Cyber Briefing: 2025.06.25
FileFix tricks users via Explorer, OneClik hits energy firms, Trezor users phished, Columbia faces IT outage, ransomware hits Porto and Mainline, US cyber law nears expiry, G7 backs cyber fund.
👉 What's trending in cybersecurity today?
Welcome to Cyber Briefing, the newsletter that informs you about the latest cybersecurity advisories, alerts, incidents and news every weekday.
First time seeing this? Please Subscribe
🚨 Cyber Alerts
1. FileFix Attack Turns Explorer Into Weapon
A new social engineering technique called "FileFix" has been developed as a dangerous evolution of the "ClickFix" attack method. Discovered by a security researcher, the attack tricks users into running malicious commands through the Windows File Explorer address bar instead of a more suspicious command prompt. The method uses a phishing page and a clever copy-paste trick where a malicious PowerShell command is hidden behind a fake file path. This technique is particularly concerning as it exploits a familiar user interface and can bypass security training focused on traditional attack vectors.
2. OneClik Malware Attacks Energy Sector Firms
A sophisticated malware campaign dubbed “OneClik” is targeting the energy, oil, and gas sectors with advanced, stealthy attacks. Researchers at Trellix discovered the campaign, which abuses Microsoft's ClickOnce technology and legitimate cloud services like AWS to bypass security controls. The infection chain typically begins with a spearphishing email that tricks victims into installing a backdoor called "RunnerBeacon." While not definitively attributed, the tactics and techniques used in the campaign share overlaps with known China-linked threat actors.
3. Hackers Abuse Trezor Support For Phishing
Hardware wallet maker Trezor is warning users of a phishing campaign that abuses its own automated support system. Attackers are creating support tickets with alarming titles, which the system then automatically emails to users from an official Trezor email address. These legitimate-looking emails contain malicious links that lead to phishing sites designed to steal a user's wallet recovery seed phrase. This incident follows several previous security breaches and phishing campaigns that have targeted Trezor users over the past few years.
For more alerts, click here!
💥 Cyber Incidents
4. Columbia University Probes Major IT Outage
Columbia University's online platforms were knocked offline for hours yesterday morning, prompting an investigation with the New York Police Department. The widespread outage blocked student and staff access to essential services like email and the CourseWorks platform that professors use for assignments. While IT teams worked to restore services, a separate mystery unfolded as screens across campus began displaying bizarre images. University officials stated they could not definitively connect the strange images to the system outage and have discredited online posts from a group that had initially claimed responsibility.
5. Mainline Health Breach Hits 101,000 Patients
Arkansas-based Mainline Health Systems has begun notifying over 101,000 people that their personal data was stolen in a breach. The company determined last month that an unauthorized party had acquired sensitive information during a security incident that occurred back in April 2024. The exposed data includes a wide range of personal and protected health information, such as Social Security numbers, medical diagnoses, and financial details. The "Inc Ransom" ransomware group took credit for the attack in May 2024 as part of a broader campaign against the U.S. healthcare sector.
6. Porto Nacional City Hall Hit by Ransomware
The City Hall of Porto Nacional, Brazil, was hit by a ransomware attack that temporarily disrupted its internal systems and internet access. According to city officials, the attackers threatened to disclose personal data but were unable to copy or steal any files. The city's technical team stated that the large volume of data, approximately 20 terabytes, made theft unfeasible and that no taxpayer or server data was compromised. Thanks to a daily backup system, the city is restoring all its services and will file a police report to investigate the crime.
For more incidents, click here!
📢 Cyber News
7. US Cyber Sharing Law Nears Expiration
A crucial U.S. cybersecurity law that underpins information sharing between the public and private sectors is set to expire on September 30th. With very few legislative days left on the calendar, analysts fear Congress may fail to renew the law or rush through a renewal without needed improvements. The Cybersecurity Information Sharing Act of 2015 (CISA 2015) has broad bipartisan support, but experts argue it is outdated and needs to be modernized to address current threats like AI manipulation. If the law lapses, it could severely damage the government's visibility into threats against critical infrastructure and force many companies to stop sharing vital cyber threat data altogether.
8. G7 Backs New Global Cybersecurity Fund
A new Common Good Cyber Fund has been launched to support non-profit organizations that provide core cybersecurity services for the public. The first-of-its-kind effort aims to strengthen global cybersecurity, particularly for those most at risk, including journalists and human rights defenders. The governments of the United Kingdom and Canada have announced they will be the first to invest in the fund, with all G7 leaders also pledging their support. The fund will be managed by the Internet Society and will support services like securing core digital infrastructure and providing cybersecurity assistance to high-risk groups.
9. New Defensive Methods Stop Crypto Botnets
Cybersecurity researchers at Akamai have developed two new techniques designed to actively disrupt and shut down malicious cryptocurrency mining botnets. The first method, called "bad shares," gets a botnet's central mining proxy banned by intentionally submitting invalid work to the mining pool. The second method overwhelms a mining pool with over a thousand simultaneous login requests, forcing the pool to temporarily ban the attacker's wallet address. These techniques allow defenders to disable malicious campaigns by exploiting the very policies and infrastructure the attackers rely upon.
For more news, click here!
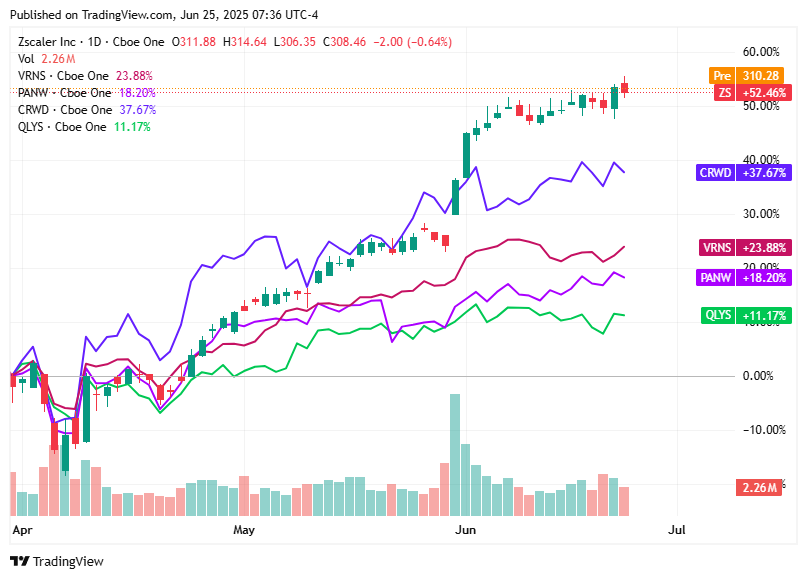
📈Cyber Stocks
On Wednesday, June 25, 2025, as trading gets underway in the U.S., economic and geopolitical developments are influencing market sentiment. A tentative Israel‑Iran ceasefire has helped ease oil prices and boost investor risk appetite, while weaker consumer confidence and cautious signals from the Fed are putting pressure on tech stocks. Here are the latest readings on five pure-play cybersecurity companies:
Zscaler (ZS): Trading at $308.46, down 0.66%. The stock eased slightly following recent gains, though long-term demand for its Zero Trust and SASE technologies remains strong.
Varonis (VRNS): Trading at $50.11, up 1.33%. Investor interest remains steady, driven by its data-centric security platform and growing enterprise focus on cyber risk.
Palo Alto Networks (PANW): Trading at $201.69, down 0.83%. The stock holds above $200, with continued adoption of its AI-powered security tools supporting the long-term outlook.
CrowdStrike (CRWD): Trading at $485.38, down 1.34%. The slight dip reflects broader tech softness, though demand for its cloud-native endpoint security remains strong.
Qualys (QLYS): Trading at $140.00, down 0.27%. Minor pullback today, but fundamentals and technical strength remain intact following robust Q1 performance.
💡 Cyber Tip
Stay Alert as Social Engineering Turns File Explorer Into a Malware Trap
A newly discovered social engineering technique called FileFix tricks users into running malicious PowerShell commands through the Windows File Explorer address bar. Disguised as a normal file path, the command is copied from a phishing page and executed when pasted, bypassing traditional security awareness focused on Run Dialog or Command Prompt abuse. This method relies on visual deception and exploits the trust users place in everyday interfaces.
✅ What you should do:
Never paste unknown paths or commands into the File Explorer address bar, especially from websites or unsolicited messages.
Train employees to recognize copy-paste based phishing tactics and to verify suspicious file-sharing requests.
Use endpoint protection tools that monitor command execution from non-standard interfaces like Explorer.
Enable security logging to detect unusual PowerShell activity or unexpected browser-child process chains.
Update security awareness training to include Explorer-based execution risks like FileFix.
🔒 Why this matters:
FileFix shows that attackers are now turning trusted system features like File Explorer into tools for malware delivery. Because the command appears harmless or invisible to users, even well-trained individuals can be tricked. Awareness of these new attack surfaces is essential to staying protected.
📚 Cyber Book
Cybersecurity Law: Protect Yourself and Your Customers by Shimon Brathwaite
That concludes today’s briefing . You can check the top headlines here!
Copyright © 2025 CyberMaterial. All Rights Reserved.
Follow CyberMaterial on:
Substack, LinkedIn, Twitter, Reddit, Instagram, Facebook, YouTube, and Medium.