Cyber Briefing: 2025.06.04
Crocodilus trojan targets crypto users, fake CAPTCHAs spread NetSupport RAT, and rogue RubyGems steal Telegram tokens. BitoPro hacked, minister’s WhatsApp breached, and Chrome distrusts two CAs.
👉 What's trending in cybersecurity today?
Welcome to Cyber Briefing, the newsletter that informs you about the latest cybersecurity advisories, alerts, incidents and news every weekday.
First time seeing this? Please Subscribe
🚨 Cyber Alerts
1. Crocodilus Trojan Steals Crypto Globally
A recently discovered Android banking trojan named Crocodilus is rapidly expanding its global reach, now targeting users in Europe and South America with improved obfuscation techniques and new features. Initially documented in March 2025, the malware employs overlay attacks to steal financial credentials and abuses accessibility services to capture cryptocurrency wallet seed phrases. Recent campaigns use fake Facebook ads and disguise the malware as legitimate apps, while new variants can add fake contacts to victims' devices to bypass security alerts and automate seed phrase collection.
2. Bogus CAPTCHA Lures Install NetSupport RAT
Cybercriminals are exploiting fake "Prove You Are Human" CAPTCHA pages on spoofed websites mimicking platforms like Gitcodes and DocuSign to distribute the NetSupport Remote Access Trojan. This sophisticated campaign tricks users into copying and executing malicious PowerShell scripts via the Windows Run prompt, which initiates a multi-stage attack to install the RAT and achieve persistence. Tactics include clipboard poisoning on fake DocuSign pages and a multi-layered approach with repeated script executions to evade detection while communicating with command-and-control servers. While attribution is unclear, patterns suggest links to known threat groups, highlighting the need for user vigilance as legitimate sites rarely demand script execution from users.
3. Fake RubyGems Steal Telegram Bot Tokens
Cybersecurity researchers have discovered two malicious RubyGems packages, typosquatting legitimate Fastlane CI/CD plugins, designed to redirect Telegram API requests and steal sensitive data. These packages, still live on RubyGems under names like fastlane-plugin-telegram-proxy, appear nearly identical to the genuine plugin but reroute traffic through an attacker-controlled proxy to intercept bot tokens, chat IDs, messages, and files. This supply chain attack leverages trust in popular developer tools, as Fastlane is widely used for mobile app automation, and its Telegram integration provides real-time CI/CD updates. Developers who installed these malicious gems are urged to remove them immediately, rebuild any affected mobile binaries, rotate all compromised Telegram bot tokens, and consider blocking traffic to the attacker's proxy domain.
For more alerts, click here!
💥 Cyber Incidents
4. BitoPro Loses $11.5M In DeFi Hack Wave
Taiwan-based cryptocurrency exchange BitoPro confirmed it suffered a security breach on May 8th, resulting in the loss of over $11.5 million in digital assets from its hot wallets across multiple blockchains. Despite the incident and user withdrawal issues, the exchange only publicly acknowledged the exploit via a Telegram post on June 2nd, weeks after onchain investigators highlighted suspicious outflows that were moved to mixers like Tornado Cash. BitoPro stated the breach occurred during a wallet system upgrade when an old hot wallet was compromised, but assured users that reserves are sufficient and all other functions remain operational while a third-party investigates.
5. MainStreet Bank Faces Vendor Data Breach
MainStreet Bank recently disclosed a vendor cyberattack from March that exposed personal information of about 5% of its customers, though its own systems and financial data were not compromised. This disclosure coincides with five major banking associations demanding the Securities and Exchange Commission rescind its new cyber incident reporting rule, arguing it forces premature and harmful public revelations. The associations claim hackers now leverage this rule as an extortion tactic and that confusion over what constitutes a "material" incident leads to inconsistent and unhelpful market disclosures. While MainStreet Bank stated its incident had no material operational impact, its filing underscores the ongoing debate surrounding the SEC rule's effectiveness and alleged negative consequences for companies.
6. Malaysia Home Minister WhatsApp Breached
Malaysia’s Home Minister, Datuk Seri Saifuddin Nasution Ismail, had his WhatsApp account hacked, with attackers reportedly using a VPN to send malicious links to his contacts, police announced recently. Although no financial losses have been reported so far from this specific incident, the Ministry of Home Affairs confirmed the breach, urged public caution, and an investigation is underway to locate the hacker. This event follows similar cyberattacks on other high-ranking Malaysian officials, including the parliamentary speaker and a former Prime Minister, highlighting ongoing vulnerabilities. The hacking of the nation's top security official has drawn online criticism, with citizens questioning the strength of Malaysia’s overall cybersecurity measures.
For more incidents, click here!
📢 Cyber News
7. Romanian Swatter Guilty For US Leader Hoaxes
Romanian national Thomas Szabo pleaded guilty on Monday to leading an extensive swatting and bomb threat campaign that targeted dozens of high-ranking U.S. officials from late 2023 through early 2024. His victims included members of Congress, cabinet officials, senior law enforcement heads like CISA Director Jen Easterly, members of the federal judiciary, and even a former U.S. president. Szabo, who encouraged his swatting group and had previously threatened then President-elect Biden, was extradited from Romania and charged alongside Serbian national Nemanja Radovanovic for the widespread hoaxes. Now facing a maximum of 15 years in prison for conspiracy and threats involving explosives, Szabo will be sentenced on October 23rd, while charges against Radovanovic remain pending.
8. Germany Fines Vodafone $51M For Data Flaws
German data privacy regulators have fined Vodafone $51.2 million (€45M) for "malicious behavior" by third-party sales agents who arranged fraudulent deals and for security flaws in its customer authentication processes. These vulnerabilities allowed unauthorized access to sensitive eSIM profiles, while Vodafone was also penalized for inadequately monitoring its partner agencies under GDPR. Vodafone acknowledged its systems were insufficient, regretted the customer impact, and stated data protection is now a top priority with revised processes and strengthened protections. This significant fine comes as EU regulators increase GDPR enforcement, with Germany's commissioner stressing that data protection builds trust and can offer a competitive advantage.
9. Chrome To Distrust Two More CA Certificates
Google announced its Chrome browser will no longer trust new Transport Layer Security server authentication certificates issued by Chunghwa Telecom and Netlock after July 31, 2025, citing "patterns of concerning behavior" and compliance failures. This change, effective with Chrome 139 in August 2025, will cause security warnings for users visiting sites with newly issued certificates from these two Certificate Authorities. Website operators relying on these CAs are urged to transition to new publicly trusted certificate providers to avoid user disruption, although enterprises can override this by locally trusting the roots. This move follows similar industry actions against other CAs like Entrust and Apple's earlier distrust of a NetLock certificate, reflecting ongoing efforts to ensure web ecosystem integrity.
For more news, click here!
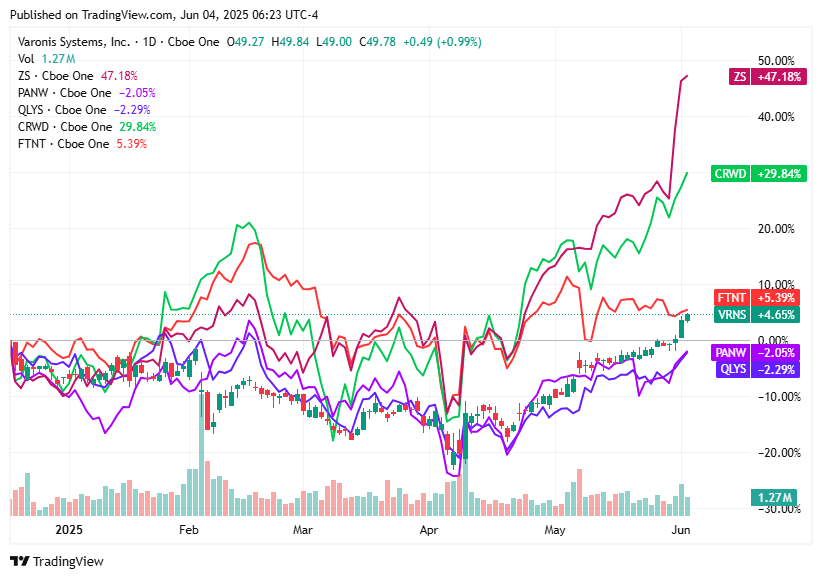
📈Cyber Stocks
As the U.S. stock market kicks off on Wednesday, June 4, 2025, leading cybersecurity stocks are showing notable activity, driven by robust earnings reports, strategic AI collaborations, and continued investor optimism.
Zscaler (ZS): Trading at $295.03, up 60% year-to-date, buoyed by strong Q3 results and a new AI partnership with Vectra.
Varonis (VRNS): Currently at $49.78, showing rising momentum and an improving strength rating.
Palo Alto Networks (PANW): Shares at $197.12, up 23% in the past month, following strong earnings and a bullish analyst outlook.
Qualys (QLYS): Trading at $142.56, exhibiting a bullish double-bottom pattern with a strength rating climbing to 72.
CrowdStrike (CRWD): At $488.76, the stock has recovered from the July 2024 bug, showing strong fundamentals and a 40% increase since.
Fortinet (FTNT): Priced at $102.88, boosted by 13% revenue growth and a $1B stock buyback expansion.
💡 Cyber Tip
Never copy and run scripts from websites that ask you to prove you're human.
Cybercriminals are using fake CAPTCHA pages that look like security checks to trick users into copying dangerous PowerShell commands. These commands secretly install a remote access tool called NetSupport RAT, which allows attackers to control your computer.
✅ What you should do
Do not trust websites that ask you to run scripts or commands as part of a CAPTCHA or verification process.
Always double-check the website’s URL and make sure it’s the official site before interacting.
Never paste unknown text into your Run prompt (Win+R), terminal, or PowerShell.
Keep your antivirus software updated and monitor your system for unusual behavior.
If you accidentally run a suspicious script, disconnect from the internet and contact your IT or security team immediately.
✅ Why this matters
Fake CAPTCHA pages are being used to install malware that can steal data, control your computer, or let attackers spy on your activity. Being cautious online can prevent serious damage.
📚 Cyber Book
The Small Business Social Media Cyber Security Guide by Jay Parisi
That concludes today’s briefing . You can check the top headlines here!
Copyright © 2025 CyberMaterial. All Rights Reserved.
Follow CyberMaterial on:
Substack, LinkedIn, Twitter, Reddit, Instagram, Facebook, YouTube, and Medium.