Cyber Briefing: 2025.06.09
npm and PyPI malware steal data and wipe files, SOQL flaw exposes Salesforce records, and HelloTDS uses fake CAPTCHAs. Chaos gang hits Optima, Sorbonne breached, Brazil city health systems shut down.
👉 What are the latest cybersecurity alerts, incidents, and news?
Welcome to Cyber Briefing, the newsletter that informs you about the latest cybersecurity advisories, alerts, incidents and news every weekday.
First time seeing this? Please Subscribe
🚨 Cyber Alerts
1. Sabotage Theft Malware On npm And PyPI
Cybersecurity researchers have uncovered a new supply chain attack where malicious code was injected into over a dozen packages related to GlueStack, delivering a remote access trojan to users. In a separate incident on npm, two rogue packages were discovered that act as destructive wipers, designed to delete entire application directories in an unusual case of sabotage rather than for financial gain. Concurrently, a new Python-based credential harvester on the PyPI repository, posing as an Instagram growth tool, has been found to steal user logins and broadcast them to multiple bot services.
2. Salesforce SOQL Flaw Exposed User Records
A critical zero-day vulnerability was discovered in a default Salesforce Aura controller, allowing attackers to extract sensitive user and document details via Salesforce Object Query Language (SOQL) injection techniques. Security researcher Tobia Righi found that the flaw, affecting thousands of deployments by default, could be exploited using error-based blind injection to enumerate database information. After being notified of the issue in late February 2025, Salesforce quietly patched the widespread vulnerability without issuing a public advisory, CVE number, or release notes. This silent patching approach has left the security community without official guidance on detection methods or indicators of compromise, making it difficult for organizations to assess if they were previously breached.
3. HelloTDS Spreads Malware Via Fake CAPTCHAs
Cybersecurity researchers have uncovered a complex Traffic Direction System dubbed "HelloTDS" that orchestrated the delivery of malware to over 4.3 million devices in April and May 2025 alone. This system uses advanced fingerprinting on users visiting compromised websites to selectively redirect suitable targets to malicious landing pages, most often deceptive FakeCaptcha verification screens. The FakeCaptcha pages then trick victims into executing harmful commands which initiate a multi-stage attack that ultimately installs infostealers like LummaC2 or remote access trojans. The campaign's ability to serve benign content to evade researchers and dynamically rotate its infrastructure highlights a sophisticated threat that exploits user trust in familiar CAPTCHA interfaces.
For more alerts, click here!
💥 Cyber Incidents
4. Chaos Gang Leaks Optima Tax Client Data
U.S. tax resolution firm Optima Tax Relief has been hit by the Chaos ransomware gang, who on June 6th claimed to have stolen 69 GB of data and added the company to its data leak site. This double-extortion attack involved both data theft and server encryption, with the stolen information including sensitive customer case files containing personal details like Social Security numbers. The Chaos ransomware gang, which emerged in March 2025 and should not be confused with the older Chaos ransomware builder, has also recently claimed an attack on the Salvation Army. As of the report, Optima Tax Relief had not yet issued an official statement regarding the incident or formally notified its affected customers and relevant authorities about the breach.
5. Sorbonne University Hit By Staff Data Breach
Sorbonne University in France has been hit by a cyberattack that caused major disruptions to its information systems and resulted in a sensitive data breach. An investigation with external cybersecurity experts revealed that compromised data includes staff professional email addresses, banking information, Social Security numbers, and compensation details. Following GDPR protocols, the university has notified French data protection and cybersecurity authorities (CNIL and ANSSI) and filed a police complaint while working to restore all services. While essential digital services are functioning, Sorbonne University is establishing a toll-free number and FAQ to support affected staff, reaffirming its commitment to data protection.
6. Hack Shuts Down Brazil City Health Systems
The City Hall of São José do Rio Preto, Brazil, suffered a major cyberattack on Thursday, June 5th, which compromised all municipal administration systems and prompted an immediate shutdown. The city's IT provider, Empro, isolated the network and began restoring from backups while stating databases were not compromised, as cybercrime authorities launched an investigation. Healthcare services were severely affected, forcing emergency and basic health units to use manual processes that caused long queues and suspended non-urgent exams and some emergency phone lines. Empro highlighted that this attack managed to overcome their usual digital barriers, which typically block over a dozen attempts daily, underscoring the severity of this particular incident.
For more incidents, click here!
📢 Cyber News
7. New Trump Cyber EO Rolls Back Biden Rules
President Donald Trump signed a new executive order on Friday to amend cybersecurity policies from the Biden and Obama administrations, focusing on areas like software security, AI, and digital identity. The order immediately strikes a controversial section from a January 2025 Biden Executive Order that encouraged accepting digital IDs for public benefits, a move the White House claimed prevents fraud but which the Better Identity Coalition criticized. It also reverses Biden-era policies on AI defense collaboration and removes requirements for federal contractors to attest to their software's security, while simplifying the roadmap for post-quantum cryptography. Finally, the order amends an Obama-era sanctions policy, changing the target from "any person" to "any foreign person" to, according to the administration, prevent its use against domestic political opponents.
8. DOJ Seeks $7.74M From North Korean IT Scam
The U.S. Department of Justice has filed a civil forfeiture complaint to permanently claim over $7.74 million linked to an illicit North Korean IT worker scheme that generates revenue for the regime. These funds were connected to North Korean Foreign Trade Bank representative Sim Hyon Sop, who was indicted in 2023 for conspiring with IT workers to launder money obtained from their illegal employment at U.S. companies. The scheme involved laundering cryptocurrency obtained with stolen American identities through a complex network, with Sim and another official, Kim Sang Man, acting as central clearinghouses for the proceeds. This forfeiture action is part of the broader "DPRK RevGen" initiative, which aims to disrupt the financial networks that North Korea uses to fund its weapons programs by exploiting global IT work.
9. OpenAI Bans State Hackers From ChatGPT
OpenAI announced this week that it has taken down accounts linked to state-backed threat actors from China, Russia, North Korea, and Iran who were using ChatGPT for illicit purposes. The malicious activities included refining malware like the "ScopeCreep" RAT, researching U.S. defense technology, and bulk-generating social media posts for covert influence and disinformation campaigns. Notably, Chinese groups APT5 and APT15 used the models for reconnaissance, while North Korean operators used ChatGPT to generate fake resumes for their widespread IT worker employment scams. While OpenAI found no evidence that the actors gained novel capabilities from their models, the company's actions highlight the increasing trend of state-sponsored groups weaponizing large language models for cybercrime.
For more news, click here!
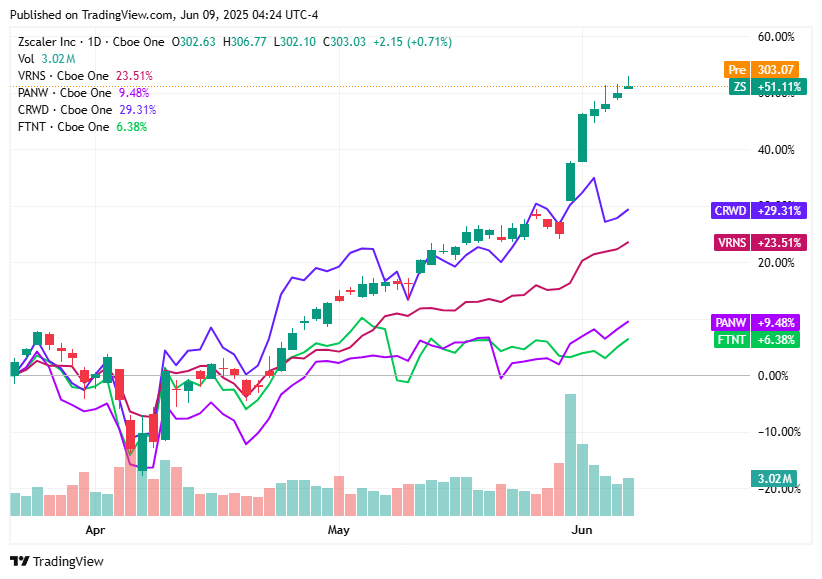
📈Cyber Stocks
As U.S. markets open on Monday, June 9, 2025, the following cybersecurity leaders are showing mixed performances amid evolving macro and sector trends:
Zscaler (ZS): Trading at $303.03, up 0.73%. The stock continues its upward trend, driven by strong demand for cloud security and Zero Trust architecture, with analysts remaining bullish.
Varonis (VRNS): Trading at $50.64, up 0.97%. Investor interest remains strong as the company’s focus on data protection aligns with rising enterprise security needs.
Palo Alto Networks (PANW): Trading at $199.60, up 1.21%. Momentum remains solid after surpassing $5B in annual recurring revenue for next-gen security offerings.
CrowdStrike (CRWD): Trading at $468.41, up 1.19%. Despite recent revenue guidance concerns, the stock is rebounding as analysts reaffirm long-term growth prospects.
Fortinet (FTNT): Trading at $104.94, up 1.35%. Gains reflect continued confidence following double-digit revenue growth and an expanded $1B stock buyback program.
💡 Cyber Tip
Be careful when installing software packages from npm or PyPI.
Cybersecurity researchers have found malicious code in open-source packages used by developers around the world. Some packages install remote access tools that let attackers take control of your device. Others delete files or steal social media passwords like Instagram, Facebook, and Gmail.
✅ What you should do
Only install packages from trusted, verified authors and check for recent security warnings before using them.
Review recent changes and updates in package repositories before downloading or updating software.
Avoid using tools that promise quick growth on social media as they are often scams or contain hidden malware.
Keep your development environment secure by using endpoint protection, limiting permissions, and backing up important files.
If you suspect a malicious package is installed, uninstall it immediately and run a full malware scan.
✅ Why this matters
Just one bad package from a public repository can allow hackers to steal your data, destroy your files, or hijack your system. Staying alert while installing software helps protect your work and your identity.
📚 Cyber Book
Fix Your Online Reputation: A Guide to Saving Your Brand Online by Gert Mellak
That concludes today’s briefing . You can check the top headlines here!
Copyright © 2025 CyberMaterial. All Rights Reserved.
Follow CyberMaterial on:
Substack, LinkedIn, Twitter, Reddit, Instagram, Facebook, YouTube, and Medium.