Cyber Briefing: 2025.07.08
AMOS gets persistent Mac backdoor, NordDragonScan steals Windows data, BERT ransomware kills ESXi VMs, Louis Vuitton and Semco breached, AT&T settles for $177M, Parrot OS 6.4 adds hacking tools.
👉 What's trending in cybersecurity today?
Welcome to Cyber Briefing, the newsletter that informs you about the latest cybersecurity advisories, alerts, incidents and news every weekday.
First time seeing this? Please Subscribe
🚨 Cyber Alerts
1. AMOS Mac Stealer Adds Persistent Backdoor
The Atomic macOS Stealer malware, also known as AMOS, has been upgraded with an embedded backdoor for persistent access to infected systems. This transforms the malware from a simple data stealer into a tool for long-term surveillance and remote command execution. The malware is distributed through cracked software sites and spear-phishing campaigns that often mimic job interviews to steal passwords. This evolution demonstrates the increasing sophistication of threats targeting macOS users and has already affected over 120 countries.
2. NordDragonScan Malware Steals Windows Data
Security researchers have discovered a new infostealer called NordDragonScan that targets Microsoft Windows systems. The attack uses a complex chain starting with a malicious LNK shortcut file that runs a weaponized HTA script. The malware establishes persistence and then steals system information, files with specific extensions, and entire browser profiles. It uses advanced string obfuscation to evade static analysis and exfiltrates the stolen data to a remote command-and-control server.
3. New Ransomware BERT Targets ESXi Systems
A new ransomware group known as BERT is targeting virtualized environments with a particularly disruptive new tactic. Its Linux variant can detect and forcibly shut down ESXi virtual machines before it begins encrypting any files. This approach directly undermines disaster recovery efforts by preventing administrators from migrating or backing up live systems during an attack. The cross-platform malware has variants for Windows and ESXi and shows code similarities to the REvil ransomware family.
For more alerts, click here!
💥 Cyber Incidents
4. Louis Vuitton Korea Hit By Cyberattack
The South Korean unit of luxury brand Louis Vuitton has confirmed it suffered a cyberattack that leaked some customer data. While customer information like contact details was compromised, the company stated that no financial data was exposed. The company has since contained the breach, notified the relevant authorities, and is working with experts to strengthen its security. This is the second LVMH brand to be targeted in recent months after Christian Dior Couture disclosed a similar data breach in May.
5. French Chip Firm Semco Hacked During IPO
The French semiconductor company Semco Technologies suffered a cyberattack from the Qilin ransomware gang during its initial public offering. The Russian-speaking hackers stole sensitive employee data, including passports and invoices, which they later leaked on the dark web. Semco Technologies confirmed the attack but stated that it had contained the incident and that its core operations were not impacted. The timing of the attack during the company's IPO was likely a deliberate tactic to maximize pressure on the firm.
6. Virginia School District Hit By Cyberattack
Prince George County Public Schools in Virginia has announced it identified a cybersecurity incident over the Independence Day holiday weekend. Upon discovery, the district took immediate action to contain the issue and engaged external cybersecurity professionals for assistance. While critical safety systems like building access and phones remain operational, some internal systems, including the email server, have been taken offline. The attack occurred during the summer break, minimizing disruption to classroom learning as the district investigates with law enforcement.
For more incidents, click here!
📢 Cyber News
7. AT&T Agrees to $177M Breach Settlement
Telecom giant AT&T has agreed to a $177 million settlement to resolve class-action lawsuits from two separate data breaches. The first breach, starting in 2019, exposed the personal data and Social Security numbers of about 73 million customers. A second incident, confirmed in 2024, involved a hacker accessing the call records of nearly all 109 million U.S. customers. While denying responsibility, AT&T will establish a fund for customer claims, with notifications expected to be sent starting in August 2025.
8. Alleged Hafnium Hacker Arrested in Italy
A Chinese national named Xu Zewei has been arrested in Milan, Italy, based on an international warrant from the United States. Xu is allegedly linked to the Chinese state-sponsored hacking group Silk Typhoon, also known as Hafnium. He is specifically accused of being part of a 2020 campaign that targeted and stole data related to COVID-19 vaccine research. Xu is now being held in an Italian prison as the United States government seeks his extradition to face trial.
9. Parrot OS 6.4 Adds New Hacking Tools
The Parrot Security team has released Parrot Security OS 6.4, the final major update in the 6.x series of the ethical hacking distribution. This version includes an upgraded Linux kernel, adds many new hacking tools, and introduces official support for Microsoft PowerShell. This release refines the current Debian 12-based system and sets the stage for the next generation of the platform. The development team is now actively working on Parrot 7, which will be based on Debian 13 and support new architectures.
For more news, click here!
📈Cyber Stocks
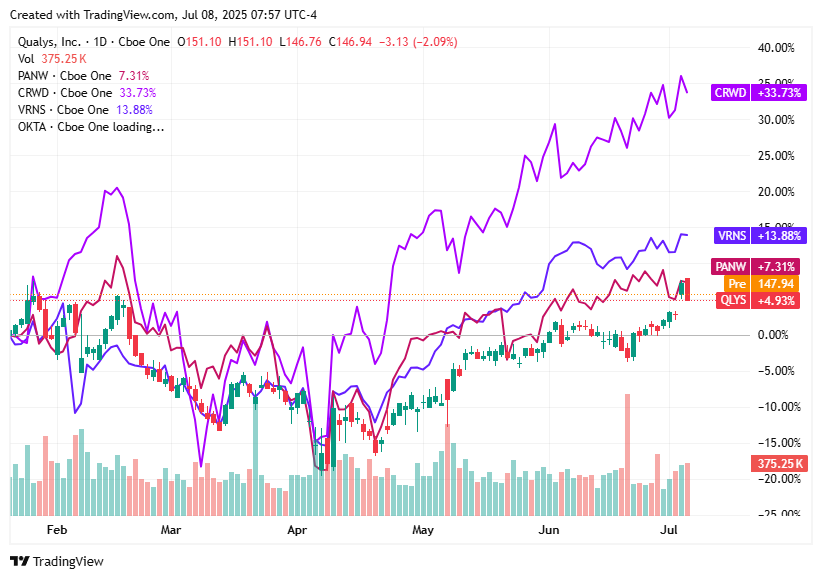
On Tuesday, July 8, 2025, cybersecurity stocks experienced modest declines as markets responded to fresh tariff announcements, shifts in geopolitical spending priorities, and continued reassessment of tech valuations.
Okta (OKTA) closed at $97.40, down 1.68%, as the broader tech sector came under pressure following newly announced tariffs by President Trump.
Varonis (VRNS) ended at $51.10, down 0.12%, reflecting cautious sentiment in mid-cap tech despite continued adoption of its AI-powered data security solutions.
CrowdStrike (CRWD) declined to $505.46, falling 1.68%, as investor enthusiasm cooled following a strong rally fueled by AI momentum and high valuation concerns.
Palo Alto Networks (PANW) finished at $201.42, down 0.21%, as investors weighed short-term market volatility against expectations of increased U.S. federal cybersecurity spending.
Qualys (QLYS) dropped to $146.94, down 2.07%, with concerns over rising capital costs dampening investor appetite for compliance-focused security solutions amid tariff-driven uncertainty.
💡 Cyber Tip
Malware Alert as NordDragonScan Compromises Windows Files and Browsers
Security researchers have identified a new infostealer called NordDragonScan targeting Microsoft Windows users. The attack starts with a malicious shortcut file inside a decoy archive, triggering an HTA script that quietly deploys the malware. Once installed, it steals browser data, system information, and documents, and then sends the stolen data to a remote command-and-control server. The malware also establishes persistence to survive system reboots and uses obfuscation to avoid detection.
✅ What you should do:
Avoid opening shortcut files (.lnk) or archives from unknown sources, especially if delivered via shortened URLs.
Disable or restrict the use of mshta.exe in your environment if not needed.
Monitor registry paths like CurrentVersion\Run for unfamiliar entries.
Use endpoint detection tools that can flag obfuscated payloads and unusual script behavior.
Train staff to recognize suspicious downloads and document-themed phishing lures.
🔒 Why this matters:
NordDragonScan uses stealthy tactics and decoy documents to steal sensitive data from Windows systems. Its ability to persist and exfiltrate browser and system data makes it a serious threat to both personal and corporate environments. Early detection and caution with unknown files are key to staying protected.
📚 Cyber Book
Speaking Their Language: The Non-Techie’s Guide to Managing IT & Cybersecurity for Your Organization by Rob Protzman
That concludes today’s briefing . You can check the top headlines here!
Copyright © 2025 CyberMaterial. All Rights Reserved.
Follow CyberMaterial on:
Substack, LinkedIn, Twitter, Reddit, Instagram, Facebook, YouTube, and Medium.