackers to escape the browser's sandbox through a crafted HTML page.
2. Interlock deploys new PHP RAT via FileFix
The Interlock ransomware group is now deploying a new PHP-based Remote Access Trojan (RAT) via a sophisticated delivery method called FileFix, a variant of ClickFix, in a widespread campaign targeting various industries. This marks a significant evolution in their tactics, moving from previous JavaScript-based RATs to a more evasive PHP version, spread through compromised websites and deceptive CAPTCHA prompts that trick users into executing malicious PowerShell scripts.
3. Android Malware Konfety evolves
A sophisticated new Konfety Android malware variant is actively evading detection by employing malformed ZIP structures and advanced obfuscation techniques. This latest iteration disguises itself as legitimate applications, yet delivers no real functionality, serving instead as a stealthy platform for malicious activities like ad fraud and unauthorized installations.
For more alerts, click here!
💥 Cyber Incidents
4. Albemarle County Ransomware Attack
Albemarle County, Virginia, recently experienced a sophisticated ransomware attack that compromised the personal information of residents, county employees, and public school staff. This significant cybersecurity breach led to federal law enforcement involvement and the implementation of enhanced security measures.
5. Millions Affected By Episource Data Breach
Over five million patients had their sensitive medical and personal information exposed in a major data breach at Episource, a subsidiary of UnitedHealth Group's Optum. The breach, discovered in February 2025, potentially compromised data ranging from Social Security numbers to health insurance details and diagnosis records, raising significant privacy and security concerns for affected individuals.
6. Fitify Leaks 138K User Progress Photos
A publicly accessible Google cloud storage bucket belonging to the popular fitness app Fitify was discovered by Cybernews, exposing hundreds of thousands of user files, including 138,000 sensitive progress photos often showing users in minimal clothing. The vulnerability, which allowed access without passwords or security keys, was promptly closed after Cybernews notified the company, but highlighted significant lapses in data security and privacy for Fitify users.
For more incidents, click here!
📢 Cyber News
7. China's Salt Typhoon Hacked US Guard
Chinese state-sponsored hackers, identified as "Salt Typhoon," extensively compromised a US Army National Guard unit's network between March and December 2024, exfiltrating critical configuration information and communication data. This breach poses a significant threat to US critical infrastructure as the stolen data could facilitate further attacks on other National Guard units and state-level cybersecurity partners.
8. Police Disrupt Diskstation Gang
An international law enforcement operation, "Operation Elicius," successfully dismantled the Romanian "Diskstation" ransomware gang, which had been encrypting Synology NAS devices globally since 2021 and paralyzing businesses, including several in Italy's Lombardy region. The investigation, led by Milanese prosecutors, resulted in arrests and the seizure of critical evidence, significantly disrupting the group's operations.
9. Abacus Dark Web Market Exit Scam
Abacus Market, once the largest Western darknet marketplace facilitating Bitcoin and Monero transactions for illicit drugs and other goods, has reportedly ceased operations. This abrupt shutdown is largely suspected to be an "exit scam," a common tactic where marketplace operators disappear with user funds held in escrow. Blockchain intelligence firm TRM Labs indicates that the sudden closure, coupled with previous withdrawal delays, aligns with typical exit scam patterns, although a covert law enforcement takedown remains a less likely, but not impossible, scenario.
For more news, click here!
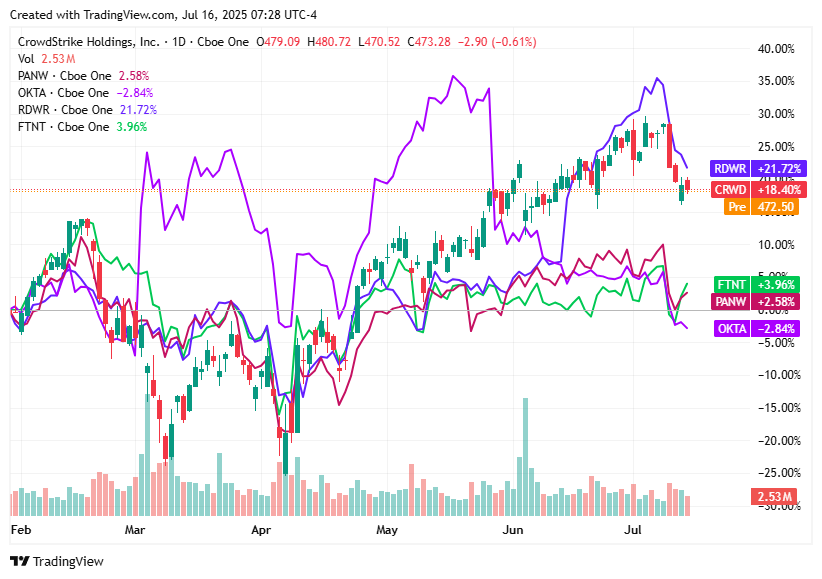
📈Cyber Stocks
Following a shift in market sentiment toward AI optimism and away from tariff-related concerns, cybersecurity stocks showed varied performance on July 16, 2025.
CrowdStrike (CRWD) declined 0.69% to $473.28, as profit-taking set in after a strong year-to-date rally and ongoing concerns about its elevated valuation.
Palo Alto Networks (PANW) rose 0.75% to $192.25, supported by growing optimism over increasing AI-driven cybersecurity demand and the strength of its integrated security platform.
Okta (OKTA) slipped 0.97% to $91.10, as investors rotated into higher-momentum tech stocks following Nvidia-led gains and adjustments triggered by softer consumer inflation data.
Radware (RDWR) dropped 1.65% to $27.68, pressured by broader sector weakness amid overall market volatility and the absence of specific company news.
Fortinet (FTNT) climbed 1.91% to $104.93, boosted by a strong Relative Strength Rating and continued earnings momentum in its Unified SASE offerings, signaling a technical breakout.
💡 Cyber Tip
Update Chrome Now to Stay Protected from Actively Exploited Vulnerability
Google has released an urgent security update for Chrome to fix a serious vulnerability that is currently being exploited. This flaw allows attackers to bypass browser security simply by luring users to a malicious webpage. Once exploited, it can give attackers access to your device without any further action on your part.
✅ What you should do:
Open Chrome and check for updates by going to More > Help > About Google Chrome, then restart the browser.
Avoid visiting unfamiliar or suspicious websites until you’ve applied the update.
Update any other Chromium-based browsers you use, such as Microsoft Edge, Brave, or Opera.
Use your system’s built-in security settings to add an extra layer of protection.
Stay alert for unusual browser behavior that could signal infection.
🔒 Why this matters:
This vulnerability is already being used in real-world attacks. Without the latest update, just visiting a malicious website could silently compromise your system. Updating now is a simple but crucial step to stay secure.
📚 Cyber Book
Cyber Insurance - The Cyber Insurance Survival Guide by Joey Hernandez
That concludes today’s briefing . You can check the top headlines here!
Copyright © 2025 CyberMaterial. All Rights Reserved.
Follow CyberMaterial on:
Substack, LinkedIn, Twitter, Reddit, Instagram, Facebook, YouTube, and Medium.