Cyber Briefing: 2025.07.14
WinRAR zero-day sold for $80K, Gemini prompt injection flaw exploited, Wing FTP RCE active, DC law firm hacked, supermarket breach, Grok-4 jailbreak, Huawei deal, and CBI tech scam bust.
👉 What's trending in cybersecurity today?
Welcome to Cyber Briefing, the newsletter that informs you about the latest cybersecurity advisories, alerts, incidents and news every weekday.
First time seeing this? Please Subscribe
🚨 Cyber Alerts
1. WinRAR Zero-Day Exploit $80K on Dark Web
A new, highly dangerous zero-day exploit for WinRAR, enabling remote code execution, has been put up for sale on a dark web forum for $80,000. This previously unknown vulnerability affects various WinRAR versions, posing a significant risk to millions of users even if they've patched against other recent flaws.
2. Google Gemini Flaw Hijacks Email Summaries
Google Gemini for Workspace can be exploited through hidden, invisible instructions within emails, prompting it to generate seemingly legitimate but malicious summaries that direct users to phishing sites. This "indirect prompt injection" bypasses traditional security measures as it relies on Gemini's interpretation of the email content rather than direct links or attachments.
3. Wing FTP Server RCE Flaw Exploited
Hackers are actively exploiting a critical remote code execution vulnerability (CVE-2025-47812) in Wing FTP Server, just a day after technical details became public. This flaw, which allows unauthenticated attackers to execute code with the highest privileges, is being used for reconnaissance, persistence, and data exfiltration.
For more alerts, click here!
💥 Cyber Incidents
4. China Hackers Suspected in DC Law Firm Breach
A powerful Washington, DC law firm, Wiley Rein, suspects Chinese government-affiliated hackers breached attorney email accounts for intelligence gathering, likely seeking information related to the US-China trade war, Taiwan, and US government agencies. This incident follows a pattern of suspected Chinese cyber intrusions targeting sensitive US trade and investment data.
5. nius.de cyberattack leaks user data
A cyberattack on nius.de manipulated article titles and apparently published a database containing subscriber information like names, emails, and payment details. The breach, which also involved website defacement, potentially exploited unauthenticated access to the CMS and customer database, with the authenticity of the leaked data and the attackers' identity still unconfirmed.
6.Supermarket cyberattack prompts warning
A recent cybersecurity incident affecting New World Clubcard accounts has prompted an urgent warning for supermarket customers to change their passwords. This comes after scammers attempted to access accounts using commonly known passwords, leading to unauthorized access for some users with weaker or reused credentials.
For more incidents, click here!
📢 Cyber News
7. Spain Awards €12.3M Huawei Contracts
Spain has awarded €12.3 million in contracts to Huawei for managing and storing sensitive wiretap data, igniting concerns among security officials and international observers about potential Chinese government access to classified information due to Huawei's ties to Beijing. This decision stands in stark contrast to the cautionary approach taken by the US and many other EU nations regarding Huawei's involvement in critical infrastructure.
8. CBI Busts £390K UK Tech Scam
India's CBI successfully dismantled a sophisticated transnational tech support scam syndicate, "Operation Chakra V," that targeted victims in the UK and Australia, leading to over £390,000 in losses in the UK alone. The operation, a collaborative effort with international agencies, resulted in arrests and the shutdown of a fraudulent call center in Noida.
9. Grok-4 Jailbroken Via Exploit
Security researchers have demonstrated a powerful jailbreak attack against Grok-4, X’s AI language model, by combining the Echo Chamber and Crescendo techniques to bypass its safety measures. This combined method highlights a critical vulnerability in large language models, exposing the need for more advanced defenses against multi-turn, context-driven adversarial prompts.
For more news, click here!
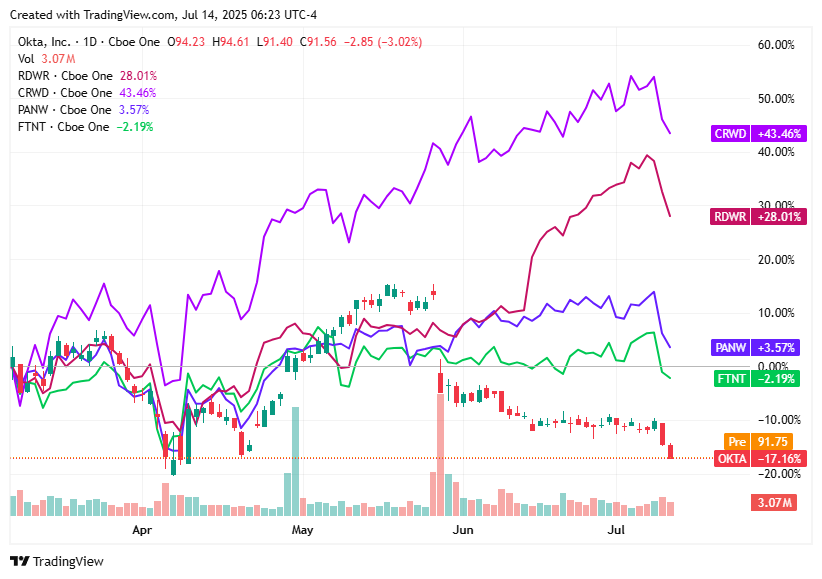
📈Cyber Stocks
Cybersecurity stocks faced broad declines on July 14, 2025, as investor sentiment soured due to fresh tariff announcements, profit-taking, and ongoing concerns over elevated valuations.
Okta (OKTA) dropped 3.04% to $91.56, as software stocks sold off sharply following the announcement of new 30% tariffs on imports from the EU and Mexico.
Radware (RDWR) declined 3.48% to $28.29, caught in a broader sector-wide pullback and facing muted momentum ahead of its upcoming Q2 earnings release.
CrowdStrike (CRWD) fell 1.80% to $478.45, pressured by a rotation out of high-growth tech stocks amid ongoing trade-related valuation concerns.
Palo Alto Networks (PANW) slid 2.43% to $187.39, as investors took profits following a strong AI-driven rally and reacted to trade policy uncertainty.
Fortinet (FTNT) eased 1.12% to $99.06, impacted by general cybersecurity market weakness despite continued strength in its operational technology and network security offerings.
💡 Cyber Tip
Gemini Summaries Hijacked by Hidden Phishing Prompts
A vulnerability in Google Gemini for Workspace allows attackers to embed hidden instructions in emails that manipulate Gemini’s summaries. By using invisible text, attackers can trick Gemini into generating fake alerts, such as password reset warnings or support phone numbers, without including traditional phishing indicators. Since the summaries appear to come from a trusted AI tool, users are more likely to believe them and follow the malicious instructions.
✅ What you should do:
Treat AI-generated summaries in emails as helpful but not authoritative, verify critical alerts manually.
Do not call phone numbers or click links from summaries without confirming their legitimacy.
Use email security tools that flag hidden HTML/CSS content in email bodies.
Disable or limit automatic AI-generated summaries in high-risk environments.
Stay informed about prompt injection and emerging AI-related threats in productivity tools.
🔒 Why this matters:
This attack bypasses traditional email filters by embedding invisible prompts that only affect the AI assistant. It highlights a growing trend where threat actors target not just users, but the AI tools they rely on. Awareness and verification are key to preventing AI-driven phishing deception.
📚 Cyber Book
The Code Book by Simon Singh
That concludes today’s briefing . You can check the top headlines here!
Copyright © 2025 CyberMaterial. All Rights Reserved.
Follow CyberMaterial on:
Substack, LinkedIn, Twitter, Reddit, Instagram, Facebook, YouTube, and Medium.