Cyber Briefing: 2025.06.12
SmartAttack steals air-gapped data via sound, Tomcat and Entra ID face attacks, Erie Insurance and Philly schools breached, SoftBank leaks PII, Linux cloud malware surges, INTERPOL busts infostealers.
👉 What's going on in the cyber world today?
Welcome to Cyber Briefing, the newsletter that informs you about the latest cybersecurity advisories, alerts, incidents and news every weekday.
First time seeing this? Please Subscribe
🚨 Cyber Alerts
1. SmartAttack Uses Sound To Steal PC Data
Security researchers have demonstrated a new attack method called 'SmartAttack' that uses a smartwatch as a covert receiver to steal data from physically isolated, air-gapped computer systems. The technique requires malware on the target computer to encode sensitive information like encryption keys into inaudible ultrasonic audio signals broadcast from the system's built-in speakers. A nearby smartwatch, worn by an insider or previously compromised, can then use its microphone to capture these signals and demodulate the hidden data, which is then exfiltrated using the watch's Wi-Fi or cellular connection. Although the attack has limitations like low data transfer rates, it proves the viability of acoustic covert channels, prompting experts to recommend prohibiting smartwatches in high-security environments.
2. Coordinated Brute Force Hits Tomcat Manager
A significant and coordinated cyberattack campaign has targeted exposed Apache Tomcat Manager interfaces, with threat actors leveraging approximately 400 unique IP addresses in attacks that peaked on June 5th. Security firm GreyNoise identified two related attack vectors involving brute force and login attempts, with traffic reaching up to 20 times above normal levels and originating largely from DigitalOcean's cloud infrastructure. This sophisticated campaign showed a narrow focus on Tomcat services to minimize detection, with attackers likely using automated tools to coordinate the simultaneous attacks from hundreds of IPs. Organizations are urged to immediately block the identified malicious IPs, enforce strong authentication like MFA, restrict access to manager interfaces, and review logs for signs of compromise.
3. Pentest Tool TeamFiltration Hits Entra ID
A sophisticated account takeover campaign, tracked as UNK_SneakyStrike, is weaponizing a legitimate penetration testing framework called TeamFiltration to compromise Microsoft Entra ID environments globally. Since December 2024, attackers have used the tool to conduct password spraying and enumerate users, targeting over 80,000 accounts across approximately 100 different cloud tenants. Proofpoint researchers identified the malicious activity by fingerprinting the framework's distinctive and outdated Microsoft Teams user agent string and its targeting of specific OAuth application IDs. This campaign highlights how threat actors are increasingly abusing legitimate security tools, originally designed for defensive purposes, to steal data and establish persistent access in cloud environments.
For more alerts, click here!
💥 Cyber Incidents
4. Erie Insurance Cyberattack Halts Operations
Major U.S. insurer Erie Insurance has disclosed a cyberattack discovered on Saturday, June 7th, that forced it to take some systems offline and caused widespread business disruptions. The incident has impacted the Fortune 500 company's ability to fulfill and distribute customer orders, with customers unable to log into the online portal or easily make claims. Erie has activated its incident response plan, notified law enforcement, and engaged external cybersecurity experts to investigate the breach, which is still in its early stages. While the full nature of the attack is unknown, the company has warned customers it will not solicit payments during the outage, indicating concern about follow-on phishing scams.
5. Physical Breach At SoftBank Vendor Leaks PII
Japanese telecommunications giant SoftBank has announced that personal information of over 137,000 mobile subscribers may have been leaked from one of its subcontracted companies in Japan, "UF Japan." The breach was reportedly caused by a physical security failure where a former employee of another subcontractor illegally entered the office due to sloppy access management and took the sensitive personal information. Exposed data could include the names, addresses, and phone numbers of SoftBank and Ymobile subscribers but does not contain financial information like credit card or bank account numbers. In response, SoftBank has terminated its contract with the vendor, is consulting with police, and has pledged to strengthen its management of all subcontractors who handle personal data.
6. DragonForce Ransomware Hits Philly Schools
Mastery Schools, the largest charter school network in Philadelphia, has confirmed it is notifying 37,031 people of a September 2024 ransomware attack that compromised their personal data. The incident, which initially caused IT outages affecting phones and email, exposed sensitive information including names, Social Security numbers, medical details, and student records. The DragonForce ransomware gang claimed responsibility for the attack, stating on its leak site that it stole 171 GB of data, although Mastery has not publicly verified this claim. In response, the school network is now offering eligible victims free identity theft protection services through Experian and has warned them to be vigilant for potential fraud.
For more incidents, click here!
📢 Cyber News
7. New Bill Aims To Secure US Healthcare Data
U.S. Representatives Jason Crow and Brian Fitzpatrick have introduced a new bipartisan Healthcare Cybersecurity Bill to Congress to expand the federal government's role in protecting Americans' medical data. Prompted by massive incidents like the Change Healthcare attack which impacted 190 million people, the bill mandates collaboration between the Cybersecurity and Infrastructure Security Agency (CISA) and the Department of Health and Human Services (HHS). This partnership will involve sharing cyber threat intelligence, providing CISA-led training for healthcare organizations, and creating a healthcare-specific risk management plan to protect critical systems. The bill aims not just to respond to attacks but to build the infrastructure to prevent them, protect patient privacy, and defend what lawmakers call a vital pillar of national security.
8. Operation Secure Busts Infostealer Ring
INTERPOL announced that a multinational law enforcement action, codenamed "Operation Secure," has dismantled over 20,000 malicious domains and IP addresses linked to 69 infostealer malware variants. Conducted across 26 countries between January and April 2025, the coordinated operation resulted in 32 arrests and the seizure of 41 servers supporting the malware infrastructure. Private partners like Group-IB provided critical intelligence that helped disrupt infrastructure tied to prominent infostealers such as Lumma, RisePro, and META Stealer. This takedown is the latest in a series of global efforts, like Operation Endgame, aimed at dismantling the cybercrime-a-as-a-service ecosystem that uses stolen data to enable ransomware and financial fraud.
9. Linux Malware Cloud Attacks Surge 388%
A new wave of sophisticated Linux malware is increasingly targeting cloud computing environments, causing security alerts to surge by an astonishing 388 percent in 2024. Palo Alto Networks analysts have identified five primary malware families in these campaigns, which use backdoors, RATs, and wipers adapted to exploit cloud-specific vulnerabilities. A concerning tactic is the use of advanced persistence mechanisms like dynamic linker hijacking, where the malware abuses the LD_PRELOAD variable to hook into critical Linux services like the SSH daemon.
For more news, click here!
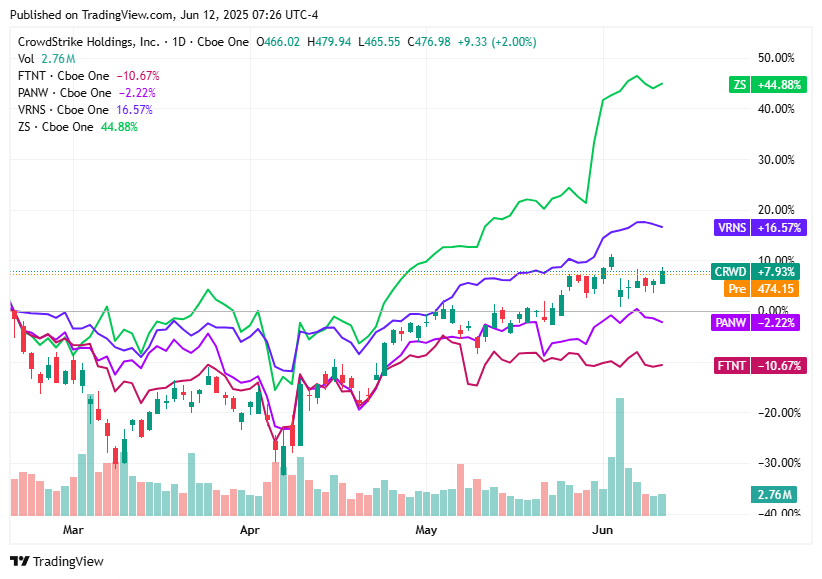
📈Cyber Stocks
As U.S. markets open on Thursday, June 12, 2025, leading cybersecurity stocks are showing mixed activity amid insider moves, analyst signals, and broader tech-market dynamics:
Zscaler (ZS): Trading at $299.86, up 0.63%. Despite recent insider sales totaling ~$36M by key stakeholders, analysts remain bullish citing strong Cloud‑Zero Trust momentum and price targets raised toward $350+ .
Varonis (VRNS): Trading at $50.23, down 0.46%. Investor interest in data-centric cybersecurity remains steady, with shares holding within a narrow range.
Palo Alto Networks (PANW): Trading at $194.39, down 0.80%. Stocks are consolidating after recent gains, yet the company’s AI-enhanced security offerings continue to support its long-term growth narrative.
CrowdStrike (CRWD): Trading at $476.98, up 1.99%. The stock rallies after last week’s dip, as analysts including Wedbush, UBS, and Bank of America reaffirm buy ratings with targets ranging from $500 to $545 .
Fortinet (FTNT): Trading at $102.02, up 0.42%. Investor confidence holds firm, backed by robust revenue growth and a $1B buyback program.
💡 Cyber Tip
Keep Smartwatches Away from Secure Computers
Researchers have discovered a new method called "SmartAttack" that uses a smartwatch to secretly receive data from air-gapped (offline) computers through inaudible sound. Malware on the computer turns sensitive data into ultrasonic signals that nearby smartwatches can record and send out over Wi-Fi or mobile networks.
✅ What you should do
Do not wear smartwatches or other recording-capable wearables near high-security or sensitive systems.
In extremely secure environments, disable or remove built-in speakers from air-gapped machines.
Consider using ultrasonic jamming or sound-isolating techniques to prevent hidden audio signals from being transmitted.
Educate staff on the risks of wearable tech in restricted or classified areas.
Regularly check and audit physical security policies and insider threat controls.
🔒 Why this matters
Even without internet access, isolated computers can leak data through hidden audio signals. Wearables like smartwatches may unknowingly help attackers exfiltrate that data.
📚 Cyber Book
Cybersecurity in Healthcare: A National Study of HIPAA Implementation by Dr. Mansur Hasib
That concludes today’s briefing . You can check the top headlines here!
Copyright © 2025 CyberMaterial. All Rights Reserved.
Follow CyberMaterial on:
Substack, LinkedIn, Twitter, Reddit, Instagram, Facebook, YouTube, and Medium.