Cyber Briefing: 2025.06.30
Bluetooth flaw enables spying via headsets, Scattered Spider targets airlines, fake software spreads malware, ransomware hits Horizon Healthcare, school cyberattack shuts down UK classes.
👉 What's happening in cybersecurity today?
Welcome to Cyber Briefing, the newsletter that informs you about the latest cybersecurity advisories, alerts, incidents and news every weekday.
First time seeing this? Please Subscribe
🚨 Cyber Alerts
1. Bluetooth Flaw Lets Hackers Spy On You
Security researchers discovered critical vulnerabilities in a widely used Airoha Bluetooth chipset affecting numerous popular audio devices. The flaws impact dozens of headphones and speakers from major brands including Sony, Bose, and Marshall. An attacker within Bluetooth range can potentially exploit the issues to eavesdrop through a microphone or steal a user's contacts and call history. Although the chip manufacturer created a fix, device makers have not yet released the necessary firmware updates to the public.
2. Scattered Spider Hackers Target Airlines
The FBI has warned that the cybercrime group known as Scattered Spider is now actively targeting the airline industry. This group uses advanced social engineering techniques to impersonate employees, tricking IT help desks into granting them access to secure systems. The hackers often target high-value C-suite accounts to steal sensitive data, extort the company, and deploy ransomware. In response, security experts are urging aviation companies to immediately strengthen their internal identity verification processes to prevent these attacks.
3. Hackers Use Fake Software To Spread Malware
A Chinese hacking group known as Silver Fox is distributing malware through fake websites that advertise popular software. The campaign delivers the Sainbox remote access trojan and the open-source Hidden rootkit to unsuspecting victims. These attacks primarily target Chinese-speaking users with malicious installers designed to look like legitimate software. This method provides the attackers with stealth and system control without requiring significant custom malware development.
For more alerts, click here!
💥 Cyber Incidents
4. Data Breach at Horizon Healthcare RCM
Horizon Healthcare RCM, a revenue cycle management firm, suffered a ransomware attack and data breach in late December. The attack exposed a wide range of patient information, including health insurance data and, in some cases, Social Security numbers and financial details. The company's public notice was transparent about the ransomware and strongly implied that it paid a demand to have the stolen data deleted. However, the total number of affected patients and which of its many healthcare partners were impacted remains unknown.
5. Compumedics Breach Hits 10 Health Clients
The sleep disorder diagnostic vendor Compumedics suffered a data breach that exposed patient data from Northern Light Health. The breach occurred between February and March 2025 and compromised files containing names, medical records, and sleep study results. While a subset of patients may have had Social Security numbers exposed, Northern Light Health believes its patients' financial and insurance data were not involved. Compumedics has since enhanced its security, and all individuals who were affected by the incident have been notified by mail.
6. Cyberattack Closes Richard Lander School
Richard Lander School in Cornwall, England, closed for two days due to a major cybersecurity incident affecting its IT systems. The school has very limited access to its data, which impacts its ability to function and properly safeguard its students. While an investigation into the incident is ongoing, officials have stated there is no evidence of a personal data compromise. The school administration will provide an update to parents on Tuesday regarding the operational plans for the rest of the week.
For more incidents, click here!
📢 Cyber News
7.NATO Deal Boosts Cyber Defense Spending
NATO allies have agreed to increase their defense spending to a new target of five percent of GDP within a decade. The goal includes 3.5 percent for core defense and 1.5 percent for indirect spending like cybersecurity capabilities. This increase is seen as a direct response to decades of U.S. criticism about burden-sharing, largely amplified by President Trump. Despite the new agreement, some allies have already expressed reluctance to meet the target, and the rules for spending remain vague.
8. Unpatched Exploits Are Top Ransomware Threat
A new report found that exploited vulnerabilities are the top cause of ransomware attacks for the third straight year. While the average recovery cost for victims is $1.53 million, the report notes that data encryption rates have actually dropped. Key operational factors enabling these attacks include a lack of internal cybersecurity expertise and insufficient staffing capacity. The findings highlight the critical need for organizations to prioritize proactive vulnerability management to combat these ongoing threats.
9. Microsoft RIFT Tool Fights Rust Malware
Microsoft has released a new open-source tool called RIFT to combat the growing threat of Rust-based malware. The Rust language is being used to create complex malware that is much larger and harder to reverse engineer than traditional programs. RIFT helps analysts by automatically identifying library code in Rust binaries, allowing them to focus on the malicious logic. By releasing the tool on GitHub, Microsoft aims to equip the cybersecurity community to better defend against these evolving threats.
For more news, click here!
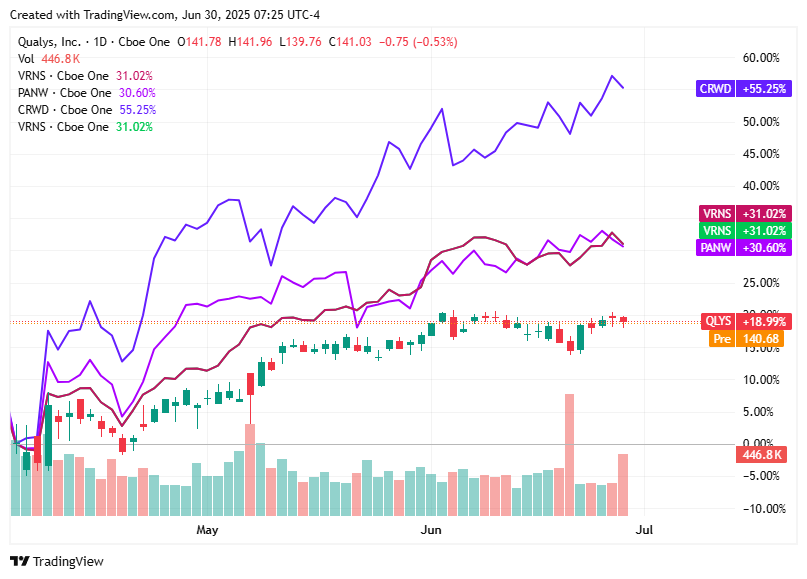
📈Cyber Stocks
Cybersecurity stocks showed restrained movement on Monday, June 30, 2025:
Okta closed at $98.43, up 0.38%, buoyed by optimism around its AI-driven identity roadmap and investor confidence following reduced institutional ownership that signaled strategic repositioning.
Varonis dropped to $50.26, down 1.36%, as rising U.S. interest rates triggered a broader tech-sector pullback, overshadowing momentum from its SaaS transition and AI product releases.
CrowdStrike slipped to $499.33, down 1.15%, after issuing a conservative Q2 revenue forecast citing reduced enterprise cybersecurity spending and geopolitical tariff pressures.
Palo Alto Networks declined to $200.57, down 0.86%, as investors paused following a strong AI-fueled rally, weighing valuation concerns against potential federal contract gains.
Qualys fell to $141.03, down 0.49%, driven by cautious investor behavior amid rising interest rates and reduced short-term appetite for mid-cap cybersecurity stocks despite stable service demand.
💡 Cyber Tip
Stay Alert as Bluetooth Flaw Lets Hackers Spy on Your Calls and Data
Security researchers have uncovered serious vulnerabilities in Airoha Bluetooth chipsets used in popular headphones and speakers from brands like Sony, Bose, and Marshall. These flaws allow attackers within Bluetooth range to bypass authentication, access device memory, steal contacts and call history, and even activate microphones to eavesdrop, all without user interaction. Although the chipmaker has issued a fix, many audio device manufacturers have not yet released firmware updates to users.
✅ What you should do:
Check your device manufacturer’s website for the latest firmware updates and apply them as soon as they’re available.
Avoid using Bluetooth audio devices in sensitive environments until updates are confirmed.
Unpair unused or unfamiliar Bluetooth devices from your phone or computer.
Keep your phone’s Bluetooth turned off when not in use to reduce exposure.
Use headphones with wired connections when privacy is a concern.
🔒 Why this matters:
These vulnerabilities turn everyday audio devices into potential surveillance tools. Even though attacks require close range and a high level of skill, the threat is real, especially for high-value targets. Staying updated and limiting Bluetooth exposure is essential for protecting your privacy.
📚 Cyber Book
A Short & Happy Guide to Privacy and Cybersecurity Law by Jon Garon
That concludes today’s briefing . You can check the top headlines here!
Copyright © 2025 CyberMaterial. All Rights Reserved.
Follow CyberMaterial on:
Substack, LinkedIn, Twitter, Reddit, Instagram, Facebook, YouTube, and Medium.